
eBook - ePub
Cyber Defense Mechanisms
Security, Privacy, and Challenges
Gautam Kumar, Dinesh Kumar Saini, Nguyen Ha Huy Cuong, Gautam Kumar, Dinesh Kumar Saini, Nguyen Ha Huy Cuong
This is a test
- 216 pages
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
eBook - ePub
Cyber Defense Mechanisms
Security, Privacy, and Challenges
Gautam Kumar, Dinesh Kumar Saini, Nguyen Ha Huy Cuong, Gautam Kumar, Dinesh Kumar Saini, Nguyen Ha Huy Cuong
Détails du livre
Aperçu du livre
Table des matières
Citations
À propos de ce livre
This book discusses the evolution of security and privacy issues and brings related technological tools, techniques, and solutions into one single source.
The book will take readers on a journey to understanding the security issues and possible solutions involving various threats, attacks, and defense mechanisms, which include IoT, cloud computing, Big Data, lightweight cryptography for blockchain, and data-intensive techniques, and how it can be applied to various applications for general and specific use.
Graduate and postgraduate students, researchers, and those working in this industry will find this book easy to understand and use for security applications and privacy issues.
Foire aux questions
Comment puis-je résilier mon abonnement ?
Il vous suffit de vous rendre dans la section compte dans paramètres et de cliquer sur « Résilier l’abonnement ». C’est aussi simple que cela ! Une fois que vous aurez résilié votre abonnement, il restera actif pour le reste de la période pour laquelle vous avez payé. Découvrez-en plus ici.
Puis-je / comment puis-je télécharger des livres ?
Pour le moment, tous nos livres en format ePub adaptés aux mobiles peuvent être téléchargés via l’application. La plupart de nos PDF sont également disponibles en téléchargement et les autres seront téléchargeables très prochainement. Découvrez-en plus ici.
Quelle est la différence entre les formules tarifaires ?
Les deux abonnements vous donnent un accès complet à la bibliothèque et à toutes les fonctionnalités de Perlego. Les seules différences sont les tarifs ainsi que la période d’abonnement : avec l’abonnement annuel, vous économiserez environ 30 % par rapport à 12 mois d’abonnement mensuel.
Qu’est-ce que Perlego ?
Nous sommes un service d’abonnement à des ouvrages universitaires en ligne, où vous pouvez accéder à toute une bibliothèque pour un prix inférieur à celui d’un seul livre par mois. Avec plus d’un million de livres sur plus de 1 000 sujets, nous avons ce qu’il vous faut ! Découvrez-en plus ici.
Prenez-vous en charge la synthèse vocale ?
Recherchez le symbole Écouter sur votre prochain livre pour voir si vous pouvez l’écouter. L’outil Écouter lit le texte à haute voix pour vous, en surlignant le passage qui est en cours de lecture. Vous pouvez le mettre sur pause, l’accélérer ou le ralentir. Découvrez-en plus ici.
Est-ce que Cyber Defense Mechanisms est un PDF/ePUB en ligne ?
Oui, vous pouvez accéder à Cyber Defense Mechanisms par Gautam Kumar, Dinesh Kumar Saini, Nguyen Ha Huy Cuong, Gautam Kumar, Dinesh Kumar Saini, Nguyen Ha Huy Cuong en format PDF et/ou ePUB ainsi qu’à d’autres livres populaires dans Ciencia de la computación et Ciberseguridad. Nous disposons de plus d’un million d’ouvrages à découvrir dans notre catalogue.
Informations
1 Security Threat Analysis and Prevention towards Attack Strategies
Suman De
SAP Labs India Pvt. Ltd.
