
Network Analysis Using Wireshark 2 Cookbook - Second Edition
- 626 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Network Analysis Using Wireshark 2 Cookbook - Second Edition
About this book
Over 100 recipes to analyze and troubleshoot network problems using Wireshark 2About This Book• Place Wireshark 2 in your network and configure it for effective network analysis• Deep dive into the enhanced functionalities of Wireshark 2 and protect your network with ease• A practical guide with exciting recipes on a widely used network protocol analyzerWho This Book Is ForThis book is for security professionals, network administrators, R&D, engineering and technical support, and communications managers who are using Wireshark for network analysis and troubleshooting. It requires a basic understanding of networking concepts, but does not require specific and detailed technical knowledge of protocols or vendor implementations. What You Will Learn• Configure Wireshark 2 for effective network analysis and troubleshooting• Set up various display and capture filters• Understand networking layers, including IPv4 and IPv6 analysis• Explore performance issues in TCP/IP• Get to know about Wi-Fi testing and how to resolve problems related to wireless LANs• Get information about network phenomena, events, and errors• Locate faults in detecting security failures and breaches in networksIn DetailThis book contains practical recipes on troubleshooting a data communications network. This second version of the book focuses on Wireshark 2, which has already gained a lot of traction due to the enhanced features that it offers to users. The book expands on some of the subjects explored in the first version, including TCP performance, network security, Wireless LAN, and how to use Wireshark for cloud and virtual system monitoring. You will learn how to analyze end-to-end IPv4 and IPv6 connectivity failures for Unicast and Multicast traffic using Wireshark. It also includes Wireshark capture files so that you can practice what you've learned in the book. You will understand the normal operation of E-mail protocols and learn how to use Wireshark for basic analysis and troubleshooting. Using Wireshark, you will be able to resolve and troubleshoot common applications that are used in an enterprise network, like NetBIOS and SMB protocols. Finally, you will also be able to measure network parameters, check for network problems caused by them, and solve them effectively. By the end of this book, you'll know how to analyze traffic, find patterns of various offending traffic, and secure your network from them.Style and approachThis book consists of practical recipes on Wireshark 2 that target novices as well as intermediate Wireshark users. It goes deep into the technical issues, covers additional protocols, and many more real-live examples so that you are able to implement it in your daily life scenarios.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
FTP, HTTP/1, and HTTP/2
- Analyzing FTP problems
- Filtering HTTP traffic
- Configuring HTTP preferences
- Analyzing HTTP problems
- Exporting HTTP objects
- HTTP flow analysis
- Analyzing HTTPS traffic – SSL/TLS basics
Introduction
Analyzing FTP problems
- Active mode (ACTV): In this mode, the client initiates a control connection to the server, and the server initiates a data connection to the client
- Passive mode (PASV): In this mode, the client initiates both the control and data connections to the server
Getting ready
- The FTP server port
- The client port
- A link that the traffic crosses
How to do it...
- First, check for any Ethernet, IP, or TCP problems as described in previous chapters. In many cases, slow responses happen due to networking problems and not necessarily due to application problems. Perform simple ICMP ping (with a larger packet size, say 1,500 bytes) between the client and server, as it helps to find if there is any delay or failures along the path.
- Check for TCP retransmissions and duplicate ACKs. Check whether they are on the entire traffic or only on the FTP connection:
- If you get it on various connections, it is probably due to a slow network that influences the entire traffic
- If you get it only on FTP connections to the same server or client, it can be due to a slow server or client
- When you are copying a single file in an FTP file transfer, you should get a straight line in the I/O graph and a straight gradient in the TCP stream graph (time sequence).
