
IoT Security
Advances in Authentication
- English
- ePUB (mobile friendly)
- Available on iOS & Android
IoT Security
Advances in Authentication
About this book
An up-to-date guide to an overview of authentication in the Internet of Things (IoT)
The Internet of things (IoT) is the network of the countless physical devices that have the possibility to connect and exchange data. Among the various security requirements, authentication to the IoT is the first step to prevent the impact of attackers. IoT Security offers an important guide into the development of the many authentication mechanisms that provide IoT authentication at various levels such as user level, device level and network level.
The book covers a wide range of topics including an overview of IoT and addresses in detail the security challenges at every layer by considering both the technologies and the architecture used. The authors—noted experts on the topic—provide solutions for remediation of compromised security, as well as methods for risk mitigation, and offer suggestions for prevention and improvement. In addition, IoT Security offers a variety of illustrative use cases. This important book:
- Offers an authoritative reference designed for use by all IoT stakeholders
- Includes information for securing devices at the user, device, and network levels
- Contains a classification of existing vulnerabilities
- Written by an international group of experts on the topic
- Provides a guide to the most current information available on IoT security
Written for network operators, cloud operators, IoT device manufacturers, IoT device users, wireless users, IoT standardization organizations, and security solution developers, IoT Security is an essential guide that contains information on security features, including underlying networks, architectures, and security requirements.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part I
IoT Overview
1
Introduction to IoT
Abstract
The successful existence of the Internet, its proven potential to cater to day‐to‐day needs of people from all walks of life and its indispensability to society at large, together have propelled the evolution of the current Internet to the next level termed as the Internet of Things (IoT). As a witness to the dawn of IoT revolution, what we are experiencing (and will continue in to do so in the near future at an exponential and astonishing rate) is the intelligent presence and communication of the physical objects or things around us with themselves (M2M) and/or with humans (M2H). Emergence of such a kind of pervasive inter‐networking ecosystem has enormous scope in terms of market growth and applications which have (to some extent) and will prove with greater force its efficacy to improve quality of life. Though it is bit early to precisely define the depth of coverage and the long‐term impact of IoT applications, nevertheless particularly in domains like healthcare, agriculture, city and home/office automation, industrial and energy management, etc. the immediate applications of IoT are easily conceivable. For realization and rapid development of such IoT applications, formal establishment of IoT architecture and standardization of related protocol suites are vital as they ensure co‐existence and co‐operation of cross‐vendor devices as well as applications. Nevertheless, as with any other hyped research area, IoT has also become victim of its own success and hitherto no one architecture is globally accepted with a common consensus.In the midst of this, this chapter intends to introduce IoT in a pedagogical manner to the readers. More specifically, the chapter guides the reader through the evolution of IoT, discusses the pertinent taxonomy and proposed architectures, probes the various efforts for standardization of IoT and illustrates some of the popular applications of IoT. While dealing with promising IoT applications, the chapter presents a comprehensive view comprised of the constituent components and major stakeholders to fit‐in, characteristics and key factors to focus, enabling technologies to leverage and categorize each application to understand the various viewpoints.
1.1 Introduction
1.1.1 Evolution of IoT
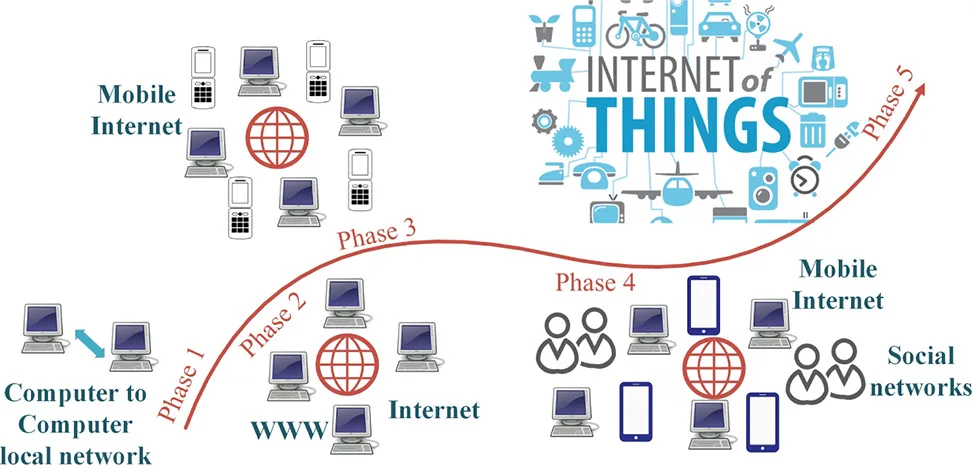
Table of contents
- Cover
- Table of Contents
- About the Editors
- List of Contributors
- Preface
- Acknowledgments
- Part I: IoT Overview
- Part II: IoT Network and Communication Authentication
- Part III: IoT User Level Authentication
- Part IV: IoT Device Level Authentication
- Part V: IoT Use Cases and Implementations
- Index
- End User License Agreement
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app