
eBook - ePub
Supply Chain Risk Management
Applying Secure Acquisition Principles to Ensure a Trusted Technology Product
Ken Sigler, Dan Shoemaker, Anne Kohnke
This is a test
Compartir libro
- 278 páginas
- English
- ePUB (apto para móviles)
- Disponible en iOS y Android
eBook - ePub
Supply Chain Risk Management
Applying Secure Acquisition Principles to Ensure a Trusted Technology Product
Ken Sigler, Dan Shoemaker, Anne Kohnke
Detalles del libro
Vista previa del libro
Índice
Citas
Información del libro
The book presents the concepts of ICT supply chain risk management from the perspective of NIST IR 800-161. It covers how to create a verifiable audit-based control structure to ensure comprehensive security for acquired products. It explains how to establish systematic control over the supply chain and how to build auditable trust into the products and services acquired by the organization. It details a capability maturity development process that will install an increasingly competent process and an attendant set of activities and tasks within the technology acquisition process. It defines a complete and correct set of processes, activities, tasks and monitoring and reporting systems.
Preguntas frecuentes
¿Cómo cancelo mi suscripción?
¿Cómo descargo los libros?
Por el momento, todos nuestros libros ePub adaptables a dispositivos móviles se pueden descargar a través de la aplicación. La mayor parte de nuestros PDF también se puede descargar y ya estamos trabajando para que el resto también sea descargable. Obtén más información aquí.
¿En qué se diferencian los planes de precios?
Ambos planes te permiten acceder por completo a la biblioteca y a todas las funciones de Perlego. Las únicas diferencias son el precio y el período de suscripción: con el plan anual ahorrarás en torno a un 30 % en comparación con 12 meses de un plan mensual.
¿Qué es Perlego?
Somos un servicio de suscripción de libros de texto en línea que te permite acceder a toda una biblioteca en línea por menos de lo que cuesta un libro al mes. Con más de un millón de libros sobre más de 1000 categorías, ¡tenemos todo lo que necesitas! Obtén más información aquí.
¿Perlego ofrece la función de texto a voz?
Busca el símbolo de lectura en voz alta en tu próximo libro para ver si puedes escucharlo. La herramienta de lectura en voz alta lee el texto en voz alta por ti, resaltando el texto a medida que se lee. Puedes pausarla, acelerarla y ralentizarla. Obtén más información aquí.
¿Es Supply Chain Risk Management un PDF/ePUB en línea?
Sí, puedes acceder a Supply Chain Risk Management de Ken Sigler, Dan Shoemaker, Anne Kohnke en formato PDF o ePUB, así como a otros libros populares de Business y Operations. Tenemos más de un millón de libros disponibles en nuestro catálogo para que explores.
Información
Chapter 1
Why Secure Information and Communication Technology Product Acquisition Matters
At the conclusion of this chapter, the reader will understand the following (Figure 1.1):






Introduction to the Book
The purpose of this book is to ensure an understanding of the strategic process of trusted product acquisition, which is directly associated with the discipline of SCRM. This chapter will introduce the concepts and principles of formal trusted product acquisition governance as well as the standard principles and underlying activities that define best practice in the performance of secure product sourcing.
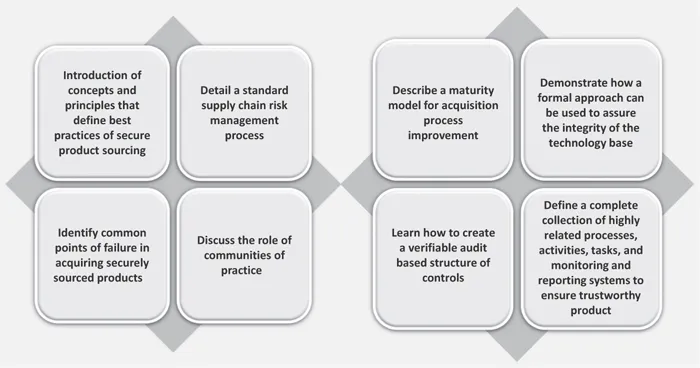
Figure 1.1 Objectives of the book.
This book will also detail a standard SCRM process that is integral to securing ICT acquisition in a global business environment. It will identify the common points of failure in acquiring adequately secure sourced products, and it will explain the factors that drive those failures. Readers will see how difficult it is to acquire ICT products that are trustworthy and secure, and they will understand the fundamental causes of that difficulty. Readers will discover the role of communities of practice in the overall process of building a complex ICT product, and since continuous capability improvement is the essence of maintaining an effective security posture, Chapter 7 will describe a maturity model for Acquisition Process Improvement.
The goal of this chapter is to demonstrate how a formal approach to acquisition and supply chain security can be used to assure the integrity of the technology base of any organization. The key concept here is “across-the-board trust” because all of the potential components of the technology base are involved in the secure functioning of the system. Consequently, every aspect of that base must be dependably secure or “the weakest link” applies. The reader will discover how formal processes and a standard baseline reference are necessary to establish that requisite level of trust.
Underwriting Trust and Competence
The vast range of ICTs have created our digital culture. Consider that 30 years ago you could not shop, bank, buy stocks online, play games, or interact with people on a mobile device. Now that is all possible, and new opportunities seem to pop up at an unthinkably frantic rate. At the same time, because of the dependence on the Internet, it is critically important to be able to trust the security and integrity of all of our ICT products, and that is demonstrably not the case.
