
eBook - ePub
Implementing Cybersecurity
A Guide to the National Institute of Standards and Technology Risk Management Framework
This is a test
- 313 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Implementing Cybersecurity
A Guide to the National Institute of Standards and Technology Risk Management Framework
Book details
Book preview
Table of contents
Citations
About This Book
The book provides the complete strategic understanding requisite to allow a person to create and use the RMF process recommendations for risk management. This will be the case both for applications of the RMF in corporate training situations, as well as for any individual who wants to obtain specialized knowledge in organizational risk management. It is an all-purpose roadmap of sorts aimed at the practical understanding and implementation of the risk management process as a standard entity. It will enable an "application" of the risk management process as well as the fundamental elements of control formulation within an applied context.
Frequently asked questions
At the moment all of our mobile-responsive ePub books are available to download via the app. Most of our PDFs are also available to download and we're working on making the final remaining ones downloadable now. Learn more here.
Both plans give you full access to the library and all of Perlego’s features. The only differences are the price and subscription period: With the annual plan you’ll save around 30% compared to 12 months on the monthly plan.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes, you can access Implementing Cybersecurity by Anne Kohnke,Ken Sigler,Dan Shoemaker in PDF and/or ePUB format, as well as other popular books in Computer Science & Information Technology. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Introduction to Organizational Security Risk Management
At the conclusion of this chapter, the reader will understand:
■ The role and importance of risk management in the cybersecurity process
■ The issues associated with risk and generic risk management
■ The form and content of the risk management process
■ The general structure and intent of risk-oriented frameworks
■ The general application and development of a risk-based strategy
■ The generic elements of the risk management process
1.1 Introduction to the Book
The goal of this book is to provide a comprehensive understanding of the strategic risk management process as well as the underlying principles and a standard risk management framework. Risk management entails a formal set of steps that are carried out to protect an organization’s assets from harm that may be caused by inadvertent or deliberate acts of destruction. Risk management involves a systematic architecture comprising all the necessary controls to prevent unauthorized use, loss, damage, disclosure, or modification of organizational information. Specifically, this chapter discusses the formal processes for identifying, managing, and mitigating risk as prescribed by the National Institute of Standards and Technology’s (NIST) risk management framework (RMF). In this chapter, we also discuss the general uses for the framework and the contexts in which it applies.
In some respects, this book is as much about standardization as it is about risk management. Hence, Chapters 2 and 3 present an overview of the role of the standardization process in ensuring a consistent response to a given issue of importance. This includes a discussion of why information assets are difficult to protect as well as the part in which commonly acknowledged best practices apply in ensuring an informed response. The discussion will also center on how to use the NIST’s RMF as a standard means of deploying an appropriate set of information technology security controls. We lay out the issues involved in implementing a standard process, including the benefits that derive from it, as well as potential pitfalls. We also try to give you an understanding of the implementation process, which is best demonstrated by applying the RMF to a specific context.
1.2 Risk Is Inevitable
Risk is a fundamental element of human life in the sense that risk is always a factor in any situation where the outcome is not precisely known (Figure 1.1). In addition, the necessary calculations that we make about the probability of some form of harm resulting from an action that we take are generally a given in our decision processes. Whether the risk assessment involves decisions about a major corporate initiative or just making the decision to walk down the street, we are always anticipating, identifying, and evaluating the potential risks involved. In that respect, we can be said to be constantly managing risk in everything we do.
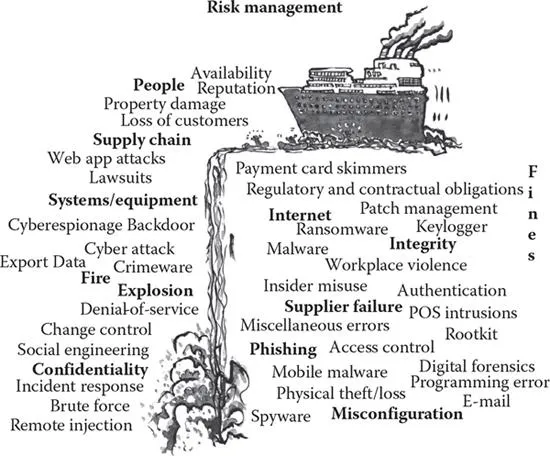
Figure 1.1 Security risk management.
The reason why risk management is a particularly important aspect of the cybersecurity body of knowledge (BOK) is that information and communication technology (ICT) and information assets are more difficult to account for and control than most conventional physical assets, because ICT involves the production and management of virtual, highly dynamic products, which makes it difficult to identify what to secure, let alone how to do it. That puts risk management center stage in the consideration of how to establish and maintain a secure ICT environment.
By definition, ICT assets are something of value to the business. The risk management process specifically ensures the assurance of three generic protection criteria, as shown in Figure 1.2. These three criteria assure against meaningful loss of confidentiality, loss of integrity, and loss of availability (CIA).
