
- 424 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
Today's network administrators are fully aware of the importance of security; unfortunately, they have neither the time nor the resources to be full-time InfoSec experts. Oftentimes quick, temporary security fixes are the most that can be expected. The majority of security books on the market are also of little help. They are either targeted toward
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Topic
InformaticaSubtopic
Reti di computerChapter 1
Introduction
1.1 Who Is This Book For?
I previously worked for a networking company that specialized in designing and installing Windows NT systems for customers who did not have their own IT staff. I was constantly haunted by our company’s complete lack of security awareness regarding our customer installations. The network to our own company’s Internet connection had absolutely no packet filtering or other security mechanisms of any type installed on our routers—and search as I might, there was no indication of a firewall anywhere on our own network.
When I inquired of management about not consulting with customers about their own network security and the frightful lack of any on our own network, I received an interesting response: “Customers are not interested in paying for security consulting.” Why customers were not interested in paying was explained by management’s response to the second half of my question. “We don’t have a firewall because it is too expensive—and then I’ll have to pay for someone to configure it.”
Today, this laissez-faire attitude toward network security is thankfully becoming increasingly rare. While many network security experts give a knowing nod and an “I told you so!” every time there is another high-profile computer crime—the press has begun to make our jobs a lot easier. No longer are top-secret government agencies the only organizations interested in the state of their network security. Any customer my company consults with, from the smallest SOHO start-up business to Fortune 500 ISPs, now has network security on the top of the priority list.
Despite this awareness and the abundance of press, the task of securing networks has not gotten any easier over the past few years. Increasingly connected networks, cheap high-speed Internet access, and complex applications requirements have made the task of securing networks more complicated than ever before. Network security is becoming more complex because our networks are becoming more complex. Each time a network professional increases the security on his or her network, a network hacker is taking the time to figure out a new weakness to exploit.
This book will help both the novice and experienced network administrator and manager determine the appropriate defenses to incorporate into their network. While network security is complex, the network “bad guys” can be slowed down quite a bit with a thoughtfully laid-out security policy.
I purposefully used the term “slowed down” in the previous paragraph. If you are new to the network security game, here is something to remember: in general, the more money you spend, the more you can secure your network. At the same time, no matter how much money you spend, you will never completely secure your network.
Network security will cost money; but be clear, no matter how much money you spend, you will never have a 100-percent secure network. It is this slight bit of doubt, the wondering what the other guy is doing, that keeps the job interesting for security professionals. While interesting for people like me, this truism creates a particular problem for those attempting to implement their own security policy. How much should I spend on security so that I can secure my network? But how do I know how much “too much” is? In other words, what is the point of diminishing returns for my network security program?
The first section of this book helps to answer this question. We review what steps can be taken in the creation of a security policy This process will help determine how much what we are trying to protect is worth. From that value, we will then examine the various elements that go into implementing the security policy—otherwise known as the security model. This examination will assist us in creating a security policy that will not only satisfy a network security professional, but also make the accounting department happy.
1.2 The Path to Network Security
A secure network is not an accident. Secure networks generally are not the product of random changes, additions, and additional network functionality. While there is no doubt that someone would be able to point to a friend or associate who has a “secure” network that happened to “organically grow” out of years of trial and error and switching things around according to the zodiac, this is really the exception. Secure networks are built out of a solid understanding of how networking works: How does a packet of information get from a client to a remote server? What happens at the server to make it return another packet to the client? How does this return packet of information get back to the client?
A secure network is built from policy. I am the type of person who cringes when I hear the term “policy.” Sometimes, Dilbert-esque policies leave me mystified as to their intent and reason, other than to annoy the average end user. Despite this policy aversion of my own, I am the first to ask a customer to help me create their security policy. This ensures that you and your customer/client/ boss/management all understand what you need to do. A security policy is a broad statement of principle. Once the policy is completed, then the security model can be implemented. This is the step-by-step guide that puts the principle into practice. Chapter 2, “Managing Network Security,” addresses the critical issue of creating a security policy. It also provides critical tips to avoid your transformation into the pointy-haired manager type as well. By creating a policy that has input, is well understood, and is fairly enforced, most of the negative connotations of “policy” will disappear.