According to the Privacy Rights Clearing House, close to one billion consumer records have been lost or stolen over the last decade. According to McAfee and the Center for Strategic and International Studies, that translates to $300 billion to $1 trillion in annual loss. Therefore, it is not surprising that industry and government have decided to address the problem of ICT product security. Just like buying a suit off the rack rather than having it bespoke tailored means that the customer will get it faster and cheaper, the business logic makes it inescapable for most modern companies to purchase rather than develop their own ICT products. Businesses want their solutions now, not at some time in the indeterminate future, and they do not want to spend the R&D money to back the development of custom packages. In many respects, because solutions are purchased rather than built, the procurement staff is as critical to the security of the ICT operation as the technical staff.
An organization’s ICT procurement process is no different from any other purchasing function in that the purpose of any procurement activity is to acquire an effective product for the organization. Consequently, whether the product is a video game or a piece of sophisticated military hardware, the activities that take place within the acquisition process have to be logically related, controlled, and coordinated. A standard model of the best practices to be carried out within that process simply ensures that the control is implemented systematically and is effectively maintained through the specific actions of the individuals who are responsible for performing the assigned task.
From a security and integrity standpoint, what this implies is that every individual action in the overall process has to be rationally and properly placed in the timeline for execution. Additionally, each task must be fully and correctly integrated into the overall activity. Therefore, at its core, the acquisition process that will be discussed here must be well defined and properly executed. It must ensure that proper relationships are maintained among the larger set of actions that have been arrayed to achieve a given purpose.
Justification and Objectives of the Book
Perhaps the best way to justify this book is the statement that it has been long overdue. Technology systems are complex and their elements are indistinguishable by normal inspection. Thus, the usual way to acquire trustworthy ICT products has been to only deal with suppliers who are “known and trusted” over a reasonable period of time. Even so, in a modern global sourcing environment, a trusted supplier has the potential to integrate subcomponents that are obtained from untrustworthy sources into a system. Therefore, when it comes to acquiring the technology needed, any purchaser of an ICT product is essentially “buying a pig in a poke,” so to speak. This is a particularly egregious situation given the “faster-cheaper-better” mentality of current companies, and it has led to an overreliance on suppliers’ commercial-off-the-shelf (COTS) system security to leverage development strategies.
The problem is that until recently there has been no common body of knowledge that can be relied on to provide a standard set of practices for executing secure, end-to-end technology purchases. Fortunately, this has changed primarily due to the dawning recognition that elements of our critical infrastructure may already contain malicious items, which have been placed there as a result of insecure supply chains and a slipshod open-source acquisition process.
The ideas presented in this book are well-established aspects of a single process that has been developed and promulgated by the federal government to ensure trusted product acquisition in its particular space. Specifically, this book presents the concepts of ICT SCRM from the perspective of NIST SP 800-161, which is the first standard body of knowledge for secure SCRM (NIST, 2015). In this book, you will learn how to create a verifiable audit-based structure of controls, which will ensure comprehensive security for all types of sourced ICT products. We will explain how to establish systematic security within the supply chain as well as how to build auditable trust into the products and services that are acquired by the organization.
In addition, we will detail a unique capability maturity development process that will help foster an increasingly competent process. The overall aim of this book is to define a complete and correct collection of highly related processes, activities, and tasks as well as the attendant monitoring and reporting systems to ensure a trustworthy product. A practical and standard means of leveraging the acquisition process to higher levels of capability maturity is also explained in this text. The details of this process are captured in a very well-known and widely accepted approach to capability maturity development. Thus, the information in this book is both authoritative and commonly agreed upon.
The Five-Part Problem
As we said in the last section, this book centers on the belief that SCRM is a strategic governance concern. Thus, the practical governance solution to the acquisition process is a formally defined and concrete infrastructure of best practices, which are aimed at ensuring sufficient coordination and control over the entire process. The objective is to ensure that all sourced products fall within certain levels of trust. As with any complex goal, the assurance of product trustworthiness can only be substantiated through activities that take place within a rational and explicit framework of auditable procedures. Thus, the basis for creating and deploying these procedures is presented in this chapter.
The General Accounting Office (GAO) summarized the concerns associated with organizational ICT SCRM in a March 23, 2012, report. ICT risk issues fall into five categories, each of which has a slightly different implication for product integrity: “installation of malicious logic on hardware or software; installation of counterfeit hardware or software; failure or disruption in the production or distribution of a critical product or service; reliance upon a malicious or unqualified service provider for the performance of a technical service; and installation of unintentional vulnerabilities on software or hardware” (GAO, 2012, p. 1) (Figure 1.2).
Malicious logic is embedded in a product to fulfill some specific purposes. Malicious objects are by definition not part of the intended functionality; therefore, in order to find and eliminate any instance, rigorous testing and inspection is required. Embedding a malicious object in a product is always a hostile act, and assurance that a product is free of malicious code should be a high priority with any ICT customer. Nonetheless, since it is hard enough to ensure the quality and security of the functions that ought to be present in a piece of software, it is asking a lot to expect that functions that should not be present should also be identified and eliminated. Therefore, it is almost impossible to estimate how much malicious code currently resides in ICT products. Because the decision to embed a piece of malicious logic in a product is intentional, one of the most effective ways to ensure against the presence of such objects is to maintain strict oversight and control over ICT development, sustainment, and acquisition work.
Counterfeits are not just an acquisition issue. Counterfeit parts can appear at any stage in the development and sustainment of ICT products. Counterfeits execute product functions as intended and threaten product security and integrity because they are not the same as the actual part. Generally, the purpose of a counterfeit is to save money or supply a feature that the maker is otherwise incapable of providing. As a result, counterfeits embody shortcuts in product quality or security that can fail in many ways. Because they function like the original part, it is often hard to spot a counterfeit in a large array of legitimate components. Therefore, it is critically important that customers fully and completely understand their supplier’s business and technical practices prior to engaging in any use of the products. A capability model is particularly helpful in enforcing that understanding...