
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Securing SCADA Systems
About this book
- Bestselling author Ron Krutz once again demonstrates his ability to make difficult security topics approachable with this first in-depth look at SCADA (Supervisory Control And Data Acquisition) systems
- Krutz discusses the harsh reality that natural gas pipelines, nuclear plants, water systems, oil refineries, and other industrial facilities are vulnerable to a terrorist or disgruntled employee causing lethal accidents and millions of dollars of damage-and what can be done to prevent this from happening
- Examines SCADA system threats and vulnerabilities, the emergence of protocol standards, and how security controls can be applied to ensure the safety and security of our national infrastructure assets
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
CHAPTER 1
What Is a SCADA System?
Supervisory control and data acquisition (SCADA) systems are vital components of most nations’ critical infrastructures. They control pipelines, water and transportation systems, utilities, refineries, chemical plants, and a wide variety of manufacturing operations.
SCADA provides management with real-time data on production operations, implements more efficient control paradigms, improves plant and personnel safety, and reduces costs of operation. These benefits are made possible by the use of standard hardware and software in SCADA systems combined with improved communication protocols and increased connectivity to outside networks, including the Internet. However, these benefits are acquired at the price of increased vulnerability to attacks or erroneous actions from a variety of external and internal sources.
This chapter explores the evolution of SCADA systems, their characteristics, functions, typical applications, and general security issues.
History of Critical Infrastructure Directives
In 1996, Presidential Executive Order 13010 established the President’s Commission on Critical Infrastructure Protection (PCCIP) to explore means to address the vulnerabilities in the U.S. critical infrastructure. Internet-based attacks and physical attacks were two of the major concerns that were to be considered by the committee. As a result of the committee’s efforts, the FBI National Infrastructure Protection Center (NIPC) and the Critical Infrastructure Assurance Office (CIAO) were established in May 1998 by Presidential Decision Directive 63 (PDD 63). The main function of the NIPC was to conduct investigations relating to attacks against the critical infrastructure and issue associated warnings, when appropriate. The CIAO was designated as the main entity for managing the U.S. critical infrastructure protection (CIP) efforts, including coordinating the efforts of the different commercial and industrial entities affected.
As a consequence of the CIAO activities, the Communications and Information Sector Working Group (CISWG) was established with the mission to “promote information sharing and coordinated action to mitigate CIP risk and vulnerabilities in all levels of the Information and Communications (I&C) Sector.” In addition, companies in eight critical industry sectors established a related entity, the Partnership for Critical Infrastructure Security (PCIS). The PCIS was formed to mitigate the vulnerabilities caused by the interdependence of many commercial and industrial organizations.
In response to the September 11, 2001 attacks, the president, on October 8, 2001, established the President’s Critical Infrastructure Board (PCIB), the Office of Homeland Security, and the Homeland Security Council with Executive Order 13228. Also in October 2001, the USA Patriot Act was passed to provide U.S. government law enforcement agencies with increased authority to perform searches, monitor Internet communications, and conduct investigations.
On the economic front, in February 2003, President George W. Bush appointed the 30-member National Infrastructure Advisory Council (NIAC) from the private sector, state and local governments, and academia. NIAC’s charter is to advise the president on information system security issues related to the various U.S. business sectors. Around the same time, President Bush issued Executive Order 1327, which discontinued the PCIB. This action was necessary because the functions of the PCIB were assumed by the Department of Homeland Security.
President Bush, in December 2003, announced Homeland Security Presidential Directives HSPD-7 and HSPD-8. HSPD-7 is a modification of PDD 63 that delineates the national policy and responsibilities of the executive departments, government corporations as defined by 5 U.S.C. 103(1), and the United States Postal Service relating to protection of the critical infrastructure. These are the executive departments:
- ■ The Department of Homeland Security
- ■ The Department of State
- ■ The Department of the Treasury
- ■ The Department of Defense
- ■ The Department of Justice
- ■ The Department of the Interior
- ■ The Department of Agriculture
- ■ The Department of Commerce
- ■ The Department of Labor
- ■ The Department of Housing and Urban Development
- ■ The Department of Transportation
- ■ The Department of Energy
- ■ The Department of Education
- ■ The Department of Veterans Affairs
HSPD-8 focuses on preparedness to prevent and respond to domestic terror attacks, disasters, and emergencies.