In my experience, the most difficult part of creating a security policy is this initial step. This step needs the most participation, the most research, the most input, and the most thought. Done correctly, implementing the security model is a relatively straightforward matter of choosing the hardware, placing it in strategic points in your network, configuring it, and continually testing and monitoring it. Simple enough. Right?
Without a basic understanding of this process, it is difficult to create a system that can reliably secure your network. If you are missing this information or feel that you could stand a refresher, Chapter 3, “The Network Stack and Security,” will be a good place to start. One place that I find even some seasoned security professionals failing is a solid understanding of routing and routing issues. Chapter 3, in addition to the normal presentation of network hardware and protocol operation, such as TCP/IP, also examines some of the more commonly encountered routing protocols and how they can play a part in the secure network.
While there is no shortage of obscure and confusing acronyms, protocol types, hardware, and software vendors to confuse the issue of implementation, for the most part, all of network security only uses about half a dozen different technologies. While the names of who wrote the programs and the decals on the side of the hardware may change, network security uses the same basic ideas over and over again. A series of chapters on access-control, firewalls, VPNs (virtual private networks), and intrusion detection systems cover all of the basics of each technology. Once the basics are reviewed, we then examine how they fit into our network security policy: how do they assist us in creating our security model? It is in these chapters that we will learn the amount and type of protection that each technology affords us and, more importantly, how to wisely invest in the technology to maximize security for minimum cost.
In addition to the material covering the common security technologies, we also examine some network applications and designs that, while not directly related to security, do affect the security of our network through their very operation. Wireless networking—all the rage for its ease of deployment and user friendliness—is one example. How can a wireless network with security that has been demonstrated over and over again to be faulty be part of the “secure” network? We examine our options and explore other applications that need special consideration in Chapters 4–11.
Comparing our security policy with the technologies available to us will then allow us to examine a number of case studies to put all the pieces together. For four networks, ranging from a small SOHO to enterprise-class networks, we examine the process of creating a sample security policy and then build a security model around that policy.
Finally, the book concludes with perhaps the most satisfying element of network security—penetration testing. When you attempt this on someone else’s network, you are considered a criminal; but when you test your own network for vulnerabilities, you are providing valuable insight into your own network because you see it as it is seen by the rest of the world or by others utilizing your internal network. By performing network penetration testing— either through a contracted third party or by yourself— you ensure that the fruits of your labor, starting with the first meeting that discussed security policy, have been worth your time and effort. Chapter 12, “Network Penetration Testing,” discusses the process of testing your own network, points you in the direction of some common tools (which changes frequently) and techniques for penetration testing, and discusses what to expect from a third party if you were to hire them to test the security of your network.
1.3 Who Should Read This Book?
I hope that the primary value of the book will be to those who are entrusted by others to provide network security to their organization, company, or club. Network security is commonly complicated but it does not need to be. By following some commonly known best practices, you can safely secure your network under budget yet still allow yourself a good night’s sleep. This book will show you how.
This text is not intended to serve as a study guide for any security certification. That said, most security certifications have a “common body of knowledge” on which they test. This common body of knowledge may be quite extensive yet not very deep, as in the case of the ICS2 CISSP—or very deep yet not broad, as in the case of the SANS GIAC certification. If you are already a CISSP, you will likely not find much new in terms of information in this text. However, if you are already a CISSP, then you did not purchase this book to use as a study aid. The primary value of this book to those who already hold security certifications is to assist them in the process of working with and educating others who may not have the same level of expertise. If you are in the process of obtaining either of the above security certifications, this book will either instruct or reinforce the most common and critical elements of network security.
