
eBook - ePub
Computer Architecture and Security
Fundamentals of Designing Secure Computer Systems
Shuangbao Paul Wang, Robert S. Ledley
This is a test
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Computer Architecture and Security
Fundamentals of Designing Secure Computer Systems
Shuangbao Paul Wang, Robert S. Ledley
Book details
Book preview
Table of contents
Citations
About This Book
The first book to introduce computer architecture for security and provide the tools to implement secure computer systems
This book provides the fundamentals of computer architecture for security. It covers a wide range of computer hardware, system software and data concepts from a security perspective. It is essential for computer science and security professionals to understand both hardware and software security solutions to survive in the workplace.
- Examination of memory, CPU architecture and system implementation
- Discussion of computer buses and a dual-port bus interface
- Examples cover a board spectrum of hardware and software systems
- Design and implementation of a patent-pending secure computer system
- Includes the latest patent-pending technologies in architecture security
- Placement of computers in a security fulfilled network environment
- Co-authored by the inventor of the modern Computed Tomography (CT) scanner
- Provides website for lecture notes, security tools and latest updates
Frequently asked questions
How do I cancel my subscription?
Can/how do I download books?
At the moment all of our mobile-responsive ePub books are available to download via the app. Most of our PDFs are also available to download and we're working on making the final remaining ones downloadable now. Learn more here.
What is the difference between the pricing plans?
Both plans give you full access to the library and all of Perlego’s features. The only differences are the price and subscription period: With the annual plan you’ll save around 30% compared to 12 months on the monthly plan.
What is Perlego?
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Do you support text-to-speech?
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Is Computer Architecture and Security an online PDF/ePUB?
Yes, you can access Computer Architecture and Security by Shuangbao Paul Wang, Robert S. Ledley in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Engineering. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Introduction to Computer Architecture and Security
A Computer is composed of a number of different components:
Hardware: Computer hardware processes information by executing instructions, storing data, moving data among input and output devices, and transmitting and receiving information to and from remote network locations.
Software: Software consists of system software and application software or programs. Operating Systems such as Windows, UNIX/Linux and Snow Leopard are system software. Word, Firefox browser and iTunes are examples of application software.
Network: The network communication component is responsible for sending and receiving information and data through local area network or wireless connections.
Data: is the fundamental representation of information and facts but usually formatted in a special way. All software is divided into two categories: data and programs. Programs are a collection of instructions for manipulating data.
Figure 1.1 shows a view of a computer system from a user perspective. Here a computer system no longer looks like an onion as traditional textbooks used to represent. Instead, a network component (including hardware and software) is added as a highway for data flowing in and out of the computer system.
Figure 1.1 A conceptual diagram of a common computer system
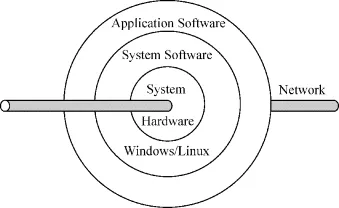
Computer architecture is to study how to design computer systems. It includes all components: the central processing unit (CPU), computer memory and storage, input and output devices (I/O), and network components.
Since the invention of the Internet, computer systems are no longer standalone machines. The traditional “computing” concept of the single machine model is fading away. For most users, information exchange has taken an important role in everyday computer uses.
As computer systems expose themselves over the Internet, the threat to computer systems has grown greater and greater. To protect a computer system (hardware, software, network, and data) from attacks, people have developed many counter-attack techniques such as firewalls, intrusion detection systems, user authentications, data encryptions and so on.
Despite the numerous efforts to prevent attacks, the threat to computer systems is far from over. Computer compromises and data bleach are still very common. If you look back to those counter-attack techniques, most of the detection systems are based on passive techniques. They only work after attacks have taken place.
A firewall by its name is a wall to prevent fire from spreading. On the other hand, it also likes a dam or levee to prevent flood. People can build a dam or levee high enough to protect against flood. However nobody can predict how high the water level will be. The 2005 New Orleans levee leak caused by Katrina is an example of this.
In medicine, people spent billions of dollars to develop new drugs to cure illness. However ancient Chinese people study how to eat well and exercise well to prevent illness. This is the same as now the so-called prevention medicine. If we apply the same mechanism to computer systems, we draw the conclusion that we not only need to build firewalls, more importantly we need to develop computer systems that are immune from attacks.
In early 2005, a US patent was filed to propose new technology that can prevent hackers from getting information stored in computer systems. The technology has drawn the attention of industry, academia, as well as government.
