
Data Breach Preparation and Response
Breaches are Certain, Impact is Not
Kevvie Fowler
- 254 pages
- English
- ePUB (adapté aux mobiles)
- Disponible sur iOS et Android
Data Breach Preparation and Response
Breaches are Certain, Impact is Not
Kevvie Fowler
À propos de ce livre
Data Breach Preparation and Response: Breaches are Certain, Impact is Not is the first book to provide 360 degree visibility and guidance on how to proactively prepare for and manage a data breach and limit impact. Data breaches are inevitable incidents that can disrupt business operations and carry severe reputational and financial impact, making them one of the largest risks facing organizations today. The effects of a breach can be felt across multiple departments within an organization, who will each play a role in effectively managing the breach. Kevvie Fowler has assembled a team of leading forensics, security, privacy, legal, public relations and cyber insurance experts to create the definitive breach management reference for the whole organization.
- Discusses the cyber criminals behind data breaches and the underground dark web forums they use to trade and sell stolen data
- Features never-before published techniques to qualify and discount a suspected breach or to verify and precisely scope a confirmed breach
- Helps identify your sensitive data, and the commonly overlooked data sets that, if stolen, can result in a material breach
- Defines breach response plan requirements and describes how to develop a plan tailored for effectiveness within your organization
- Explains strategies for proactively self-detecting a breach and simplifying a response
- Covers critical first-responder steps and breach management practices, including containing a breach and getting the scope right, the first time
- Shows how to leverage threat intelligence to improve breach response and management effectiveness
- Offers guidance on how to manage internal and external breach communications, restore trust, and resume business operations after a breach, including the critical steps after the breach to reduce breach-related litigation and regulatory fines
- Illustrates how to define your cyber-defensible position to improve data protection and demonstrate proper due diligence practices
Foire aux questions
Informations
An Overview of Data Breaches
Abstract
Keywords
Introduction
What Is a Data Breach?
Lifecycle of a Breach
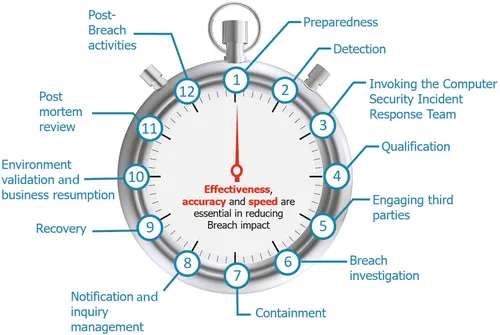
| Phase | Description | Chapter Reference | |
| 1 | Preparedness | The steps an organization takes in advance of a Breach to identify sensitive information, implement cyber defenses and detection capabilities, and to develop and test a Computer Security Incident Response (CSIR) Plan to manage an incident. Most organizations that suffer a material security incident have gone through this phase and have operated under the impression they were covered to an acceptable level. However, often errors in asset identification, security strategies, and incident response capabilities are quickly highlighted during and after management of an incident and organizations will almost always revisit this step after an incident to further improve preparedness including bolstering cyber security controls and response capabilities based on lessons learned. This phase is the beginning and the end of the management of any material incident | Chapters 2, 3, and 8 |
| 2 | Detection | The moment an organization is alerted about a security incident. Whether the incident was detected by organizational security controls, staff or by a third party organization or individual. After the detection of an incident, it is critical that it is escalated appropriately to invoke the CSIR Plan. Several industry Breaches have resulted in increased impact to the victim organization due to the miss-handling of detection events which were ignored or not properly routed to the organization’s CSIR Team... |
Table des matières
- Cover image
- Title page
- Table of Contents
- Copyright
- About the Author
- About the Contributors
- Acknowledgments
- Chapter 1: An Overview of Data Breaches
- Chapter 2: Preparing to Develop a Computer Security Incident Response Plan
- Chapter 3: Developing a Computer Security Incident Response Plan
- Chapter 4: Qualifying and Investigating a Breach
- Chapter 5: Containing a Breach
- Chapter 6: Precisely Determining the Scope of a Breach
- Chapter 7: Communicating Before, During and After a Breach
- Chapter 8: Restoring Trust and Business Services After a Breach
- Chapter 9: Preparing for Breach Litigation
- Appendix
- Index