Figure 1-1 illustrates the timeline of the major activities relating to CIP in the United States.
SCADA System Evolution, Definitions, and Basic Architecture
Supervisory control and data acquisition (SCADA) means different things to different people, depending on their backgrounds and perspectives. Therefore, it is important to review the evolution of SCADA and its definition as understood by professionals and practitioners in the field.
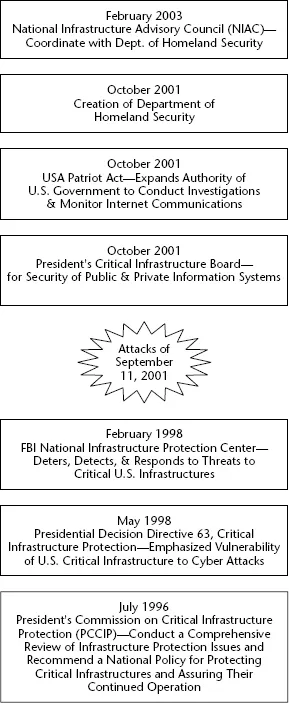
Figure 1-1 Timeline of U.S. critical infrastructure protection activities
SCADA Evolution
The scope of SCADA has evolved from its beginnings in the 1960s. The advent of low-cost minicomputers such as the Digital Equipment Corporation PDP-8 and PDP-11 made computer control of process and manufacturing operations feasible. Programmable logic controllers (PLCs) progressed simultaneously. These latter devices implemented traditional relay ladder logic to control industrial processes. PLCs appealed to traditional control engineers who were accustomed to programming relay logic and who did not want to learn programming languages and operating systems. When microcomputers were developed, they were programmed and packaged to emulate PLCs in function, programming, and operation. In fact, competition developed between the two approaches and continues to this day.
Initially, control systems were confined to a particular plant. The associated control devices were local to the plant and not connected to an external network. The early control systems consisted of a central minicomputer or PLC that communicated with local controllers that interfaced with motors, pumps, valves, switches, sensors, and so on. Figure 1-2 illustrates this architecture.
This architecture is sometimes referred to as a distributed control system. Such systems are generally confined to locations close to each other, normally use a high-speed local network, and usually involve closed loop control. As a necessary requirement for the operation of these systems, companies and vendors developed their own communication protocols, many of which were proprietary.
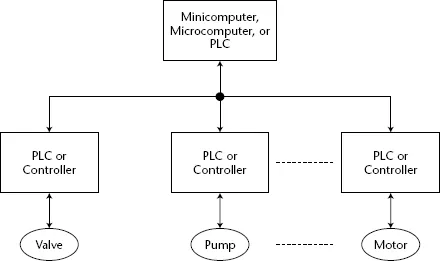
Figure 1-2 Typical local control system
As the technical capabilities of computers, operating systems, and networks improved, organizational management pushed for increased knowledge of the real-time status of remote plant operations. Also, in organizations with a number of geographically separated operations, remote data acquisition, control, and maintenance became increasingly attractive ...
Table of contents
- Cover
- Table of Contents
- Title
- Copyright
- Dedication
- About the Author
- Credits
- Acknowledgments
- Introduction
- CHAPTER 1: What Is a SCADA System?
- CHAPTER 2: SCADA Systems in the Critical Infrastructure
- CHAPTER 3: The Evolution of SCADA Protocols
- CHAPTER 4: SCADA Vulnerabilities and Attacks
- CHAPTER 5: SCADA Security Methods and Techniques
- CHAPTER 6: SCADA Security Standards and Reference Documents
- CHAPTER 7: SCADA Security Management Implementation Issues and Guidelines
- CHAPTER 8: Where We Stand Today
- APPENDIX A: Acronyms and Abbreviations
- APPENDIX B: System Protection Profile — Industrial Control Systems
- APPENDIX C: Bibliography
- Index
- End User License Agreement
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Securing SCADA Systems by Ronald L. Krutz in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.