Figure 1.2 shows a conceptual diagram of the proposed secured computer system. Note that in addition to the traditional hardware and software, the system added an additional layer. It is like a sandbox that “separates” the computer system from the outside world. In this book, we call it a virtual semi-conductor or semi “network conductor.” It allows the computer operator to control information and data access so that hackers are no longer able to steal data from the computer system. We will discuss this in more detail in the following chapters.
Figure 1.2 A conceptual diagram of a secured computer system
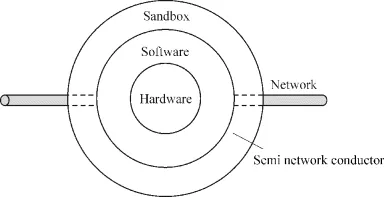
Computer Architecture and Security will teach you how to design secured computer systems. It includes information on how to secure central processing unit (CPU) memory, buses, input/output interfaces. Moreover, the book explains how to secure computer architecture as a whole so that modern computers can be built on the new architecture free of data breaches.
1.1 History of Computer Systems
Computers originally mean to compute or to calculate. The earliest computing devices date back more than two thousand years. The abacus (second century BC) which was introduced in China is one of them.
Blaise Pascal, a renowned French scientist and philosopher, invented a mechanical adding machine in 1645. Gottfried Leibniz invented the first calculator in 1694. The multiplication could be performed by repeated turns of a handle, and by shifting the position of the carriage relative to the accumulator. In December 26, 1837, Charles Babbage proposed a calculating engine that is capable of solving mathematical problems including addition, subtraction, multiplication, division, and finding the square root.
Herman Hollerith, a German-American statistician and the founder of the company that became IBM, developed a punched-card electric tabulating machine in 1889. The first program-controlled computing machine is the German machine Z3 which was developed in 1941. Mark-I, also known as IBM automatic sequence-controlled calculator, was developed by Howard Aiken at Harvard University in 1944. The Electronic Numerical Integrator and Calculator (ENIAC) was developed in May 1943. The machine was used to calculate bomb trajectories and to develop hydrogen bombs. It was not a stored-program machine, a key way to distinguish between earlier computing devices and modern computers.
The final step toward developing a modern computer was characterized as follows:
- General-purpose. The computer can be used by anybody in any domain.
- Electronic. The computer is controlled by electronic signals instead of mechanical devices.
- Stored-program. Programs are stored in its internal memory so they can run automatically without much human interaction.
- Computation. The computer can take numerical quantities to compute.
There are other features such as it has the ability for a program to read and modify itself during the course of a computation, using registers to store temporary data, indirect addressing and so on.
Professor John von Neumann, of the Institute for Advanced Study at Princeton University, one of the leading mathematicians of his time, developed a stored-program electronic computer in 1945. It is generally accepted that the first documented discussion of the advantages of using just one large internal memory, in which instructions as well as data could be held, was the draft report on EDVAC written by Neumann, dated June 30, 1945. (The full report is available on www.wiley.com/go/wang/comp_arch)
Since 1945, the Neumann computer architecture has been the foundation of modern computers, a CPU, memory and storage, input/output devices, a bus with address, data and control signals that connects the components.
Early computers were made of vacuum tubes. They are large and consume a great deal of energy. During the mid 1950s to early 1960s, solid-state transistors were used and in the mid 1960s to early 1970s, integrated circuits (IC) were used in computers. Minicomputer PDP-11 in 1970, supercomputer CDC (Cray) and mainframe IBM 360 are some examples of computers during that time. Intel 8080 and Zilog Z80 are 8-bit processors made of large-scale IC. Later, Intel's 8086 (16-bit), 80286 (16-bit) and Motorola's 68000 (16/32-bit) made of very large-scale IC (VLSI) opened the era of so-called microcomputers.
The uses of microcomputers were greatly increased by the software development. UNIX and MS-DOS later became Windows are still being used as operating systems (system software) today. Word processing, spreadsheets and databases, and many other application programs help people to carry out office works. Fortran, C, Java and many other computer languages assist software developers to program new software applications.
Now computers have grown from single-chip processors to multiple processors (cores) such as dual-cores, quad-cores and eight-cores in the near future. On the other hand, smaller devices or handheld devices such as pads and smart cell phones have the ability to handle information and data needs for many people.
With virtualization technology, a “guest” or virtual operating system may run as a process on a “host” or physical computer system. It is often considered as “computers on a computer.”