This book also does not extensively cover any particular technology or provide detailed configuration steps for each product. In the process of obtaining my own networking certifications, I have a stack of books for each discipline, each of which is taller than my own 6’5” frame. The number of Linux books alone fills a number of bookshelves in my home office. Each of these texts taught me valuable information; however, I find the ones most likely to collect dust are those that provide specific command references for a particular application. Not only does the technology move too fast to keep those books valuable for more than a month, but through the process of reading, consulting, working closely with clients implementing their own security policies and complex network needs, I have come to realize that although the checkboxes may change and the command-line interface or GUI may look different from box to box, what really matters when working with various networking products is knowing how the technology works and why I would be checking an option box in the first place. Sometimes, I even feel that some books use the screen shots to bump up their page count, with little long-term benefit to the reader. There is simply no substitute for learning the technology through trial and error and research. In this book I minimize the learning curve for you if you are new or otherwise thrust into the role of providing network security. To do this, I explain how things work and give you the information you need to compare one product against another. From there it is up to you to research the vendor’s documentation to learn how to configure a given product.
Chapter 2
Managing Network Security
Let us clarify something right from the beginning. Technology alone is not going to secure your network. A trip to your local networking superstore will not necessarily make your network secure, even if you have to back up the minivan to take everything back to the office. The problem is that underlying all security technologies is a single inconsistency that tends to skew all of our hard work and planning—people. That is correct—you, I, and that guy or gal down the hall who is constantly dumping his or her trash in your trash bin. People screw things up. Of course, that is also part of our charm; but people will misconfigure firewalls, tell friends their passwords, make a programming error that causes a server to crash when unexpected input is entered; and odds are that it was another person who typed in the unexpected input in the first place!
The point of this is that we cannot rely on technology to protect our network because the people who create the technology are not perfect. We cannot expect technology to protect us against computer crime. Crime and technology have a long history together. The invention of the wheel did not eliminate crime; it just made it easier to get away from the scene. We should not fool ourselves into thinking that we have finally arrived at the generation that has finally figured out a way to make us immune to crime through the use of technology.
When we start thinking about network security, we need to think about security as a system—not a single technology. By reading this book, you will hopefully be convinced that your information is secured through the use of your information security policies, and not any single piece of technology that you are using. Sadly, I have had more than one conversation with a customer that went like this:
“Well, we have a firewall. Won’t that make my network secure?” the client responds.
“It certainly is a good start, but a firewall does not imply a secure network. We can’t, however, determine what you need for security until we can determine what you need to secure,” I counter, sitting down to a conference table and giving my pen a twist to expose the tip.
A couple of scratches on the notepad later and I am confident that the pen is working. I look up to see the customer still looking at me.
“What do you mean, what we want to secure? We want to secure our network against hackers.”
Most people clearly understand the need to secure their network. Looking at any poll of IT professionals, CIOs, and managers, the need to secure their network against “hackers” generally tops the top-three concerns that these people have about their network. Unfortunately, this high priority generally leads to technology that drives the security.
When technology drives the security, you have a situation in which the IT staff looks around and thinks, “What do I have that can secure my network?” In general, their gaze eventually falls upon a firewall—perhaps even a VPN (virtual private network). While I will never be one to argue that a firewall is not a good idea to include in a security model, this is not the proper approach to creating network security. It creates a security model that is built around what security a particular device can provide, rather than the security the network needs. I counsel my clients that, instead of talking about hardware and software, the first order of business should be to create a security policy. A security policy is a high-level statement of principle and describes the needs of the network. Once we know what we need to do, we can then discuss the security model. The security model is the actual hardware, software, and configuration guidelines that will be used to enforce the policy.
2.1 The Big Picture: Security Policies from A to Z
One of my hobbies is amateur bodybuilding. This hobby also happens to provide a good nontechnical example of the difference between a policy and a model. I am often asked by people in the gym, “How can I make good gains from working out?” The questioner then typically modifies the query by defining what “gains” means to them, either losing fat or gaining muscle mass. Either way, I can respond to them with a policy, “Eat well. Work out consistently.”
