
- 482 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Adaptive Security Management Architecture
About this book
This volume enables security professionals to structure the best security program designed to meet the complex needs of an entire organization, taking into account the organization's business goals as well as the surrounding controls, processes, and units already in existence. The book explains how an organization can develop an adaptive security program closely aligned to business needs, making it an enabling force that helps the organization achieve its goals and objectives. It presents the end product of a successful security management system and examines the finer points of how it can be accomplished.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1
INTRODUCTION
The information security landscape comprises sophisticated threats, comprehensive regulation, diverse communities, and complex infrastructures that make ensuring the balance between usability and security a constant and demanding challenge. This is most evident in the realm of business. Today’s companies are continuously seeking opportunities to build success through entrepreneurial activities, taking on new challenges, driving opportunity, and creating a dynamic environment that demands agility.
Although today’s information security practices are comprehensive, they do not readily lend themselves to effective adaptation to the ever-changing needs of the business. Information security can thrive in a consistent and predictable environment, but this is becoming increasingly rare in a highly competitive, fast-moving global market that is employing compelling and disruptive technical solutions. There is a growing divide between business’s demand for agility, adaptation, effectiveness, and efficiency and the steadfast, rigid, protective nature of security. Yet security has a rich culture and underlying capabilities that have yet to be fully exploited in achieving greater alignment with business demands.
The adaptive security management architecture (ASMA) is an approach founded on several core principles and the value that can be gained from creating an interconnected security model focused on effectiveness, maturity, and collaboration. The goal is to take much of what exists in the industry today and bind it together in a unique and innovative way so as to produce an adaptive security program. Once the core principles and the important nuances of the interconnectedness between the ASMA’s features are realized, the outcome of the security program will be vastly more aligned to the business and as such will be an enabling force in helping the business to achieve its goals and objectives. The ASMA utilizes and reorganizes what you likely already have at your disposal in a manner that promotes meaningful change to enable the business without losing sight of risk and compliance.
In many ways it is less about traditional information security and more about the mechanisms that drive security within a business. The ASMA will change the identity of security in the eyes of a business by focusing on the relationship between security philosophy and business value, which will expose the intent of demands driving how security is applied and realized. Security as we know it today will become simply tools that are governed and applied by a collection of architecture features working together to achieve adaptability.
Importantly, the ASMA harnesses the innate and highly sophisticated security capabilities that are used every day and are well understood, but are not exploited to their true potential. When we thoroughly explore them, we can isolate these deeply rooted processes and reapply them to broader concepts to achieve adaptability. The reapplied intrinsic capabilities in security materialize in the features of the ASMA and how they are interconnected. Empowered with the ASMA, organizations can balance business expectations, such as performance and quality, with security demands, such as risk and compliance, to become a business enabling force.
The ASMA creates an environment that provides visibility into all aspects of security’s role in a business while simultaneously providing the means to influence that environment. All too often organizations measure aspects of security that are not actionable and are not much more than measuring the weather. Although this may help in understanding trends, it does not resonate with the business, which expects to have the ability to meaningfully address dynamics. The ASMA provides the means to influence change and does so by promoting measurements that provide specific translation to elements in the program that need modification or improvement. Based on this foundation, many security organizations can achieve the ability to innovate and confidently project the value of their actions to the business, which is at the heart of business enablement.
Security adaptability is about creating a flexible, proactive environment that has the innate ability to address change in a well-defined and effective manner. To achieve this it is important to understand and quantify the intent of change, standards, regulation, and business demands. Although stability in security is important and is needed to create a manageable environment, without clarity of intent the security program will become rigid and inflexible, furthering the divide with the business.
The ASMA brings together different aspects of security that are generally already defined and accepted within the industry. However, it goes a step further and introduces key aspects in the role of these security domains and the activities they are performing. Most importantly, the ASMA creates an environment where each security feature is interlocked with the others in a meaningful way to ensure adaptation is promoted in a controlled fashion. Much of the interconnects within the ASMA are provided herein, but these are not set in stone and will likely change to meet specific differences in each organization. What is important is the objectives of the interconnects and the role of each of the different features of the ASMA. Within this context, the underlying nature of the ASMA is to get you thinking about security from a new perspective. It is an expression of how elements of security can interact in new and comprehensive ways to drive innovative approaches to become far more agile and achieve greater business enablement.
2
SECURITY AND BUSINESS
The adaptive security management architecture seeks to take advantage of existing security practices and build upon them to promote the value of security to a business and to ensure a meaningful security posture. The ASMA is as much about the business and the security organization operating as a business unit as it is about security, risk, and compliance. There are many facets to the ASMA to achieve this, which are founded on capability maturity, applying security through services, and performance, security, and quality measurements that combine to ensure effectiveness and efficiency. Moreover, the characteristics of the ASMA provide clear visibility into operations and security, which ultimately translate to adaptability and enabling the business.
This chapter introduces the high-level reasoning and purpose for an ASMA and goes on to explain changes in the business environment to demonstrate the alignment of the ASMA to the challenges of today and tomorrow.
