
- 280 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
Android Security: Attacks and Defenses is for anyone interested in learning about the strengths and weaknesses of the Android platform from a security perspective. Starting with an introduction to Android OS architecture and application programming, it will help readers get up to speed on the basics of the Android platform and its security issues.E
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Introduction
In this chapter, we introduce the reader to the mobile devices landscape and demonstrate why Android security matters. We analyze the evolution of mobile security threats, from basic phones to smartphones (including ones running the Android platform). We move on to introduce Android history, releases, and marketplaces for Android applications.
1.1 Why Android
The number of mobile and Internet users on mobile devices has been skyrocketing. If statistics are any indication, the adoption of mobile devices in emerging and advanced economies has just started and is slated for huge growth in the next decade (see Figure 1.1).
According to data available through Wikipedia (see Figures 1.2 and 1.3), the Android platform runs on 64% of smartphones and on about 23.5% of all phones (http://en.wikipedia.org/wiki/Mobile_operating_system). Approximately 37% of all phones today are smartphones, leaving a whopping 60%+ of phones open to future adoption. Given that Android’s share of the smartphone market has been rising steadily, the Android platform is slated for similar growth in the near future. Emerging markets and advanced economies alike are slated for increased smartphone adoption, with Android at the heart of it. Even during the recent economic downturn, the number of smartphone users continued to increase steadily. Mobile devices will form the majority of Internet-accessing devices (dwarfing servers and personal computers [PCs]) in the near future.
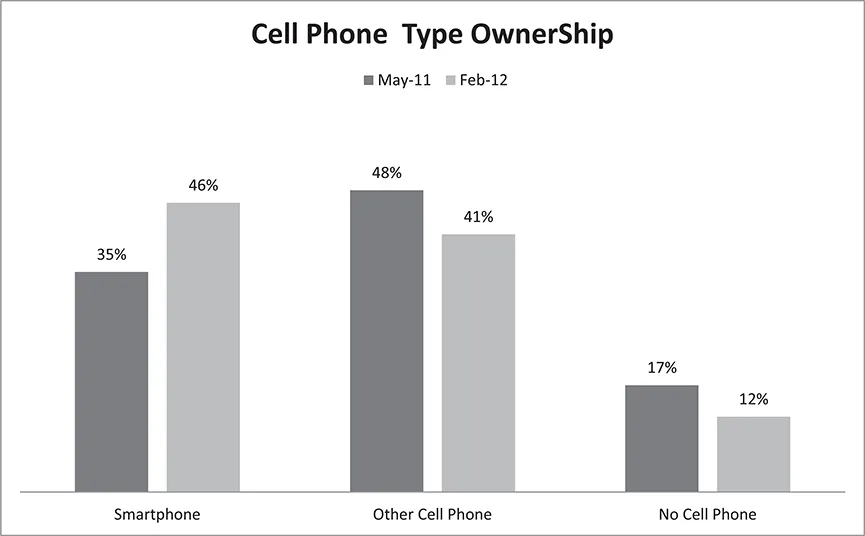
Figure 1.1 Basic vs. Smartphone Ownership in the United States

Figure 1.2 Global Smartphone Adoption (Source: http://en.wikipedia.org/wiki/Mobile_operating_system)
Until recently, smartphones were not “must-have” items and were considered only for tech-savvy or gadget geeks. The first Windows handheld devices (Windows CE) were introduced in 1996. The first true mobile smartphone arrived in the year 2000, when the Ericsson R380 was released, and it featured Nokia’s Symbian operating system. For awhile, there were cell phones and PDAs—separate devices (anyone remember iPaq?).
In 2002, both Microsoft and RIM released smartphones (Windows CE and Blackberry), respectively. While corporate adoption picked up after the release of the Blackberry, the end-user market really started picking up after the introduction of Apple’s iPhone, in 2007. By then, RIM had a majority share of the corporate market. Around the same time, Google decided to jump into the mobile device market. If mobile devices were going to represent most user activity in the future, it meant that users would be using them for searching the Internet—a core Google service. Advertising dollars would also be increasingly focused on mobile devices, as mobile devices allow for much more targeted ads. Searching “pizza” on a desktop/laptop can provide information about a user’s location through the IP address, among other information. However, with a cell phone, the user’s GPS location can be used to display “relevant ads” of places nearby.
The Open Handset Alliance (OHA) made its debut in 2007, and in 2008, Android was released.
The computational power of mobile devices has grown exponentially (see Figure 1.4). The HTC EVO 4G phone has the Qualcomm 8650 1 Ghz processor, 1 GB ROM (used for system software), and 512 MB of RAM. In addition, it has 802.11b/g, Bluetooth capability, an 8.0 MP camera, GPS, and HDMI output. The phone specifications are powerful enough to beat a desktop configuration for a typical user a few years ago. Again, this trend is likely to continue.

Figure 1.3 Global Smartphone Sales Q1 (Source: http://en.wikipedia.org/wiki/Mobile_operating_system)

Figure 1.4 Comparison of Apple iPhone, DroidX, and an Old PC
Android’s share of mobile devices has been increasing at a steady rate (see Figure 1.5). Android devices surpassed iPhone sales by 2011. By mid-2011, there were about half a million Android device activations per day (see Figure 1.6). Figure 1.7 shows the number of carriers as well as manufacturers that have turned to Android.
After the launch of the iPad, many manufacturers turned to Android as the platform for their offerings. The Samsung Galaxy Tab is a perfect example of this. Other manufacturers (e.g., Dell, Toshiba) have also started offering tablets with Android as their platform (see Figure 1.8). A trend is likely to continue wherein the tablet market uses two major platforms—IOS and Android.
1.2 Evolution of Mobile Threats
As mobile devices have evolved from basic to smartphones, threats to mobile devices have evolved in parallel. Smartphones have a larger attack surface compared to basic phones in the past. In addition, the usage patterns of mobile devices have also evolved. Basic phones were primarily used for text messaging and phone calls. Today smartphones are used for everything one can imagine using a computer for—performing routine banking transactions, logging onto Facebook, directions, maintaining health and exercise records, and so forth.