- In this screenshot, we can see what a bad FTP looks like in the TCP stream graph (time sequence):
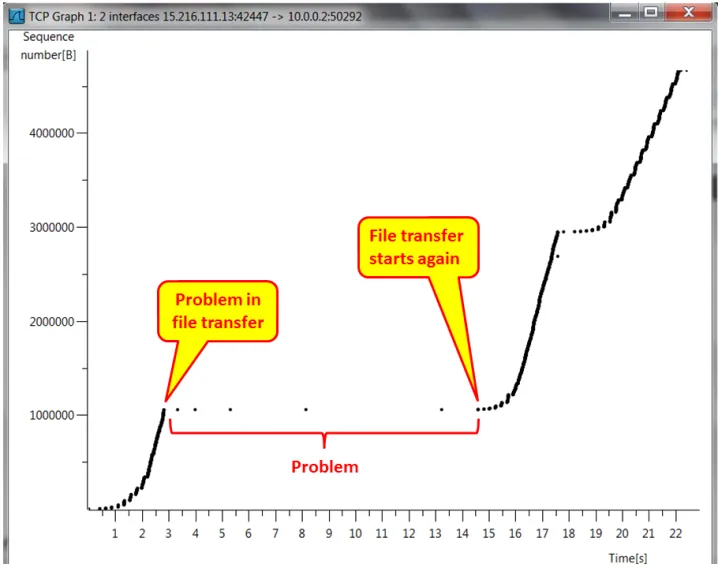
- In the following screenshot, we can see what it looks like in the I/O graph (configured with filters):

- In the capture file shown in the following screenshot, we can see TCP window problems. These are listed as follows:
- The server 15.216.111.13 sends a TCP Window Full message to the client, indicating that the server send window is full (packet 5763).
- The client 10.0.0.2 sends a TCP Zero Window message to the server, telling the server to stop sending data (packet 5778).
- The server keeps sending TCP Zero Window Probe messages to the client, asking the client whether the condition is still zero window (this tells the server not to send any more data). The client answers these messages with TCP Zero Window Probe Ack, indicating that this is still the case (packets 5793 to 5931).
- After a while, the client sends the message TCP Window Update to the server, telling it to start increasing the FTP throughput (packet 5939).
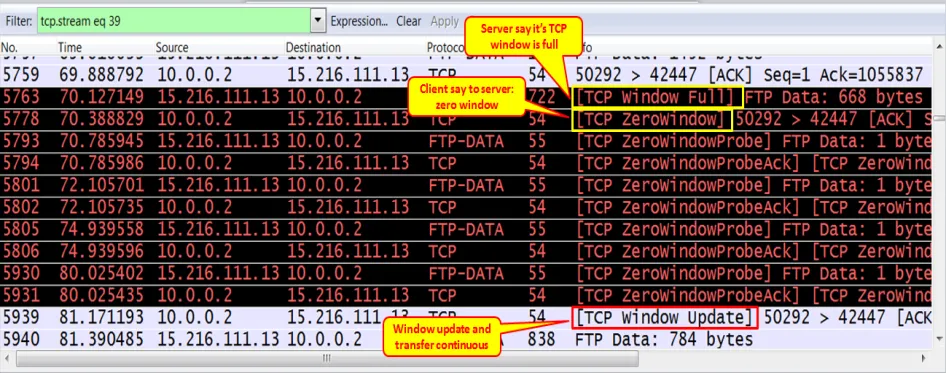
- In the preceding case, it was simply a slow client. We solved the problem by working over it and deleting some unnecessary processes.
- Was the TCP connection opened properly with the SYN/SYN-ACK/ACK packets? If not, it could be due to the following:
- The firewall that blocks communications. Check with the system administrator.
- The server that is not running. Check this on the server in the process table, FTP server management, and so on.
- A software of the server blocks connectivity. It can be an antivirus that has an additional firewall that blocks con...
Table of contents
- Title Page
- Copyright and Credits
- Dedication
- Packt Upsell
- Contributors
- Preface
- Introduction to Wireshark Version 2
- Mastering Wireshark for Network Troubleshooting
- Using Capture Filters
- Using Display Filters
- Using Basic Statistics Tools
- Using Advanced Statistics Tools
- Using the Expert System
- Ethernet and LAN Switching
- Wireless LAN
- Network Layer Protocols and Operations
- Transport Layer Protocol Analysis
- FTP, HTTP/1, and HTTP/2
- DNS Protocol Analysis
- Analyzing Mail Protocols
- NetBIOS and SMB Protocol Analysis
- Analyzing Enterprise Applications' Behavior
- Troubleshooting SIP, Multimedia, and IP Telephony
- Troubleshooting Bandwidth and Delay Issues
- Security and Network Forensics
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app