
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Financial Forensics Body of Knowledge
About This Book
The definitive, must-have guide for the forensic accounting professional
Financial Forensics Body of Knowledge is the unique, innovative, and definitive guide and technical reference work for the financial forensics and/or forensic accounting professional, including nearly 300 forensic tools, techniques, methods and methodologies apply to virtually all civil, criminal and dispute matters. Many of the tools have never before been published.
It defines the profession: " The Art & Science of Investigating People & Money. "
It defines Forensic Operators: "…financial forensics-capable personnel… possess unique and specific skills, knowledge, experience, education, training, and integrity to function in the financial forensics discipline."
It defines why: " If you understand financial forensics you understand fraud, but not vice versa " by applying financial forensics to all aspects of the financial community.
It contains a book-within-a-book Companion Section for financial valuation and litigation specialists.
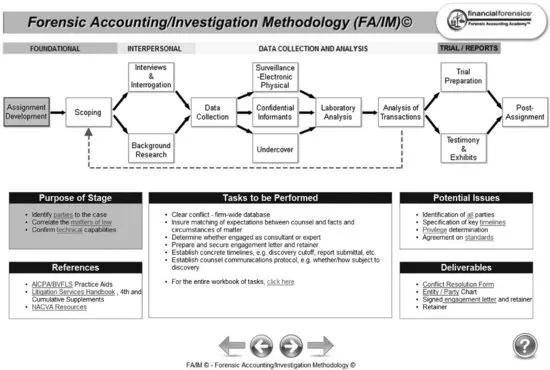
It defines foundational financial forensics/forensic accounting methodologies: FAIM, Forensic Accounting Investigation Methodology, ICE/SCORE, CICO, APD, forensic lexicology, and others.
It contains a Reader Lookup Table that permits everyone in the financial community to immediately focus on the pertinent issues.
Frequently asked questions
- Identify all parties in the matter, internal and external. This includes, but is not limited to: plaintiff and defendant, petitioner and respondent, prosecutor and defendant, claimant and disputant, etc., including legal and regulatory parties.
- Correlate the matters of law, as applicable.
- Establish technical requirements.
- Uniquely identify the assignment with a client or case number or both.
- Search, for example, the Internet for pertinent technical reference sources.
- Develop a list of required sources.
- Compare required sources against currently available sources.
- Acquire sources not otherwise available.
- All forensic operators
www.financialforensicsacademy.com
www.fjc.gov- “Reference Manual on Scientific Evidence,” Reference Guide on Economic Losses in Damages Awards, by Mark A. Allen, Robert E. Hall and Victoria A. Lazear.
- CPA forensic operators
www.financialforensicsacademy.com
- All forensic operators
- Financial Forensics Body of Knowledge, published by John Wiley & Sons.
- CPA forensic operators
- Litigation Services Handbook: The Role of the Financial Expert, 4th ed., published by John Wiley & Sons. Also, earlier editions and supplements contain significant additional material.
- Initiate full-and-false inclusion1
The full-and-false inclusion technique is foundational to financial forensics yet is foreign to many forensic operators and thus routinely overlooked. It is the single most important element of financial forensics yet is unknown or disregarded by untrained forensic operators. The technique is indispensable because it identifies the evidence essential to the forensic assignment at hand.
Full-and-false-inclusion testing serves as the real-time map continuously constructed by the GPS-like capabilities of financial forensics. (See the following chain of custody.) - Initiate chain of custody2
The chain of custody is the fraternal twin of full-and-false inclusion. The term is familiar to forensic operators with criminal investigation backgrounds. Chain of custody likewise applies in civil and mere dispute matters just as it applies in criminal matters. (See full-and-false inclusion, above.) - Formally clear conflict.
- Confirm the expectations of the responsible party(s). This could include a testimony role, consulting role, advisory role, or other capacity.
- Confirm the applicable laws, jurisdiction, regulations, precedent, and other requirements to ensure compliance.
- Confirm internal technical capabilities or alternatively, identify technical assistance, or initiate specific training.
- Search for pertinent technical reference sources via, for example, the Internet.
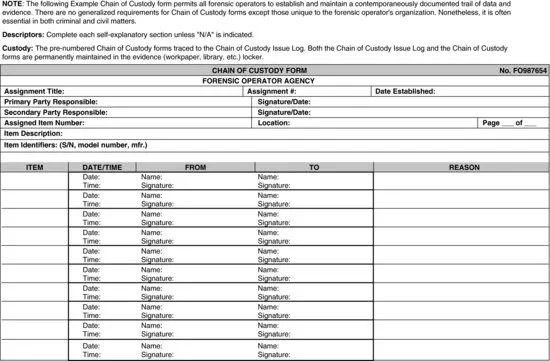
Table of contents
- Cover
- Series
- Title Page
- Copyright
- Dedication
- Preface
- Acknowledgments
- Introduction
- PART One: Financial Forensics Tools, Techniques, Methods, and Methodologies
- PART Two: Financial Forensics Special Topics
- APPENDIX: Forensic Inventory
- Bibliography
- About the Authors and Contributors
- Index