
eBook - ePub
Bowtie Methodology
A Guide for Practitioners
Sasho Andonov
This is a test
Compartir libro
- 192 páginas
- English
- ePUB (apto para móviles)
- Disponible en iOS y Android
eBook - ePub
Bowtie Methodology
A Guide for Practitioners
Sasho Andonov
Detalles del libro
Vista previa del libro
Índice
Citas
Información del libro
Bow Tie Methodology (BTM) consists of two methods, Fault Tree Analysis (FTA) and Event Tree Analysis (ETA), which are connected by a single event. The methodology is holistic and provides the tools and pre-event analysis, which is also called the risk calculations, and post-event analysis, also called the risk mitigations, of quality and safety related events. There are plenty of articles or chapters on this methodology, however there is no book that covers everything in one place. The book is filled with examples taken from the aviation industry and elaborates theory implemented in practice, which gives quality and safety practitioners a guidance on how to use and apply BTM in practice.
Preguntas frecuentes
¿Cómo cancelo mi suscripción?
¿Cómo descargo los libros?
Por el momento, todos nuestros libros ePub adaptables a dispositivos móviles se pueden descargar a través de la aplicación. La mayor parte de nuestros PDF también se puede descargar y ya estamos trabajando para que el resto también sea descargable. Obtén más información aquí.
¿En qué se diferencian los planes de precios?
Ambos planes te permiten acceder por completo a la biblioteca y a todas las funciones de Perlego. Las únicas diferencias son el precio y el período de suscripción: con el plan anual ahorrarás en torno a un 30 % en comparación con 12 meses de un plan mensual.
¿Qué es Perlego?
Somos un servicio de suscripción de libros de texto en línea que te permite acceder a toda una biblioteca en línea por menos de lo que cuesta un libro al mes. Con más de un millón de libros sobre más de 1000 categorías, ¡tenemos todo lo que necesitas! Obtén más información aquí.
¿Perlego ofrece la función de texto a voz?
Busca el símbolo de lectura en voz alta en tu próximo libro para ver si puedes escucharlo. La herramienta de lectura en voz alta lee el texto en voz alta por ti, resaltando el texto a medida que se lee. Puedes pausarla, acelerarla y ralentizarla. Obtén más información aquí.
¿Es Bowtie Methodology un PDF/ePUB en línea?
Sí, puedes acceder a Bowtie Methodology de Sasho Andonov en formato PDF o ePUB, así como a otros libros populares de Tecnologia e ingegneria y Ingegneria industriale. Tenemos más de un millón de libros disponibles en nuestro catálogo para que explores.
Información
1
Introduction to Bowtie Methodology*
1.1 Introduction
The Bowtie methodology (BM) is a methodology that specifies two methods for one more general model (theory) for risk analysis.
This general model (theory) states that there is a risk of something to happen and there are previous and later activities to help us analyze and eliminate (mitigate) the risk. Previous activities for risk analysis are methods that are used to find the cause for the event happening (determined by a particular risk), while later activities are used to explain the scenarios of the development of the consequences caused by this event. From this general definition of the model for risk analysis any two methods can be used.
The BM is more specific by using two methods for previous and later analysis of the so-called Main Event that can happen in the system. The first method is Fault Tree Analysis (FTA) and the second one is Event Tree Analysis (ETA). In the BM configuration, FTA is known as Pre-Event Analysis and ETA is known as Post-Event Analysis.
The BM gets its name due to the shape of the diagram which arises when these two methods are connected to the point called Main Event (Figure 1.1). A Main Event can be connected with a system, process, activity, operation, situation, measurement, and so on. That brings us to the main point of the BM: It can be applied to systems, processes, activities, operations, situations, specifications, and so on. Whatever the Main Event is, we must know where (in which system, which part, etc.) and when this event (operation, activity, etc.) could happen.
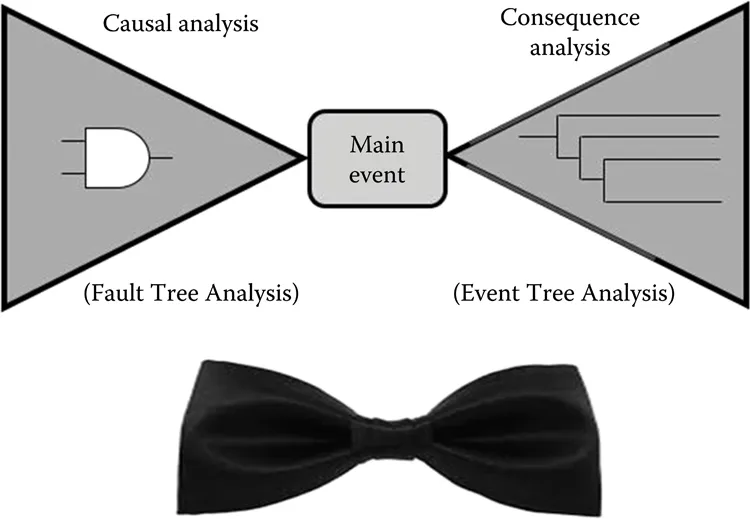
FIGURE 1.1
Bowtie methodology (BM) diagram and ordinary Bowtie. (In some literature you can find the graphical presentation of Bowtie as the Cause-Consequence Diagram (CCD).)