My policy on maximizing gains is clearly a high-level statement of principle. It broadly defines how the questioner should obtain his goal of “good gains.” Rarely, however, do people nod knowingly when I tell them this and run off to put it into practice. They also need a model. The model is a series of steps that defines “eat this many calories per day; eat this many meals per day; ensure you get this much protein per day; work out this many times per week; do these exercises; etc.” The person can agree in principle to the policy, but to actually implement the policy, that person needs a model to follow.
A properly constructed security policy has a very specific structure. The security policy is the high-level document that describes the philosophy, business environment, and goals of the organization. To implement these goals, specific steps must be taken. This is the role of security standards and procedures. A high-level policy statement such as “All financial transactions between business partners will remain confidential and arrive with guaranteed integrity” is pretty broad. Our standards and procedures may further state that “Confidentiality between networks utilizing the public Internet will employ either (1) an IPSec VPN with 256-bit AES or equivalent security. Identity will be established through the exchange of RSA signatures via a secure mechanism and validated by a third party certification authority; or (2) an MPLS-based VPN between business partners that share the same service provider. Null-encryption with the MD5 hash algorithm shall be used on such connections to assure the integrity of any transmissions.” This statement offers a couple of specific ways to provide the confidentiality and integrity between your site and remote business partners.
Even then, standards and procedures are not enough to actually implement the solutions. For this, a configuration guide is required. As the name suggests, the configuration guide is a step-by-step guide that shows which options to enable, what values to fill in the provisioning order, etc. This is the step-by-step guide that is used to put the security policy into place. Together, the structure of a security policy looks like the diagram shown in Exhibit 1. The process of creating the security policy can be broken down into nine distinct steps, with additional optional steps as required. These nine steps are listed below:
- Obtain management support
- Identify information assets
- Draft policy statement
- Perform risk analysis
- Select countermeasures
- Create security standards
- Create configuration guides
- Implement
- Review
Each of these steps is discussed in detail as the chapter progresses.
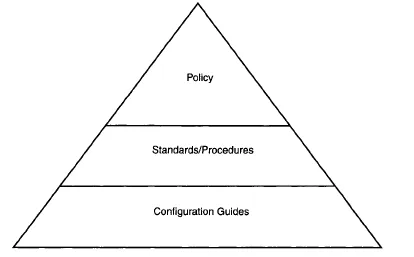
Exhibit 1. The Security Policy Model
2.1.1 Getting Management Buy-In
Sometimes it can be difficult difficult to explain to management why the time and effort must be spent in constructing a security policy. At the same time, without this important step, the remainder of the security policy process is somewhat pointless. By the end of this chapter it should be clear that this is a step integral to the successful implementation of network security. Until that point, when a baseline of security has been established on the network, getting the process rolling can be a Sisyphean task.
There are practical and legal reasons that management must be involved with the top-down construction of the security policy from the beginning. Remember: you cannot simply drop a bunch of technology into a network and expect to achieve security. The best improvement in information security is obtained when the behavior of individuals can be modified as well. To do this, the authority of management is essential.
Creating a security policy from the bottom up, where seve...
Table of contents
- Cover Page
- Title Page
- Copyright Page
- Chapter 1: Introduction
- Chapter 2: Managing Network Security
- Chapter 3: The Network Stack and Security
- Chapter 4: Cryptography and VPN Terminology
- Chapter 5: Application Security Needs
- Chapter 6: Access Control
- Chapter 7: The Public Key Infrastructure
- Chapter 8: Firewalls
- Chapter 9: Intrusion Detection Systems
- Chapter 10: Virtual Private Networks
- Chapter 11: Wireless Network Security
- Chapter 12: Network Penetration Testing
- Chapter 13: Incident Response
- Chapter 14: Disaster Recovery and Continuity Planning
- Chapter 15: Acceptable Use Policies
- Chapter 16: The Final Word
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Network Perimeter Security by Cliff Riggs in PDF and/or ePUB format, as well as other popular books in Informatica & Reti di computer. We have over one million books available in our catalogue for you to explore.