Chapter 1
How Bad Is It Out There?
Abstract
This chapter discusses the severity of hacking threats for companies. The author discusses the problem in general, and why so many companies are being breached, how data are lost and stolen, and who the hackers are. This chapter further gives examples of major, high-profile security breaches that have recently been seen in the media and briefly discusses the techniques used by hackers to breach computer systems.
Keywords
Hacking; hackers; network security; security breach; malware; end user
Let’s discuss about how bad it is, and whether or not you should be concerned. First of all, cyber threats, hacking and theft of data is much worse than most understand and would believe. So yes, you should be very concerned.
Here’s a great analogy. As a gun owner, good safety dictates you assume and treat every gun as if it is loaded. The same applies to cyber security. Assume every network or computer device is or has been compromised in one way or another. I go through life assuming that my laptop and other computing devices have been compromised and there’s nothing I can do about it. You have to make that assumption because unless you’re a forensic examiner or malware analyst, can look at your computer logs daily and determine whether you have been infected or compromised, you can never be sure and it’s better to be safe than sorry. If you assume you have been compromised you will be much more cautious with your data. With that in mind, preparation is the key. You must identify and attempt to lower risk, and take action to attempt to prevent a breach. But, as stated, preparation is the key. Prepare for that inevitable breach because it will happen.
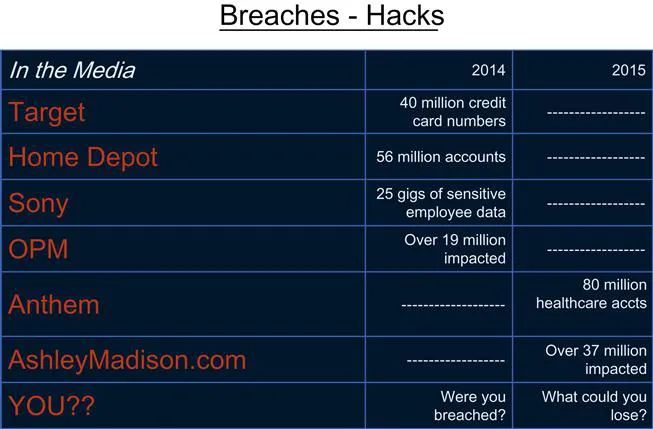
Let’s review some recent major breaches. This is just a small sampling of what has appeared recently in the media. If you look at some of the websites that report data breaches, you’ll see there’re hundreds of businesses that are breached every month and sensitive information lost. Some of the major breaches most of us are familiar with include Target, 40 million credit card numbers; Home Depot, 56 million accounts; Sony, 25 gigs of sensitive employee information; Office of Personnel Management (OPM), this one is personal for me since I was in the military, 19 to 21 million, and the figure is likely much larger now. The latest news is that the OPM breach included the theft of fingerprints. With that number of records stolen, anyone who served in the military has to assume that their personal information was part of that breach. And it continues. Anthem Health, 80 million medical records stolen; Ashley Madison, 37 million, and not just names and social security numbers, but very personal information to include people being outed left and right as cheaters. So, where do you stand? Do you even know whether your business or firm has been breached? You need to assume you have been and plan from there. This attitude puts you in a much better perspective than saying to yourself, “I’m not worried, it won’t happen to me.” You’re kidding yourself if you follow that line of thinking. The breaches are real and impacting all.
Later we will provide some more in depth discussion about the hackers, who they are, how they get in and the technology behind their techniques. Briefly though, the techniques of a hacker are not like those of someone breaking into a bank, your house, or shoplifting. Hackers use automated tools from the security of wherever their computer is, and operate virtually anonymously hopping from network to network to mask who they are and their location.
Imagine if someone was able to implant tools in retail stores or in banks all around the country, and at the press of a button, these automated tools, like little robots, would begin stealing or shoplifting and tossing the merchandise into a device which then, like a pneumatic tube, transports the merchandise to wherever the thief desires. Usually to a storage space of some other unknowing warehouse owner. That is an attempt at a physical world analogy of the techniques utilized by hackers. Automated systems/software is used to compromise computers, home networks, business networks, etc. These compromised machines/networks are then used to target companies and other networks and steal and disrupt things. For instance, a botnet is a series of infected machines that are controlled by one or more hackers to compromise other machines and networks, send out phishing attacks, implement denial of service attacks, etc. Some of the largest botnets in the world consist of over a million infected computers and networks.
Let’s consider the law of averages. How often does a hacker or attacker have to be right? Just once. How often do we, the defenders, defending our networks have to be right? One hundred percent of the time. It’s 1% versus 100%. Those are some serious losing odds. Yet another reason why you should be so concerned. We are fighting a losing battle.
Before getting back to the hackers, let’s look at another issue hindering companies. The IT companies and departments have been saddled with the job of security, and many do not have the budget, time, or even expertise to adequately do the job. Additionally, for most companies management treats cyber security as an IT/technical issue and therefore don’t bother to pay attention and understand what is really going on. Now understand, my goal is not to pick on IT departments and IT people. They do a great job. But what is their focus? For most companies, it is uptime. Back in the day before cyber was a concern, the primary focus of IT was to install computers, setup the network, install software, get everything up and running, and make sure everyone is online and has 24/7 access. Today that is still the focus. Security is a distant second to that goal. Helpdesk support takes up much of the IT department's time. If you’re using an outsourced IT company, security, in most cases, is really an afterthought, sort of an additional duty. The primary goal of many of these companies, based on what their clients requirements are, is to make sure the client is up and running. In order to be cost effective, most attempt to do this using automation to minimize the number of employees needed, as well as to limit the use of resources. The issue really becomes that of IT versus Suits. Suits want uptime, and IT knows it. Yes, management is concerned with and wants to know about threats, but most who do not have an IT background seem to treat the threats as sort of a theoretical or amorphous threat and fall prey to the attitude of, “I don’t really think it will happen to me.” Also, unfortunately, many IT support personnel, for a myriad of reasons, do not want to tell the leadership how bad the state of security is, how vulnerable the company really is, or how many attacks the company has actually suffered. The attitude appears to be, “I don’t want to tell the emperor he has no clothes,” “I don’t want to tell everybody how vulnerable we really are because it makes me look bad, and makes me look like I’m not doing my job.” In addition there are some IT personnel who believe they are the superman of all things technical and possess the attitude, “I can do it all” and, “nobody will ever get into my network.” I’ve worked with a few of them or done assessments on a few of their companies, and typically it takes all of about 5 minutes to get in. Yes, five minutes. It is usually very simple, especially with that attit...