Bowtie methodology (BM) diagram and ordinary Bowtie. (In some literature you can find the graphical presentation of Bowtie as the Cause-Consequence Diagram (CCD).)
Do not forget that in the beginning, the BM was linked to the reliability of equipment* and it proved itself good in this area. FTA was used for reliability calculations and ETA for measures to improve the reliability. Reliability was expressed as trust in the normal functioning of equipment and later it was spread to Risk Management. This happened especially in risky industries in the times when malfunctioning of equipment was counted as the main reason for incident and accidents.
It is important that both methods (FTA and ETA) can be used independently, but what connects them in the BM is the Main Event. This connection causes dependence between them, because changes in one of them can cause changes in another. Both methods will be described in detail later in this book, but only in the context for their use in the BM.
The main purpose of the BM is to provide accurate and reliable data for the decision-making process. This decision-making process is twofold. First, I use results from FTA to calculate the probability of the Main Event happening and then I use ETA to calculate the success or failure of the particular mitigation for consequences.
The area of use of the BM is wide. It can be used during the design phase, during implementations, system operations, and system modifications, but it provides best results when implemented during the design phase! At the beginning in the design phase, by using FTA (Pre-Event Analysis), I can calculate the frequency (probability) of the failures (Main Event) happening for the new product. Later, ETA (Post-Event Analysis) will give me a clear picture about the possibilities and scenarios to contain or mitigate the risk if the failure (Main Event) happens.
Here I should mention a very important point: the BM does not determine the severity of the Main Event. It must be determined in another process by taking into account the nature and environment of the Main Event. Anyway, to establish severity I will use the criteria that deal with the real situation of the systems under analysis. For different industries or even for different systems in the same industries, these criteria may be different.
What is also important that I should mention here is that the BM can also be used for a better understanding of different levels of functioning of processes in our management or production system. So, it is not necessarily connected with problems, but having in mind that the BM is highly descriptive, I can use it for quality control (QC) or quality assurance (QA) to improve our product or services offered.
1.2 BM in Oil and Petroleum Industry
I have already mentioned in Preface that there is another method with the same name (Bowtie) that is already used in the oil and petroleum industry.* I would like to explain here why I do not appreciate it very much.
This is a BM that deals, in the first instance, with hazards (causes) and barriers (controls) to the causes and, in the second instance, with mitigation and recovery actions for consequences. It is a method, not a methodology, and it starts with hazard identification. You may use any tool for hazard identification, and when the hazards are identified, the particular barriers are set to stop these hazards from developing into incidents or accidents. So, this is mostly a prevention method.
This is actually a method that presents the famous Swiss cheese model (Figure 1.2) of barriers and holes in the barriers. It is mostly used to build barriers for eliminating or mitigating safety hazards and later to check the effectiveness and efficiencies of already implemented barriers.
In Figure 1.3 are presented the differences between the method and the methodology.
This method does not use FTA for Pre-Event Analysis and ETA for Post-Event Analysis to calculate probabilities, which means that this is a method that does not calculate risks. It starts from hazards (not from the Main Event!) and later is upgraded with barriers and particular controls to prevent abnormal operations. After that, under the assumption that abnormal operations happened, there are particular measures for mitigation of the consequences or recovery actions to get back to the normal operations. All this is built under the analyzing concept of layers known as Layers of Protection Analysis (LOPA). It means that all barriers are posted by layers (one layer may contain a few barriers) and this structure provides a better understanding of the safety system dedicated to this operation. For example, Petrobras have nine such layers. Five are used to prevent the event and four are used to mitigate the consequences and provide fast recovery to normal operations. Associated with this method is the particular system for integrity monitoring in real time.
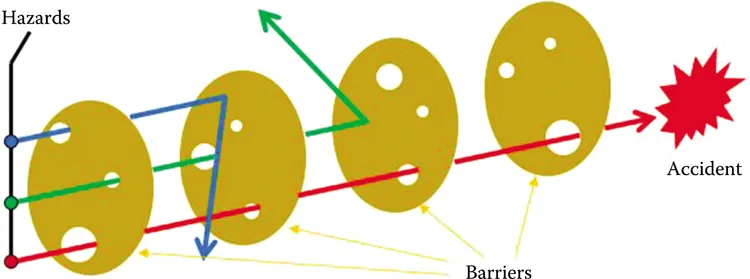
FIGURE 1.2
Cheese model.