Now, network connections have become an essential part of a computer system. People have developed many ways to enhance the security of computer architecture from protecting CPU and memory to building “firewalls” to detect intrusions. The study of computer architecture with security as a whole was not started until recently. This book aims to provide readers with the latest developments in designing modern computer systems that are immune from attacks.
1.1.1 Timeline of Computer History
The timeline of computer history (Computer History, 2012) covers the most important advancements in computer research and development during 1939 to 1988.
1939: Hewlett-Packard is founded. David Packard and Bill Hewlett founded Hewlett-Packard in a Palo Alto, California garage. Their first product was the HP 200A Audio Oscillator, which rapidly became a popular piece of test equipment for engineers. Walt Disney Pictures ordered eight of the 200B models to use as sound effects generators for the 1940 movie “Fantasia.”
1940: The Complex Number Calculator (CNC) is completed. In 1939, Bell Telephone Laboratories completed this calculator, designed by researcher George Stibitz. In 1940, Stibitz demonstrated the CNC at an American Mathematical Society conference held at Dartmouth College. Stibitz stunned the group by performing calculations remotely on the CNC (located in New York City) using a Teletype connected via special telephone lines. This is considered to be the first demonstration of remote access computing.
1941: Konrad Zuse finishes the Z3 computer. The Z3 was an early computer built by German engineer Konrad Zuse working in complete isolation from developments elsewhere. Using 2,300 relays, the Z3 used floating point binary arithmetic and had a 22-bit word length. The original Z3 was destroyed in a bombing raid of Berlin in late 1943. However, Zuse later supervised a reconstruction of the Z3 in the 1960s which is currently on display at the Deutsches Museum in Munich.
1942: The Atanasoff-Berry Computer (ABC) is completed. After successfully demonstrating a proof-of-concept prototype in 1939, Atanasoff received funds to build the full-scale machine. Built at Iowa State College (now University), the ABC was designed and built by Professor John Vincent Atanasoff and graduate student Cliff Berry between 1939 and 1942. The ABC was at the center of a patent dispute relating to the invention of the computer, which was resolved in 1973 when it was shown that ENIAC co-designer John Mauchly had come to examine the ABC shortly after it became functional.
The legal result was a landmark: Atanasoff was declared the originator of several basic computer ideas, but the computer as a concept was declared un-patentable and thus was freely open to all. This result has been referred to as the “dis-invention of the computer.” A full-scale reconstruction of the ABC was completed in 1997 and proved that the ABC machine functioned as Atanasoff had claimed.
1943: Project Whirlwind begins. During World War II, the US Navy approached the Massachusetts Institute of Technology (MIT) about building a flight simulator to train bomber crews. The team first built a large analog computer, but found it inaccurate and inflexible. After design...
Table of contents
- Cover
- Information Security Series
- Title Page
- Copyright
- Dedication
- About the Authors
- Preface
- Acknowledgements
- Chapter 1: Introduction to Computer Architecture and Security
- Chapter 2: Digital Logic Design
- Chapter 3: Computer Memory and Storage
- Chapter 4: Bus and Interconnection
- Chapter 5: I/O and Network Interface
- Chapter 6: Central Processing Unit
- Chapter 7: Advanced Computer Architecture
- Chapter 8: Assembly Language and Operating Systems
- Chapter 9: TCP/IP and Internet
- Chapter 10: Design and Implementation: Modifying Neumann Architecture
- Appendix A: Digital Logic Simulators
- Appendix B: Computer Security Tools
- Appendix C: Patent Application: Intrusion-Free Computer Architecture for Information and Data Security
- Index
Citation styles for Computer Architecture and Security
APA 6 Citation
Wang, S. P., & Ledley, R. (2012). Computer Architecture and Security (1st ed.). Wiley. Retrieved from https://www.perlego.com/book/1001952/computer-architecture-and-security-fundamentals-of-designing-secure-computer-systems-pdf (Original work published 2012)
Chicago Citation
Wang, Shuangbao Paul, and Robert Ledley. (2012) 2012. Computer Architecture and Security. 1st ed. Wiley. https://www.perlego.com/book/1001952/computer-architecture-and-security-fundamentals-of-designing-secure-computer-systems-pdf.
Harvard Citation
Wang, S. P. and Ledley, R. (2012) Computer Architecture and Security. 1st edn. Wiley. Available at: https://www.perlego.com/book/1001952/computer-architecture-and-security-fundamentals-of-designing-secure-computer-systems-pdf (Accessed: 14 October 2022).
MLA 7 Citation
Wang, Shuangbao Paul, and Robert Ledley. Computer Architecture and Security. 1st ed. Wiley, 2012. Web. 14 Oct. 2022.