
Making Technology Investments Profitable
ROI Road Map from Business Case to Value Realization
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Making Technology Investments Profitable
ROI Road Map from Business Case to Value Realization
About This Book
A guide to getting the crucial business case right?every time
Showing professionals how to calculate the value of typical budgeting and funding requests quickly and easily, Making Technology Investments Profitable, Second Edition applies the "Value Realization" process, using proven strategies that maximize the business payoff from IT projects. Filled with case studies, this innovative book enables managers to confidently quantify, in a matter of minutes, the true business value of funding a desired project.
- New edition explains how to proactively manage the conversion of a business case's value promise to its value realization
- Includes dozens of new case studies on realizing maximum value from IT enabled investments from various industries and around the world
- New checklists and tables
- A dedicated Web site containing additional material, case studies, chat rooms, and blogs on the value-realization process
The Second Edition provides senior executives, project managers, and technical staff with new insights on how to get the crucial business case right, while also explaining how to proactively manage the conversion of the business case's value promise into the value reality of a completed project.
Frequently asked questions
Information
- Hidden benefits never discovered when building the business case
- Compelling benefits discarded by hyperconservative managers who misunderstand enterprise needs
- Valid benefits rejected due to poor explanations in the business case
- Omission of crucial intangible (nonmonetary) benefits that can make or break an investment’s appeal
- Value that never sees the light of day because no one is held accountable to make it happen
- Design decisions that unintentionally optimize low value capabilities
- Scope control decisions that ignore the value implications of choices available
- Rollout priorities that disregard impacts on value achievement
- For an enterprise, needed market share gains are undermined by disappointing customer relationship management (CRM) system upgrades. Massive defections of key customers are triggered by fumbled Web-based customer service implementations.
- For an industry, entrenched leaders can fall to new entrants. For example, a lack of IT vision and commitment hastened the forfeiture of many retailers’ leading market positions to IT-empowered Wal-Mart.
- Approve IT programs that should have been rejected
- Reject IT programs that should have been approved
- Overlook program opportunities that should have been proposed
- Approve good programs that fail during implementation
- Program cost overruns are thought to be due to poor expense control during implementation. In reality, overruns may be the consequence of a deeper problem, such as misstated cost assumptions in the business case during approval of program funding.
- Missed program deadlines are said to result from unexpected expansion of the program’s scope, which in turn is attributed to lax enforcement of agreed-upon program boundaries. Deeper analysis indicates, however, that the real root cause is the fuzzy program boundaries that were allowed to slip by in the original cost-benefit justification.
- Slower than expected field adoption rates for a new initiative are blamed on technology hiccups. Closer assessments uncover that field management hesitated to embrace the new solution due to lack of buy-in to the business value touted by senior leaders.
- Lower than expected worker productivity increases are thought to stem from inadequate training on new systems. A more thorough investigation shows that the real problem is lack of management and worker motivation. The business case never identified “What’s in it for me?” for these key stakeholders during the program’s initial approval.
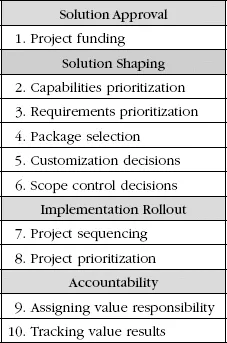
Table of contents
- Cover
- Contents
- Title
- Copyright
- Dedication
- Preface to the Second Edition
- Acknowledgments
- Introduction
- Part One: Understanding Value Leaks: Major Threats to Program Success
- Part Two: Flushing Out Value Leaks: A Guided Journey
- Part Three: Plugging Value Leaks: Success Begins Here
- Part Four: Getting the Business Case Right
- Appendix: Sample Business Case
- Glossary
- Bibliography
- About the Author
- Index