Figure 1.5 Mobile OS Market Share
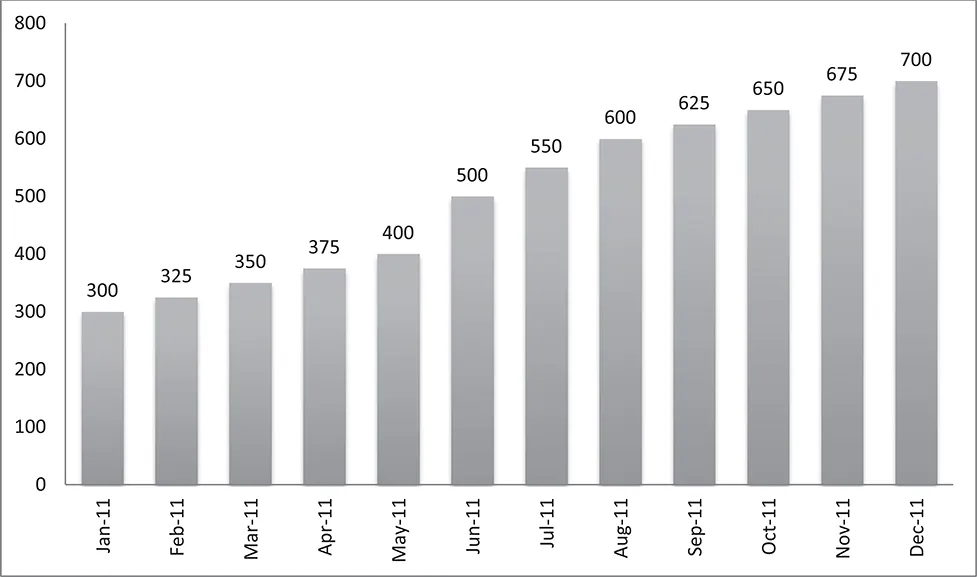
Figure 1.6 Number of Android Activations per Day (Jan. 11–Dec. 11)

Figure 1.7 Android Phones for Major Carriers
For a long time, Nokia’s Symbian OS was the primary target of attackers due to its penetration in the mobile market. As the market share of Symbian continues to decline and there is a corresponding increase in the share of Android devices and iPhones, attackers are targeting these platforms today.
Symbian is still the leading platform for phones outside the United States and will be a target of attackers in the foreseeable future. However, Android and iPhone attacks are increasing in number and sophistication. This reflects the fact that bad guys will always go after the most popular platform. As Android continues to gain in popularity, threats against it will continue to rise.

Figure 1.8 Android Devices from Major Manufacturers
Looking at the threat landscape for Android devices, it is clear that attacks against Android users and applications have increased quite a bit over the last couple of years. As Android adoption picks up, so does the focus of attackers to target the platform and its users. Android malware has seen an upward trend, as well.
This trend does not only apply to Android devices. Mobile phones have increased in their functionality as well as attack surfaces. The type of data we have on a typical smartphone and the things we do with our phone today are vastly different from just a few years ago.
Attacks on basic phones targeted Short Message Service (SMS), phone numbers, and limited data available to those devices. An example of such an attack is the targeting of premium SMS services. Attackers send text messages to premium rate numbers or make calls to these numbers. An attack on an Android or smart-phone is different and more sophisticated—for example, a malicious application accessing a user’s sensitive information (personal data, banking information, chat logs) and sending it to potential attackers. Smartphones are susceptible to a plethora of application-based attacks targeting sensitive information.
The following is a sample data set on a typical smartphone:
- Corporate and personal e-mails
- Contacts (along with their e-mail and personal addresses)
- Banking information
- Instant Messaging logs
- Pictures
- Videos
- Credit card Information
- Location and GPS data
- Health information
- Calendar and schedule information
Attacks on a smartphone running on the Android platform could result in leakage of the above data set. Some possible attacks that are more devastating include social engineering, phishing, spoofing, spyware, and malware—for example, a mobile application subscribing a user to a premium service. The user would then incur data and usage charges, in addition to subscription fees. Smartphone browsers are miniature compared to their desktop counterparts. Therefor...
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Dedication
- Table of Contents
- Foreword
- Preface
- About the Authors
- Acknowledgments
- Chapter 1 Introduction
- Chapter 2 Android Architecture
- Chapter 3 Android Application Architecture
- Chapter 4 Android (in)Security
- Chapter 5 Pen Testing Android
- Chapter 6 Reverse Engineering Android Applications
- Chapter 7 Modifying the Behavior of Android Applications without Source Code
- Chapter 8 Hacking Android
- Chapter 9 Securing Android for the Enterprise Environment
- Chapter 10 Browser Security and Future Threat Landscape
- Appendix A
- Appendix B
- Appendix C
- Glossary
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Android Security by Anmol Misra,Abhishek Dubey in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.