• Discuss what constitutes a traditional approach to the nature of security.
• Critique the scientific method and engineering design process for the study of security science.
• Examine the diverse and interrelated disciplines and practice domains of security.
• Evaluate theories or concepts that provide definitions of security.
• Appraise the need to provide context when defining the concept of security.
• Defend a framework that supports a contextual definition of security science.
Introduction
The traditional academic disciplines have evolved and developed over centuries to reach their current state of refinement. These traditional disciplines, such as astronomy, physics, mathematics, medicine, and, more recently, biology and environmental science, exhibit a set of characteristics by which each can be designated as a discipline. Some of the characteristics of a discipline would include:
1. Body of knowledge: A well-defined and inclusive body of knowledge.
2. Structure of knowledge: An internal structure of the knowledge, achieved through internal relationships between concepts so that consistency and logic prevail.
3. Concepts and principles: The building blocks of the knowledge of a discipline are concepts, and the relationships between concepts are governed by principles.
4. Theories: Theories are predictive in function and provide the ultimate test for a discipline, as outcomes can be predicted.
The knowledge domain of security has yet to achieve the status of being designated an academic discipline, as it lacks validity in the characteristics of the traditional disciplines. However, the emerging security science discipline will aspire to these characteristics with future ongoing research applied to the characteristics of a discipline, to provide the context for knowledge, structure, principles, and predictive theories.
Security lacks definition and, therefore, lacks structured knowledge. In addition, security is diverse, cross-disciplined, and without a defined or specified knowledge or skill structure (Hesse and Smith, 2001). Nevertheless, this should not lead to a conclusion that security does not contain a definable knowledge structure. The diversity and cross-disciplined nature of security will evolve as the discipline becomes more professional, concepts are developed and defined, and tertiary education programs increase. Professional development is an essential component of professional employment, as it allows the individual to maintain currency in their chosen career. Thus, professional diversity has to be bounded by structured knowledge concepts. A characteristic of professional development is that it is both ongoing and directed—that is, to maintain the confidence of the community in the knowledge and skills base of a profession, you must continue to strive to be at the leading edge of knowledge in your chosen discipline.
The foundation for the continued development of formal knowledge of security and its applications for the protection of assets in the national and international contexts will depend on an understanding of the principles and concepts of the emerging discipline of security. Research and development in the structure of the discipline of security is crucial for the professional application of a new generation of conceptual principles of security for the protection of assets. As Fischer et al. (2008, p. 482) suggested, the future of security is very positive considering the growth indicated in the discipline.
Security lacks characteristics of a discipline, with a defined and inclusive definition, as the concept of security is diverse and multidimensional. Nevertheless, security can be defined given context. Therefore, this chapter introduces the concept of security and provides definition through context and the presentation of supporting theories, models, and frameworks. Thus, a definition goes some way in achieving such understanding as to why security is multidimensional in nature through a staged approach, commencing from security of the individual to security of national and international systems. Security is a human characteristic that is objective, perceived, expected, and demanded by people in many different forms. It is perhaps one concept that over many decades has not changed in its original use; rather, it has become more broadly used to encompass greater and more diverse meaning.
Scientific method in support of security science
The development of the knowledge base in security science depends on its advancement as a discipline, and the extent of interaction between academia and professional practitioners of the security industry. The knowledge base for the emerging discipline of security will be enhanced by ongoing research both in the fundamental context of theory development and the applied context of asset protection. It is necessary for government, academia, and the commercial security industry to contribute to this knowledge base.
The stages in the development of a scientific discipline depend on the application of the scientific method to the knowledge base under consideration. The scientific method is a process for experimentation to seek cause-and-effect relationships between observable factors in the information of data gathered. For example, does the presence of a person in an e-field detector distort the field so that intrusion can be registered? From a social perspective, do people use utility theory when accessing security risk or do they take a heuristic approach? Whether in the hard or soft sciences, the scientific method seeks the cause-and-effect relationship by controlling the variables in the experimentation of the phenomenon.
A definite feature of a science is that there are a set of procedures that demonstrate how outcomes are produced, and these procedures are sufficiently detailed so that others may replicate the process to verify or refute the outcomes. The scientific method is a process of inquiry that regards itself as fallible, and as a result purposely tests itself and criticizes its outcomes to correct and improve itself. Although there are several versions of the scientific method, a basic approach involves a four-stage model to develop knowledge of a natural phenomenon:
1. Gather data by measuring or recording the observations of the phenomenon.
2. Construct an idea of how the phenomenon operates or functions in the form of a hypothesis.
3. Test or evaluate the idea or hypothesis by designing an experiment to show the operation or function of the phenomenon.
4. Analyze the results of the experiment to see if the hypothesis is true or false; if it is true, then the idea may be formalized as a theory.
Scientific Method
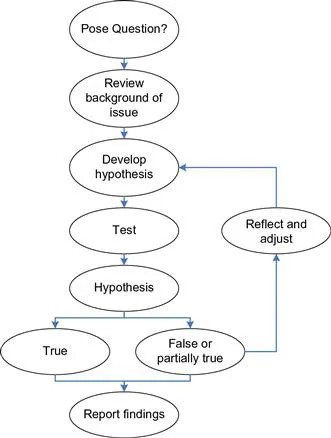
The model of the scientific method can be expanded with preplanning for background research or information seeking before the hypothesis testing stage, and the model can be extended with an outcomes communication or reporting stage after the analysis to disseminate findings to practitioners and interested people (Figure 1.1). The strength of the scientific method is that a formalized process is applied to the problem, and an outcome will either be gained or rejected. A feature of the scientific method is that the hypothesis of the problem can be tested time after time, and if the hypothesis continues to be accepted then it is accepted as knowledge. However, if the hypothesis is rejected once, then the model will not be accepted. The strength of the scientific method is that anyone can conduct the hypothesis testing for the problem, and thus establish the validity of the model.
Figure 1.1 Stages of the scientific method showing the hypothesis testing of an idea.
The regularization of observations of a phenomenon can eventually be presented as a theory, provided the phenomenon is scrutinized many times from a variety of viewpoints and with the same outcomes for each experiment. Figure 1.1 shows that if the result of hypothesis testing is false or partially true, then a modified hypothesis must be tested. When consistency of testing the hypothesis is obtained, then the idea becomes a theory and provides a coherent set of propositions that explain a class of phenomena. The theory can be considered as a framework to explain further observations, from which predictions can be made.
The strength of the scientific method is that it is unprejudiced—that is, it is not necessary to believe the results or outcomes of a particular researcher, as one can replicate the experiment and determine whether the results are true or false. The outcomes of the hypothesis testing do not depend on a particular experimenter, so that faith or belief does not play any part in the logical proof or material evidence on whether a scientific idea or theory is adopted or discarded. Thus, a theory is accepted, not based on the proponent, but rather on the quality of the results obtained through observations or experiments. Results obtained through the process of the scientific method are repeatable and reproducible.
An important characteristic of a scientific theory or hypothesis is that it must be falsifiable. That is, if any single experiment relevant to the hypothesis is shown to be negative or untrue, the hypothesis must be rejected. Thus, theories cannot be proven when the hypotheses are tested, but only rejected when a negative test results from an experiment. The philosopher Wittgenstein (1953) in his analyses of experimentation claimed that “there is no independent criterion of correctness,” so that the scientific method must continue to test the validity of its knowledge.
In a tested scientific hypothesis, a prediction is a rigorous, often quantitative, statement forecasting new outcomes under specific conditions of the idea being considered. The scientific method is formulated on testing assertions that are logical consequences of scientific theories, developed through repeatable experiments or observ...