2.1 Why a New Architecture?
Today, security is predominantly a collection of practices that are applied based on policy and standards to ensure consistency in meeting overall expectations in the management of risk and compliance. These practices are horizontal in nature given that they are usually performed equally across a business and, similarly, across industries. In fact, most security organizations work very hard to ensure consistency throughout the environment to reduce the potential for gaps in compliance and to maintain reasonable uniformity in the environment to effectively manage risk.
However, the focus on consistency has created a rigid model that does not always effectively address shifts in a business. Moreover, the horizontal and standardized application of security practices does not necessarily resonate with a business for two important reasons. First, the business may be forced to apply security in its entirety, which may include elements in which the business simply does not see value, or of which the business does not understand the applicability to its environment or requirement, or that may simply be security’s standard approach, which is not tuned to the specific goal.
Second, there is limited understanding of and visibility into the operational integrity of the security group and the application of security practices. For example, how efficiently are the security practices being performed, how effective is the result, what features align to the business’s goals, and how do these security practices relate to the overall security program and the mission of the company?
These challenges represent the reasoning for an adaptive architecture that utilizes services as a method for applying security throughout a business. Moreover, and a very important overriding theme throughout this book, today’s security is mature, comprehensive, and quite sophisticated, yet how do we unleash that potential and change the very identity of security in the business? Arguably, the consistency fought for within the security industry has merit. Nevertheless, this has also ushered in difficulties in effectively aligning to the dynamics of the business and achieving adaptability.
While security has significantly evolved over the last several decades it has also unwittingly become a limiting factor from a business’s perspective. Businesses seek to explore opportunity, increase market share, drive revenue, and differentiate themselves. This means taking on risk and new challenges and always changing. Conversely, security seeks to protect the business and put in controls to ensure compliance, manage risk, reduce the potential for debilitating events, and drive consistency. While this is exceedingly important, balance between enabling the business and protecting the business has not been fully achieved. In fact, one could argue that there is a growing chasm (Figure 2.1) between the directive of security and that of the business. This has become exceedingly evident in the face of massive, global economic turmoil.
The two problems introduced above can be summarized as the application of security and the operational integrity of the security group. The holistic employment of horizontal security practices in their entirety may not meet the business need and may include features that are not applicable, or worse, not include attributes that are critical to the business or the overall security posture. Moving forward, security must acknowledge a business’s needs as much as the desire to ensure comprehensive security. Next, of course, is how investments, budgets, and resources in security are employed in providing security and how this is communicated to a business in terms it can readily digest.
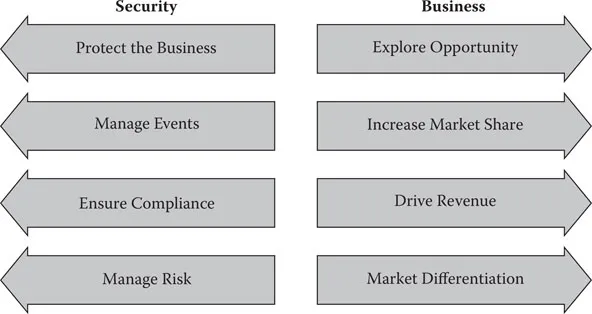
The ASMA closes the gap between business needs and security needs and will redefine security in the eyes of a business to be seen as a valuable, enabling force. It does this by doing two simple and fundamental things. First, it exploits the sophistication that exists within most security organizations today, and second, it does not try to fight the consistency battle causing the divide, but rather embraces it in the form of business intelligence and operations.
As security evolved it produced a great number of standards in the application of security practices. As previously discussed, this presents a degree of rigidity and inflexibility. However, beneath this lie extraordinary capabilities to address virtually any scenario. We’ve all experienced a situation where common approaches fall short and the “go-to-guy” is called in to connect the dots. The resulting activities may be nonstandard and unorthodox, but the ultimate goal is achieved. Essentially, the “go-to-guy” understands all of what is possible and what exists within the realm of security in the organization as ingredients, takes time to understand the need, and composes a solution that utilizes existing nuances to fine-tune security to meet the specific objective. Moreover, this is performed in a manner that not only satisfies the business demand, but also ensures it has value in the larger security posture, such as compliance and risk.
Clearly not all scenarios can be predicted, and therefore they cannot be standardized. As a result, there are many security savvy professionals in the field tuning and adjusting the norm to achieve a goal. This represents monumental value to security and to a business when wielded correctly. Unfortunately, these efforts are rarely indoctrinated because they are seen as one-offs and the value is inexorably tied to the “go-to-guy,” who you hope does not quit.
The ASMA, in large part, exploits this organic process by providing an interface between a business and the application of security. Security can have a wide range of depth and breadth in its application and as a result has the potential to be fine-tuned to a specific need or environment. Given the likelihood for complexity and diversity of challenges and environments, traditional security standards cannot be solely relied upon. Moreover, the reliance on individual or group efforts is not scalable and represents single points of failure to the security program, thus challenging sustainability.