CONTENTS
1.1 Introduction
1.2 History of Security Breaches
1.3 Common Security Threats
1.3.1 Malware
1.3.2 Phishing
1.3.3 Spear Phishing
1.3.4 “Man in the Middle” (MitM) Attack
1.3.5 Trojans
1.3.6 Ransomware
1.3.7 Denial-of-Service Attack or Distributed Denial-of-Service Attack (DDoS)
1.3.8 Attacks on IoT Devices
1.3.9 Data Breaches
1.3.10 Malware on Mobile Apps
1.4 Security Challenges in Modern Day
1.4.1 Cloud Computing
1.4.2 Social Media
1.4.3 Smart Phones
1.4.4 General Data Protection Regulations (GDPR)
1.4.5 Attacks Based on Machine Learning and AI
1.4.6 Attacks against Cryptocurrencies and Blockchain Systems
1.4.7 Switching to DevOps
1.4.8 Biometric Authentication
1.4.9 Fileless Malware
1.5 Attack Strategies and Brief Study on Advanced Persistent Threat (APT)
1.5.1 How an APT Attack Works
1.5.2 Some Instances of APTs
1.5.3 Characteristics of APTs
1.6 Prevention Measures
1.6.1 Identify the Threats
1.6.2 Beware of Cybercrimes
1.6.3 Observe All Stakeholders
1.6.4 Usage of Two-Factor Authentication
1.6.5 Conduct Regular Audits
1.6.6 Draft a Credit Sign-Off Policy
1.6.7 Protect Vital Data
1.6.8 Perform Risk Assessments
1.6.9 Insure against Cybercrime
1.6.10 Gather In-Depth Knowledge about Risk Factors
1.7 Threat Modeling
1.8 Role of a Threat Analyst
1.9 Summary
References
1.1 Introduction
Cybersecurity has become a matter of primary concern for organizations and world governments alike. The essence of every application is ranging from web-based offerings to mobile applications run into the common challenge of defending against intrusions by foreign attacks of cybercriminals. Data security provides another angle to the all security practices, and the governed aspects of policies like General Data Protection Regulations (GDPR) make it essential to software vendors to abide the needs of relevant governing laws and ensure quality with respect to security. This introduces the importance of incorporating security analysts to evaluate and ensure that the required guidelines and regulations are maintained wherever required. This chapter takes a tour of generic security threats and how the role of a security analyst helps discover potential threats and flaws in any software offering. The recent security threats are also explored and briefly discussed along with the possible prevention steps against known attack strategies.
Threat analysis is the process of evaluating suspicious actions and reach of unrecognized intelligence bodies or cybercriminals [1]. A cybersecurity threat is described as a malicious activity that looks to hamper the digital world. The activity could be damaging of data, intervention in a communication channel, or unauthorized retrieval of data. The generic target of hackers* includes business organizations, government bodies, institutions, and even individuals with influential identity. Cyberattacks can involve threats such as denial-of-service (DoS), malwares, software viruses, and phishing emails. These threats target entities with an online presence and relevance with respect to the attack. History has shown cyberattacks that have resulted in breaches of Government security missions, data breach in media houses, and massive fund transfers in bank frauds affecting regular activities of human life.
Security threats can be damaging but often follow well-defined strategic moves, which leads to a possible breach. The prevention of attack scenarios is well established by a study of possible attack strategies and the necessary steps that are needed to be taken to avoid any such breaches. Detecting, preventing, or dislodging the threat in the most convenient time reduces the business impact and the possibility of considerable effects. This chapter explores attack strategies and patterns that are used by cybercriminals or hackers to break in various systems.
* Hackers (indicative to crackers) are individuals who break into a system to gain unauthorized access to confidential data or to affect the regular functionality of a system.
1.2 History of Security Breaches
Confidential data extrapolation, social media breaches, and bank frauds are some common threats that make new headlines frequently. Keeping aside the generic ones, the terror spread through WannaCry ransomware attack or WikiLeaks have had significant impact on people and government powerhouses. In 2019 alone, 29 major breaches in financial institutions were affected, resulting in millions of dollars loss for them [2].
In May 2017 a ransomware attack called WannaCry targeted Microsoft Windows-based operating systems to demand ransom payments in Bitcoin cryptocurrency and was considered as a global epidemic. It was a type of crypto-ransomware (malicious software), used by cybercriminals to extort money. Such malwares achieve this by encrypting important files, so that the user is unable to read them, or they lock the user out of their own system, so that it cannot be accessed. This type of malicious software encryption is called crypto-ransomware and is often termed as locker ransomware. Crypto-ransomware keeps the data hostage, in return of ransom payment from the user.
More recently, a Football Leaks hacker, Rui Pinto, hacked and exposed the breaking of Financial Fair Play rules and is said to have accessed over 70 million documents and 3.4 TB of information about numerous football clubs [3]. He had leaked the information to German news magazine, Der Spiegel, and was imprisoned in 2019 for 90 separate cases of hacking and fraud. Table 1.1 shows the list of well-known cyberattacks or breaches.
Incident | Type of Attack | Year |
|---|---|---|
WannaCry Ransomware | Malware software demanding ransom | 2017 |
Koobface worm | Malware in social media sites—213K users affected | 2009 |
Equifax | Data breach affecting 145.5 million users | 2017 |
Dream market breach | Sixteen websites hacked and out on sale in the Dark web | 2019 |
Friend Finder networks | 412 Million accounts hacked and exposed | 2016 |
We also refer to the fraud cases or cyberattacks on financial institutions mentioned in the Carnegie Endowment for International Peace and see a huge rise in the numbers in recent years, which is shown in Figure 1.1. The facts hint at the more growing importance of securing systems by proper threat modeling. Be that as it may, the risk scene has been more concerning with country states progressively joining the blend and with the subsequent harm heightening, from burglary to interruption and demolition [4].
