
eBook - ePub
Digital Forensics Processing and Procedures
Meeting the Requirements of ISO 17020, ISO 17025, ISO 27001 and Best Practice Requirements
This is a test
- 880 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Digital Forensics Processing and Procedures
Meeting the Requirements of ISO 17020, ISO 17025, ISO 27001 and Best Practice Requirements
Book details
Book preview
Table of contents
Citations
About This Book
This is the first digital forensics book that covers the complete lifecycle of digital evidence and the chain of custody. This comprehensive handbook includes international procedures, best practices, compliance, and a companion web site with downloadable forms. Written by world-renowned digital forensics experts, this book is a must for any digital forensics lab. It provides anyone who handles digital evidence with a guide to proper procedure throughout the chain of custody--from incident response through analysis in the lab.
- A step-by-step guide to designing, building and using a digital forensics lab
- A comprehensive guide for all roles in a digital forensics laboratory
- Based on international standards and certifications
Frequently asked questions
At the moment all of our mobile-responsive ePub books are available to download via the app. Most of our PDFs are also available to download and we're working on making the final remaining ones downloadable now. Learn more here.
Both plans give you full access to the library and all of Perlego’s features. The only differences are the price and subscription period: With the annual plan you’ll save around 30% compared to 12 months on the monthly plan.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes, you can access Digital Forensics Processing and Procedures by David Lilburn Watson,Andrew Jones in PDF and/or ePUB format, as well as other popular books in Computer Science & Information Technology. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Introduction
Abstract
This chapter explains the purpose of the book and describes the rationale for the structure of the book. It contains a description of what Digital Forensics are and goes on to explain why there is a need for them. It explains who the target audience for this book is and gives a description of the principles of electronic evidence and some of the problems that have been encountered with it. It then gives an explanation of why there is a need for procedures in Digital Forensics. The chapter finishes with an explanation of the nomenclature that is used throughout the book.
Keywords
Digital Forensics; procedures; electronic evidence; nomenclature
Table of Contents
1.1 Introduction
1.1.1 What is Digital Forensics?
1.1.2 The Need for Digital Forensics
1.1.3 The Purpose of This Book
1.1.4 Book Structure
1.1.5 Who Should Read This Book?
1.1.6 The Need for Procedures in Digital Forensics
1.1.7 Problems with Electronic Evidence
1.1.8 The Principles of Electronic Evidence
1.1.9 Nomenclature Used in This Book
Appendix 1 - Some Types of Cases Involving Digital Forensics
Criminal Cases
Civil Cases
Appendix 2 - Growth of Hard Disk Drives for Personal Computers
Appendix 3 - Disk Drive Size Nomenclature
1.1 Introduction
1.1.1 What is Digital Forensics?
Digital forensics is a highly specialized and fast-growing field of forensic science relating to the recovery of evidence from digital storage media. Digital forensics applies traditional forensics processes and procedures to this new evidential source.
It can also be referred to as computer forensics, but technically speaking, the term only relates to recovery of evidence from a computer, and not the whole range of digital storage devices that may store digital data to be used as evidence. Computer forensics is also often referred to as cyber forensics.
In this book, as in the case of Forensic Laboratory, the term digital forensics is used.
Digital forensics can be used in civil and criminal cases or any other area of dispute. Each has its own set of handling requirements relevant to the jurisdiction in which the case is being investigated.
Typically, digital forensics involves the recovery of data from digital storage media that may have been lost, hidden, or otherwise concealed or after an incident that has affected the operation of an information processing system. This could be an accidental or deliberate act, carried out by an employee or outsider, or after a malware attack of any type.
No matter what the specific details of the case, the overview of processing a digital forensic case by the Forensic Laboratory follows the same series of processes, interpreted for the jurisdiction according to case requirements. The processes are as follows:
• preserving the evidence;
• identifying the evidence;
• extracting the evidence;
• documenting the evidence recovered and how it was recovered;
• interpreting the evidence;
• presenting the evidence (either to the client or a court).