Building different security services and spreading horizontal security practices over several vertical—targeted—services can reduce the spectrum of possibilities in the execution of security, which offers the opportunity to predict different scenarios. These options will manifest themselves in the service and ultimately act as governing agents in the application of security.
Although the organization of security into services introduces greater sophistication into the execution of security, this represents only one aspect of the value the ASMA provides. The ASMA focuses energy into the delivery of services, but it also defines mechanisms to ensure compliance, address risk, and ensure that people and processes are interacting effectively, and it introduces specific points of interaction that ensure consistency in the operational integrity of the security organization.
What should become evident is that the ASMA, in part, formalizes and enhances what is already likely occurring in security organizations around the world. It’s about embracing all the resources at your disposal and acknowledging the value of organizing security in a manner that truly exploits what is possible, fundamentally converting security into a business enabler. It raises the bar on performance, expectations, and capability, moving beyond common practices to release the true potential of security. Today’s challenges, such as addressing multiple regulatory demands and communicating the need for security to executives, will give way to an environment in which these will become by-products. When fully implemented it is likely that security organizations will discover far more intimacy with businesses, have greater clarity on capabilities and expectations, and play a more integral role in the evolution and overall success of businesses.
2.2 The Conflict of Change
Change is the key factor and as such represents the fundamental conflict between security and business (Figure 2.2). It is necessary to acknowledge the opposing forces and find a balance between the heritage of traditional security and the emerging demands of a business.
At the highest level, security is an agent for stability that conflicts with the agent of change within a business. Security seeks to focus on standardization and consistency to ensure a predictable environment, whereas a business is seeking to drive change to increase market share, ensure continued competitive differentiation, or enact progressive products or services.
The key to finding balance is to ensure that change is not simply for the sake of change, but rather for security to have a meaningful role in maintaining posture when change is necessary. Fundamentally, this means having the capacity within security for comprehensive visibility into how the security program is functioning and identifying the options for change as well as the implications of change. Comparatively, today we have change that flows down from the business into security, which is forced to react and ultimately translates to firefighting. Moreover, this has resulted in a security culture of resistance and the formation of policy and standards that create an envelope for the business in how to address change, which has not been enormously successful and will likely not scale with the business over time.
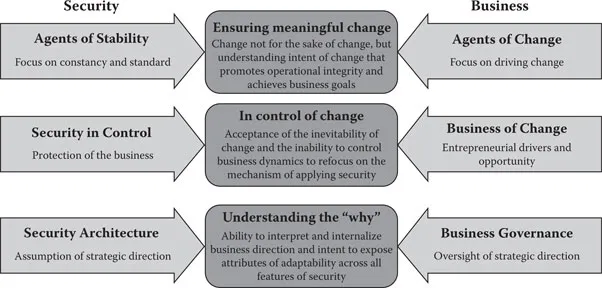
The next level of conflict is the interpretation of control. Today’s security has assumed the role of protector as well as enforcer, leading to, in some cases, a police state. This conflicts with the fact that the business is ultimately in control of change to drive business and meet stated goals. It is inevitable that the business will move forward. Of course there are conditions, specifically compliance, under which the business must concede to the needs of security, but this has resulted in a poor identity for security. The balance is for security to accept change, accept the inability to control a business’s demand for change, and promote a culture of agility through maintaining control of change. It is necessary to embrace change and everything this implies, and to prepare a security capability that is resilient, proactive, and predictive.
Finally, today’s security architecture is the manifestation of standardization and stability, and is reflective of controlling a business. Many security architectures inherently assume that strategic direction within a business conflicts with the formation of such things as business and information technology (IT) governance. IT governance has a connection with business in driving strategy and how this materializes in IT business services. Some security organizations have formed a tight bond and become integrated with IT governance, but for many the conflict remains. The balance is for security to understand the “why” of change. This does not mean learning about the change to dismantle it or fight it, but rather to fully understand the business drivers so that security can plan more efficiently and, more importantly, respo...
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Dedication
- Table of Contents
- LIST OF ILLUSTRATIONS
- LIST OF TABLES
- FOREWORD
- ACKNOWLEDGMENTS
- ABOUT THE AUTHOR
- CHAPTER 1 INTRODUCTION
- CHAPTER 2 SECURITY AND BUSINESS
- CHAPTER 3 ACHIEVING ADAPTABILITY
- CHAPTER 4 DEFINING SECURITY SERVICES
- CHAPTER 5 SERVICES MANAGEMENT
- CHAPTER 6 RISK MANAGEMENT
- CHAPTER 7 COMPLIANCE MANAGEMENT
- CHAPTER 8 GOVERNANCE
- CHAPTER 9 ORGANIZATIONAL MANAGEMENT
- CHAPTER 10 CAPABILITY MATURITY MANAGEMENT
- CHAPTER 11 CONCLUSION
- INDEX
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Adaptive Security Management Architecture by James S. Tiller in PDF and/or ePUB format, as well as other popular books in Business & Business General. We have over one million books available in our catalogue for you to explore.