
eBook - ePub
Advances of DNA Computing in Cryptography
- 181 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Advances of DNA Computing in Cryptography
About this book
This book discusses the current technologies of cryptography using DNA computing. Various chapters of the book will discuss the basic concepts of cryptography, steganography, basic concepts of DNA and DNA computing, approaches of DNA computing in cryptography, security attacks, practical implementaion of DNA computing, applications of DNA computing in the cloud computing environment, applications of DNA computing for big data, etc. It provides a judicious mix of concepts, solved examples and real life case studies.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1
Introduction of DNA Computing in Cryptography
Suyel Namasudra and Ganesh Chandra Deka
CONTENTS
1.1 Introduction
1.1.1 Key Management in Cryptography
1.2 Steganography
1.3 Background Studies of DNA
1.4 DNA Computing
1.4.1 Why DNA Computing?
1.5 DNA Computing in Cryptography
1.5.1 Polymerase Chain Reaction
1.5.2 DNA-Based Steganography
1.5.3 DNA-Based Chip Technology
1.6 Future Research Work Directions
1.7 Conclusions
Key Terms and Definitions
References
References for Advanced/Further Reading
1.1 Introduction
The security of data has become more and more important as data are shared through the cloud in heterogeneous devices (Deka and Das, 2014; Namasudra, 2017, 2018; Namasudra et al., 2017a; Namasudra et al., 2014). Cryptography is the technique of secret writing (Willett, 1982; Lin, 1998). The main goal of cryptography is to transmit data or messages (files) between the sender and receiver over an untrusted medium in such a manner that an attacker or malicious user is unable to read the original data content. It can also be used for the authentication of customers and users.
In cryptography, the plaintext refers to an ordinary readable data or message. The encryption process takes plaintext as input and generates ciphertext as output by using a secret key and encryption algorithm. The process of recovering the plaintext from the ciphertext by using the secret key is known as decryption. Fundamentally, there are two types of cryptosystems, based on how the encryption and decryption processes are carried out:
1. Symmetric key encryption
2. Asymmetric key encryption
The main dissimilarity between these two cryptographic systems is the use of the decryption and encryption keys. Both these keys are strongly associated in any cryptosystem.
In symmetric key encryption, the secret key is shared between the sender and receiver, and the encryption and decryption processes are executed by using the same key (Kumar and Wollinger, 2006; Schneier, 1996). Here, the length of the key is small, so the encryption and decryption processes are fast and use less computer processing power. In the 1970s, all cryptosystems used symmetric key encryption. Nowadays, it is still used in many cryptosystems. Some examples of symmetric key encryption are Digital Encryption Standard (DES), IDEA, BLOWFISH and Triple-DES (3DES). There are two main types of symmetric key encryption:
1. Stream cipher, where the bytes or digits of a message are encrypted one at a time.
2. Block cipher, where a number of bits are taken as a single unit, and then this unit is encrypted. Here, plaintext is padded to make it multiple block size. In block cipher, 64-bit blocks are commonly used.
However, symmetric encryption requires establishing a secure key-exchange mechanism, and the sender and receiver have to trust each other. Otherwise, they may lose their secret information, and there is always a chance that the key will be given to others. Thus, data may face security issues. Figure 1.1 shows the symmetric key encryption process.
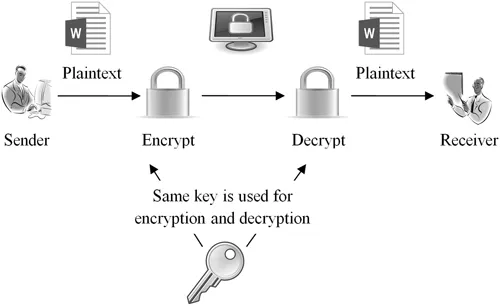
FIGURE 1.1
Symmetric key encryption.
Symmetric key encryption.
Asymmetric key encryption is also known as public key cryptography. Here, different keys or values are used to encrypt and decrypt data or a message, and the process does not require sharing keys between the sender and receiver. The keys are usually large numeric numbers and are mathematically correlated to each other even if they are different. The asymmetric key encryption process was invented in the 20th century because it was necessary to pre-share the secret key between two parties. In this process, every party has a pair of keys:
1. A private key
2. A public key, where one key is utilized at the time of encryption, and the other is utilized at the time of decryption (Katayangi and Murakami, 2001).