From a security standpoint, the most logical generic criterion might be assurance against a loss of confidentiality. Confidentiality is a security principle that encompasses an organization’s requirement to restrict access to any sensitive information or data that it keeps. Obviously, if the organization’s data and information could be made public without risk, there would not be a need for this attribute; however, this is rarely the case.
From an operational point of view, confidentiality is founded on establishing and adequately enforcing access control. Data and information are essential to the business operation. And in many information-intensive organizations, it might be the only real asset that is kept. For instance, most financial data within a company is sensitive and access is almost always rigorously safeguarded. So, one way to view the monetary value of confidentiality is to imagine how much competitors might pay to have access to the data and information of a company or the cost of litigation if a legal requirement was violated. Thus, in that respect, the organization has a legal and ethical requirement to protect its sensitive business information as well as employee and customer privacy.
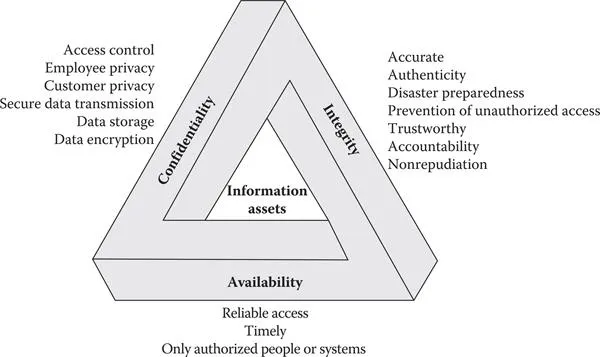
Figure 1.2 The confidentiality, integrity, and availability (CIA) triad.
The second characteristic is integrity. The integrity of data or its attended processes is determined based on how authentic, accurate, and complete the data is. It is easy to appreciate the value of integrity in the context of financial business transactions. For example, if a bank could not depend on its account balances, it could potentially sustain a large loss by disbursing checks not covered by actual funds. In an inventory system, there is the potential to lose expensive materials if the counts were inaccurate due to faulty data. Or publically, the release of unreliable data that is used as background for a damaging story might expose a newspaper to legal action.
The third characteristic, availability, ensures that information is provided to an authorized user when it is required. The best way to understand the value of availability is to ask, “What would happen if the information was not available to support a given action or decision?” For example, what would happen if the business’ payroll data were erased on payday? If the payroll program were suddenly inoperative, no one in the organization would be paid as expected. Imagine the chaos in a company the size of General Motors or IBM if they were unable to pay their employees or suppliers when they needed to. Given the potential harm that each of these principles might represent, all of the meaningful risks in each of these areas must be rationally managed.
Because every organization is unique and implements security differently, the actual process to identify, evaluate, and ensure that the meaningful risks in each of the CIA areas are properly managed generally involves the same eight requirements, which are as follows (Figure 1.3):
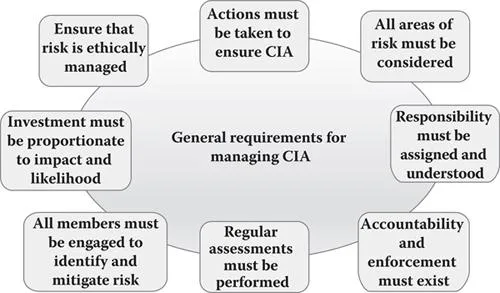
Figure 1.3 General requirements for meaningfully managing CIA.
- Identifiable actions must be taken to ensure correct, confidential, and available information.
- All relevant areas of risk must be considered in any given solution.
- The responsibility for risk management must be explicitly assigned to individuals and understood.
- A system of accountability and enforcement for risk control must exist and be documented.
- Regular and systematic assessments of risk status must be performed.
- All members of the organization must understand the importance of and work to identify and mitigate risk.
- Investment in risk management must be kept proportionate to the impact and likelihood of the risk occurrence.
- The organization must ensure that risk is ethically managed.
In practice, organizations should design, implement, and follow a systematic process to establish a persistent operational risk management process. This design and management process is a strategic activity in that it involves short- and long-range considerations. Thus, planning for strategic risk management is necessary in order to ensure continuous risk assurance. And a formal strategic planning process is necessary to implement an organization-wide risk management process. Risk management itself must incorporate all of the elements of the business within its scope and the process should reach to the boundaries of the organization.
The outcome of the implementation of a risk management process is a concrete organization-wide risk management scheme that is documented. The risk management scheme will balance the aims of a long-term risk control policy with real-world conditions and constraints. The atomic-level components of the risk management process are a set of substantive security controls that ensure the requisite level of assurance against loss. These security controls should be traceable directly to the individual policies that defined their need. This is a closed-loop process in that the ongoing alignment of risk security controls to individual policies fine-tunes the evolution of the substantive risk management process and ensures its effectiveness in the operational setting.
One problem is that the term “risk management” is rather nebulous. So, the overall process itself requires a definition of what risk management means. A concise statement and commitment to the work is needed in order to make the practice standard. Standardization is important because a lack of effective, coordinated implementation and execution of the process has made overall risk management efforts ineffective. Worse yet, employees might feel the effort is the “flavor of the day” and not take it seriously. One does not need to look any further than the increasing number of incidents in cyberspace to confirm that.