Cheese model.
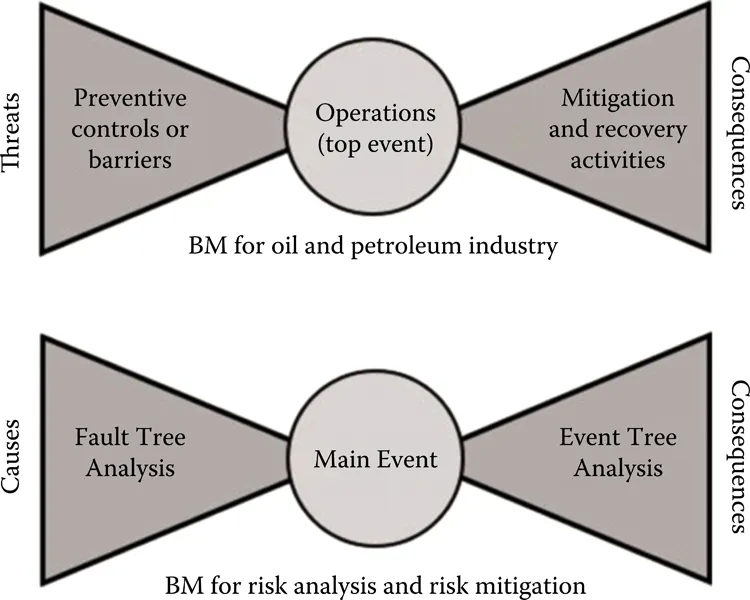
FIGURE 1.3
Comparing the BM in oil and petroleum industry with the BM for risk analysis and risk mitigation.
Comparing the BM in oil and petroleum industry with the BM for risk analysis and risk mitigation.
There are a few points that I do not like in this method.
The main point is that this method mixes threats with hazards and risks. For me that is very confusing. Maybe it works for employees, but not for me. Threats and hazards do not differ as much and risk is when the hazard is determined by its frequency (probability) and severity. Actually, as far as I know, threats are synonyms for hazards. This method associates hazards with the Main Event (which is named as the Top Event) and threats are actually taking the places of hazards in this diagram. But this is not a big issue if you notice that plenty of regulatory bodies make no difference between these terms. Even in the ISO 31000 standard (Risk Management) you cannot find the word “hazard” at all.
The second point (which I do not like here) is the fact that there is no explanation of how barriers are posted on particular positions. It means that this method does not provide us a real picture of what risks are for each hazard and how the risks progress after the posting of the barriers or preventive controls. To find this you need to use another method, which means that this one offers benefit only to the monitoring personnel who are overseeing normal operations or to regulatory staff who can see how the company is dealing with risks.
The third point is that when abnormal operation happens, there is no knowledge about the probability of success or failure of the mitigation or recovery action. Of course, the reason why these barriers are there is not clear and their quantification should be calculated by another method.
The fourth and maybe the most important point is that there is no information about how barriers, control measures, mitigation, and recovery activities depend on each other and how they influence the other parts of the system.
So this is an excellent descriptive method that can be used only as an explanation of how companies are providing and maintaining the safety of their operations, but its contribution to the safety assessment process is very poor. The main point is that after finishing with the BM for Risk Analysis and Risk Mitigation, you may produce this type of BM just to explain to employees, regulatory bodies, and public how they can handle safety in their operations. But I do not think that using it as a tool for the analysis and management of a risk can add any value.
In this book only the Bowtie methodology (not the method!) will be explained.
1.3 Context of Investigations in Science and Industry
I would like to mention here a very important point that is connected to our reality. I would like to speak about the context of points in life, science, and industry.
Let us speak about the context in our lives and let us say I would like to buy car.
There are many particular specifications that I would like my car to satisfy and all of them are dependent on my personality, my incomes, and my requirements. There are plenty of car manufacturers in the world. They differ by the models and classes of cars manufactured. The best ones are Jaguar, Porsche, Ferrari, McLaren, Bugatti, BMW, and so on. If the context of buying my car is to emphasize (or build) my status in the society, I will buy some of these cars.
There are also family cars produced by Opel, Toyota, Nissan, Volkswagen, Hyundai, and so on. Which car I would personally buy depends on the context of my requirements. If I need a car for simply driving in the city, I will buy a small, low-fuel consumption car that will not cost me a lot to buy it and to maintain it in the future. If I am an adventurer and I enjoy nature (sea, mountain, etc.), then I will buy 4 × 4 SUV (sport utility vehicle...