Computationally, it is unfeasible that one key could be determined based on another key even though both keys are mathematically correlated, which is the strength of asymmetric key encryption. In addition, the strength of the encryption is associated with the key size, and doubling the key length supports an exponential enhancement of its strength. However, users need to trust the third party for key management, which is one of the challenging issues of asymmetric key encryption. Figure 1.2 shows a block diagram of asymmetric key encryption.
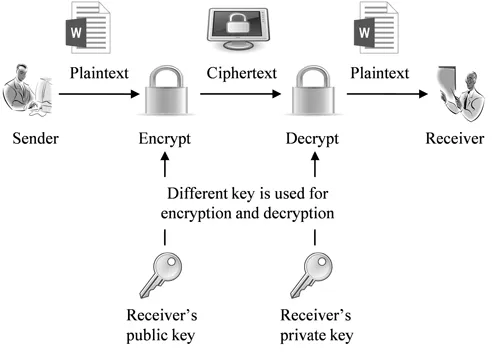
FIGURE 1.2
Asymmetric key encryption.
Asymmetric key encryption.
Some examples of asymmetric key encryption are Secure Shell (SSH), OpenPGP and digital signature. It is also utilized in many online services, such as browsers that require the establishment of a secure or trusted connection over an unsecured or untrusted network.
To create a better cryptosystem, it is preferable to use symmetric algorithms, since they are fast and secure compared to asymmetric algorithms (Knudsen, 1994; de Cannière et al., 2006).
1.1.1 Key Management in Cryptography
Key management is one of the important aspects of any cryptosystem. There are three main steps in key management:
1.Key generation: Key is generated for encryption and decryption.
2.Key revocation: Key is revoked from a user or customer, when s/he is not an authorized user.
3.Key distribution: Key is distributed in a secure way (Chaeikar et al., 2010). This is the most vital step for key management, since in this step, attackers or malicious users try to get the secret key by using an attack.
So, if a strong algorithm is used for key generation, but the key distribution process lacks security, then the security of the whole cryptosystem might be at risk. An algorithm has been proposed to distribute the key in an unsecured medium (Diffie and Hellman, 1976).
The main contributions of this chapter are to present an overview of cryptography and DNA computing. Here, all the basics of cryptography are presented. Background studies of DNA and the applications of DNA computing in the field of cryptography are also discussed in this chapter.
The rest of the chapter is organized into different parts. Section 1.2 discusses steganography. Background studies of DNA are presented in Section 1.3. DNA computing is discussed in Section 1.4. Applications of DNA computing in cryptography are presented in Section 1.5. Future work directions are discussed in Section 1.6. Finally, Section 1.7 concludes the whole chapter.
1.2 Steganography
Steganography is a technique for hiding data. Both steganography and cryptography have common aim but use different approaches. Table 1.1 summarizes the differences between cryptography and steganography.
TABLE 1.1
Steganography and Cryptography
Steganography and Cryptography
| Sl. No. | Steganography | Cryptography |
| 1 | Hides existence of data or information | Changes the content of data |
| 2 | Refers to covering a data or information (Johnson and Jajodia, 1998) | Data or information may not be covered |
| 3 | Embeds data in a carrier | Data are not embedded |
| 4 | A function is used to identify the existence of data | Data are only encrypted by a secret key |
Simmons’ prisoner’s problem is one of the popular illustrations of steganography. According to this example, two criminals want to escape from jail, and they want to discuss their plan without attracting the attention of the police or guards. The only possible way is to communicate with each other by transferring the message or information in a hidden way (Lenti, 2000).
Each method involved in steganography contains an algorithm, which embeds the data or information into a carrier and develops an identifier function that returns the embedded data or information. The function uses a secret key, and this is only shared with or known to the authorized user or customer. The function recovers and identifies the existence of the data or i...
Table of contents
- Cover
- Half-Title
- Title
- Copyright
- Contents
- Preface
- Editors
- Authors
- Contributors
- 1 Introduction of DNA Computing in Cryptography
- 2 Implementation of Public Key Cryptography in DNA Cryptography
- 3 Taxonomy of DNA-Based Security Models
- 4 Novel Data Encryption Scheme Using DNA Computing
- 5 Application of DNA Computing in the Cloud Computing Environment
- 6 Taxonomy of Security Attacks in DNA Computing
- 7 Security, Privacy, Trust, and Anonymity
- 8 DNA Computing Algorithm
- 9 Applications and Future Trends of DNA Computing
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Advances of DNA Computing in Cryptography by Suyel Namasudra, Ganesh Chandra Deka, Suyel Namasudra,Ganesh Chandra Deka in PDF and/or ePUB format, as well as other popular books in Computer Science & Cryptography. We have over one million books available in our catalogue for you to explore.