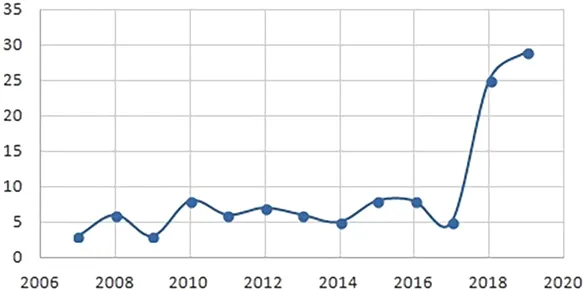
FIGURE 1.1 Cyberattack frequency on financial institutions since 2007 as per Carnegie Endowment.
1.3 Common Security Threats
Cyberattacks can emerge from multiple sources. Intruders target multiple possibilities to break in a system and can damage to it. A cyberthreat is an activity that intends to snoop data, distort data, or attempt to create major damage. These threats can be classified into some major types [5].
1.3.1 Malware
Malware is an application which does a harmful activity on a device, network, or system. Activities can result to corruption of data, gaining unauthorized access on confidential information or manipulation of data. The word “malware” is formed keeping the essence of two different words “malicious” and “software.” A malware can be a virus, Trojan, spyware, or ransomware that causes damage to a system. Viruses tend to associate itself with other entities to clear file content, or infect and damage relevant file content. Viruses spread with control, resulting in damage of a system’s primary features, and damaging or corrupting file content. Such software appears as executables (.exe) or batches (.bat), and cause harm to the system. Trojans are malwares that disguise itself as legitimate software or are hidden in legitimate software that has been tampered with. It acts discretely by making backdoors in the security system to allow significant malwares inside. Spywares are malicious software which are developed to spy on users. They hide themselves in the background and observe the user’s online activities, including passwords, credit card numbers, user behavior for websites, and other relevant activities. The primary objective of Worms is to infect a complete network of devices, both local and across the web, via network protocols, or interfaces. Ransomware attempts to lock down systems and relevant file content and sends a word to erase or damage significant data unless a ransom is paid. Another type of malware is Adware which is not harmful but causes a distraction for users and also creates an easier route for other malwares to creep into the system. Attackers can also utilize a network of computer to infect and work for personal benefits which is also another type of malware and is commonly known as Botnet.
Table des matières
- Cover
- Half Title
- Series Page
- Title Page
- Copyright Page
- Table of Contents
- Preface
- Editors
- Contributors
- Chapter 1 Security Threat Analysis and Prevention towards Attack Strategies
- Chapter 2 Defense against the Survivability to Network Strategies
- Chapter 3 Defense Mechanism to Self-Adaptive Cyber-Physical Security Systems
- Chapter 4 Secure Channel Allocation in Cognitive Radio–Wireless Sensor Networks
- Chapter 5 Security Issues in IoT Networks
- Chapter 6 IoT Ecosystem Implications to Real-World Security Scenario
- Chapter 7 Design Principles and Privacy in Cloud Computing
- Chapter 8 Big Data Analysis on Smart Tools and Techniques
- Chapter 9 Lightweight Security Protocols for Blockchain Technology
- Chapter 10 Privacy and Challenges to Data-Intensive Techniques
- Chapter 11 Dynamic Modeling on Malware and Its Defense in Wireless Computer Network Using Pre-Quarantine
- Chapter 12 Privacy Preservation Algorithms on Cryptography for AI as Human-like Robotic Player for Fighting Game Using Rule-Based Method
- Chapter 13 Web-Based Smart Agriculture System
- Index
Normes de citation pour Cyber Defense Mechanisms
APA 6 Citation
[author missing]. (2020). Cyber Defense Mechanisms (1st ed.). CRC Press. Retrieved from https://www.perlego.com/book/1636243/cyber-defense-mechanisms-security-privacy-and-challenges-pdf (Original work published 2020)
Chicago Citation
[author missing]. (2020) 2020. Cyber Defense Mechanisms. 1st ed. CRC Press. https://www.perlego.com/book/1636243/cyber-defense-mechanisms-security-privacy-and-challenges-pdf.
Harvard Citation
[author missing] (2020) Cyber Defense Mechanisms. 1st edn. CRC Press. Available at: https://www.perlego.com/book/1636243/cyber-defense-mechanisms-security-privacy-and-challenges-pdf (Accessed: 14 October 2022).
MLA 7 Citation
[author missing]. Cyber Defense Mechanisms. 1st ed. CRC Press, 2020. Web. 14 Oct. 2022.