
Beyond EHR
Using Technology to Meet Growing Demands and Deliver Better Patient Care
Jeffery Daigrepont, EFPM, CAPPM
- 198 Seiten
- English
- ePUB (handyfreundlich)
- Über iOS und Android verfügbar
Beyond EHR
Using Technology to Meet Growing Demands and Deliver Better Patient Care
Jeffery Daigrepont, EFPM, CAPPM
Über dieses Buch
Today, it is not uncommon for practices and hospitals to be on their second or third EHR and/or contemplating a transition from the traditional on-premise model to a cloud-based system. As a follow-up to Complete Guide and Toolkit to Successful EHR Adoption (©2011 HIMSS), this book builds on the best practices of the first edition, fast-forwarding to the latest innovations that are currently leveraged and adopted by providers and hospitals. We examine the role that artificial intelligence (AI) is now playing in and around EHR technology. We also address the advances in analytics and deep learning (also known as deep structured or hierarchical learning) and explain this topic in practical ways for even the most novice reader to comprehend and apply.
The challenges of EHR to EHR migrations and data conversions will also be covered, including the use of the unethical practice of data blocking used as a tactic by some vendors to hold data hostage. Further, we explore innovations related to interoperability, cloud computing, cyber security, and electronic patient/consumer engagement.
Finally, this book will deal with what to do with aging technology and databases, which is an issue rarely considered in any of the early publications on healthcare technology. What is the proper way to retire a legacy system, and what are the legal obligations of data archiving?
Though a lot has changed since the 2011 edition, many of the fundamentals remain the same and will serve as a foundation for the next generation of EHR adopters and/or those moving on to their second, third, fourth, and beyond EHRs.
Häufig gestellte Fragen
Information
Chapter 1
The Current State of the Healthcare IT Market
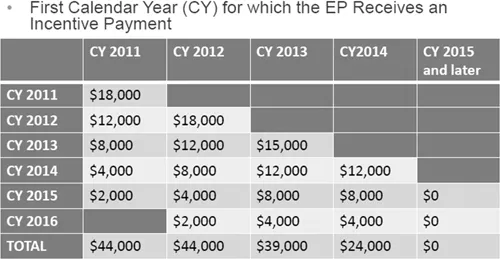
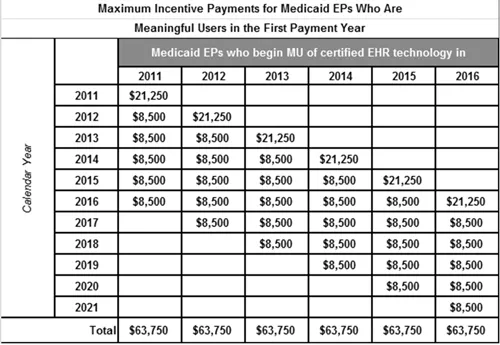
Original EHR Incentives | Current EHR Incentives |
|
|
MU was based on five main objectives, according to the Centers for Disease Control and Prevention. They were:
|
MU has now shifted to a Merit-Based Incentive Payment System and is combined with the Medicare Access and CHIP Reauthorization Act (MACRA); the Medicare EHR Incentive Program, commonly referred to as Meaningful Use, was transitioned to become one of the four components of the new Merit-Based Incentive Payment System (MIPS), which itself is part of MACRA. MIPS harmonizes existing CMS quality programs (including Meaningful Use), the Physician Quality Reporting System and Value-Based Payment Modifiers. MIPS consolidates multiple quality programs into a single program to improve quality care. |
The payout was over 5 stages with phase one starting with 15 core requirements and 10 menu requirements. All core requirements are mandatory. Additional core requirements were added each year by CMS. There were two payout tracks.
|
The first year started at a plus or minus of 4%, and it is set to go up to plus or minus 9% by 2021. Additional incentives can be gained through alternative payment models, but the risk is higher. |
Task | Completed |
Define the scope of the risk analysis and collect data regarding the ePHI pertinent to the defined scope. | |
Identify potential threats and vulnerabilities to patient privacy and to the security of your practice’s ePHI. | |
Assess the effectiveness of implemented security measures in protecting against the identified threats and vulnerabilities. | |
Determine the likelihood a particular threat will occur and the impact such an occurrence would have on the confidentiality, integrity and availability of ePHI. | |
Determine and assign risk levels based on the likelihood and impact of a threat occurrence. | |
Prioritize the remediation or mitigation of identified risks based on the severity of their impact on your patients and practice. | |
Document your risk analysis, including information from the steps above, as well as the risk analysis results. | |
Review and update your risk analysis periodically. |
Conducting a HIPAA Security Rule Risk Analysis
Inhaltsverzeichnis
- Cover
- Half-Title
- Title
- Copyright
- Contents
- Foreword
- Preface
- About the Authors
- Acronyms
- Introduction
- 1 The Current State of the Healthcare IT Market
- 2 Cloud Computing
- 3 Cybersecurity Threats beyond EHR
- 4 Health Information Technology Compliance
- 5 Using Artificial Intelligence in Healthcare
- 6 Improving Patient Engagement with Technology
- 7 EHRs and Telemedicine
- 8 Advanced Analytics and Dashboard Reporting
- 9 Interoperability
- 10 Vendor Contracting and Negotiations
- 11 Implementation and Project Management
- 12 Future Healthcare Information Trends and the Internet of Things
- 13 Tools and Policies
- Index