
CompTIA CySA+ Study Guide
Mike Chapple, David Seidl
- English
- ePUB (disponibile sull'app)
- Disponibile su iOS e Android
CompTIA CySA+ Study Guide
Mike Chapple, David Seidl
Informazioni sul libro
This updated study guide by two security experts will help you prepare for the CompTIA CySA+ certification exam. Position yourself for success with coverage of crucial security topics!
Where can you find 100% coverage of the revised CompTIA Cybersecurity Analyst+ (CySA+) exam objectives? It's all in the CompTIA CySA+ Study Guide Exam CS0-002, Second Edition! This guide provides clear and concise information on crucial security topics. You'll be able to gain insight from practical, real-world examples, plus chapter reviews and exam highlights. Turn to this comprehensive resource to gain authoritative coverage of a range of security subject areas.
- Review threat and vulnerability management topics
- Expand your knowledge of software and systems security
- Gain greater understanding of security operations and monitoring
- Study incident response information
- Get guidance on compliance and assessment
The CompTIA CySA+ Study Guide, Second Edition connects you to useful study tools that help you prepare for the exam. Gain confidence by using its interactive online test bank with hundreds of bonus practice questions, electronic flashcards, and a searchable glossary of key cybersecurity terms. You also get access to hands-on labs and have the opportunity to create a cybersecurity toolkit.
Leading security experts, Mike Chapple and David Seidl, wrote this valuable guide to help you prepare to be CompTIA Security+ certified. If you're an IT professional who has earned your CompTIA Security+ certification, success on the CySA+ (Cybersecurity Analyst) exam stands as an impressive addition to your professional credentials. Preparing and taking the CS0-002exam can also help you plan for advanced certifications, such as the CompTIA Advanced Security Practitioner (CASP+).
Domande frequenti
Informazioni
Chapter 1
Today's Cybersecurity Analyst
- Domain 3.0: Security Operations and Monitoring
- 3.4 Compare and contrast automation concepts and technologies.
- Machine Learning
- 3.4 Compare and contrast automation concepts and technologies.
- Domain 5.0: Compliance and Assessment
- 5.1 Understand the importance of data privacy and protection.
- Privacy vs. Security
- 5.1 Understand the importance of data privacy and protection.
Cybersecurity Objectives
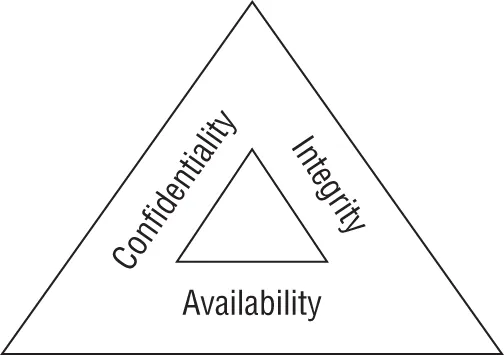
Privacy vs. Security

Exam Note
- Management says that the organization should document its privacy practices in a privacy policy and related documents.
- Notice says that the organization should notify individuals about its privacy practices and inform individuals of the type of information that it collects and how that information is used.
- Choice and consent says that the organization should obtain the direct consent of individuals for the storage, use, and sharing of PII.
- Collection says that the organization should collect PII only for the purposes identified in the notice and consented to by the individual.
- Use, retention, and disposal says that the organization should only use information for identified purposes and may not use information collected for one stated purpose for any other nondisclosed purpose.
- Access says that the organizatio...