The lack of coordinated action has been so pervasive that a logical response is the formulation of a comprehensive and coherent specification of the commonly accepted best practices for risk management. The specification could then be used to guide the creation of an effective risk management scheme for all organizations. In that respect, steps were taken by the federal government to formally research and develop a standard and comprehensive risk management process.
The specification of commonly accepted standard processes is the role of the NIST, the U.S. government’s standards making body. Of specific interest here, the NIST has developed and published a formal reference model for the management of risk simply called the RMF, as shown in Figure 1.4.
This large-scale standard model serves as both the specification of a fundamental process for understanding the risks involved in assuring information and ICT organizations and the foundation for deploying the common control mechanisms required to manage the risks that exist within them. It has the additional advantage of providing the umbrella definition of the processes for achieving Federal Information Security Management Act (FISMA) and NIST certifications.
An important justification for this standard is that the RMF also defines the basis for a comprehensive strategic governance approach to risk. A governance rather than a technical approach is a highly advantageous strategy because, notwithstanding the issue of whether the cybersecurity function itself can ever fully embrace all of the issues associated with assurance, a governance-based solution is more easily understood and acceptable to the managers and nontechnical people who comprise the majority of the organization.
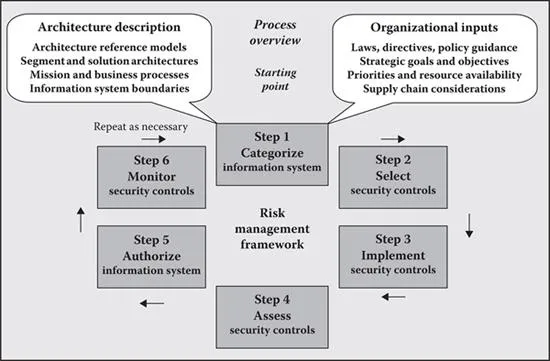
Figure 1.4 The National Institute of Standards and Technology’s risk management process overview.
A governance approach is appropriate for any organizational setting. In essence, a generic governance model constitutes a flexible top-down organizational process for establishing persistent risk management actions and the formal selection and maintenance of appropriate security controls. Moreover, since the RMF is founded on an established policy and procedure approach, it is able to capture and communicate the nature of the specific risks that an organization may encounter. And finally, since the framework itself is built and maintained through a comprehensive identification and assessment process, it can assist in rationally and systematically identifying changes in the threat environment as they occur.
1.3 Strategic Governance and Risk Management
Starting from the assumption that a standardized risk management process should be applied organization-wide (which is what we believe), risk management is a strategic issue, rather than a narrow technical concern. The reason to adopt an organization-wide risk management approach is to avoid the dysfunctional effects of a typical piecemeal solution where every department is managed by its own commonly accepted business practices. These are often based on an individual unit or manager’s ideas about the proper way to accomplish a particular organizational goal. And regardless of whether they are universally standard or documented, these become the corporate way of doing business. One problem is that those approaches are often not coordinated effectively in the operational environment. In some cases, they can actually cause dysfunctional conflicts. And corporate risk management has often evolved this way. Organizations develop specific one-at-a-time responses as risks present themselves, rather than addressing them by employing a single, coordinated management strategy. Moreover, as new risks appear in the corporate threatscape that have not been seen before, they are not incorporated into any specific management techniques that the organization employs to mitigate and contain them.
The alternative approach to piecemeal risk management is a formally defined and instantiated architecture of comprehensive risk management best practices, which are specifically aimed at optimizing risk controls within the company. As with any complex system, formal risk management practice can only be implemented through a rational and explicit planning process. The planning activity fits the strategic purposes and responsibilities of standards-based risk management to the security needs of the organization. From the standpoint of the rest of this text, it is the creation of that strategic risk management capability, which the RMF leverages, that will drive the presentation and discussion of the framework.
Risk management is basically built around information. In effect, risk management gathers and utilizes information from all sources, in order to decrease the possibility of future risks. The information-gathering activity is aided by a set of formal processes and technologies. And, at its core a successful risk management function relies on the ability to assure that the processes, practices, knowledge, and skills of risk management are incorporated as quickly and efficiently...
Table of contents
- Cover
- Half Title
- Series Page
- Title Page
- Copyright Page
- Table of Contents
- Foreword
- Preface
- Authors
- 1 Introduction to Organizational Security Risk Management
- 2 Survey of Existing Risk Management Frameworks
- 3 Step 1—Categorize Information and Information Systems
- 4 Step 2—Select Security Controls
- 5 Step 3—Implement Security Controls
- 6 Step 4—Assess Security Controls
- 7 Step 5—Authorize: Preparing the Information System for Use
- 8 Step 6—Monitor Security State
- 9 Practical Applications of the National Institute of Standards and Technology Risk Management Framework
- Appendix
- Index