Inspection of numerous sources gives differing definitions of “Digital (or Computer) Forensics,” depending on the organization and its jurisdiction. They all contain some or all of the elements mentioned above (explicitly defined or implied). The Forensic Laboratory uses the following definition:
The use of scientifically derived, proved, and repeatable methods for:
• preserving the evidence;
• identifying the evidence;
• extracting the evidence;
• documenting the evidence recovered and how it was recovered;
• interpreting the evidence;
• presenting the evidence.
to reconstruct relevant events relating to a given case.
The same processes and techniques are used for any digital media, whether it is a hard disk drive, a SIM card from a mobile phone, digital music players, digital image recording devices, or any other digital media.
Details of handling different types of cases are given in Chapter 9. A list of typical types of cases where the Forensic Laboratory has been involved is given in Appendix 1.
1.1.2 The Need for Digital Forensics
The world population was estimated as on June 30, 2012 to be 7,017,846,922 and the number of Internet users at the same time to be 2,405,518,378, some 34.3% of the population. This is an increase of 566.4% since December 31, 2000.a
As the world increasingly embraces information processing systems and the Internet, there are more data being held on digital media. At the same time, an individual country’s Gross Domestic Product (GDPs) is being boosted by an increasing Internet-based component. The current percentage of the Internet economy in the GDP was calculated for the G20 by Bostonb and also produced an estimate for 2016 was also produced. This is reproduced below.
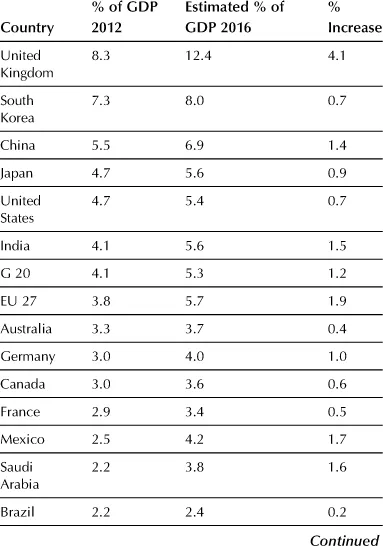
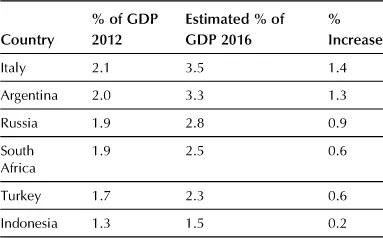
At the same time as the Internet economy has been growing, the size of local digital storage for personal computers has grown as can be seen in Appendix 2. IBM likes to think that they produced the first personal computer (the “PC” or Model 5150) on August 12, 1981; there were a number of personal computers in operation for years prior to this, including Tandy TRS, Apple, Nascom, Commodore PET, Texas Instruments, Atari, variety of CP/M machines, as well as those running proprietary operating systems. A random view of digital storage growth is given in Appendix 2.
While this table shows disks available for personal computer users, those available to corporate users or those with mainframes can have considerably larger capacities. Details of disk size nomenclature are given in Appendix 3.
The amount of growth of digital information worldwide is reported in real time on http://uk.emc.com/leadership/programs/digital-universe.htm.
At the same time, information processing systems of all types are being used to perpetrate or assist in criminal acts or civil disputes as well as just holding evidence relating to the matter. This rapidly changing technology has spawned a completely new range of crimes such as hacking (unauthorized access to a computer system or unauthorized modification to or disclosure of information contained in it) or distributed denial of service attacks. It can be argued that there are no new crimes just variations of old ones, but that legislation needs to be amended to handle new types of execution of offenses.c Whatever the outcome of this argument, more and more information processing devices are used in the commission of criminal acts or are assisting in their execution. There are no hard and fast statistics for the total number of crimes committed where an information processing device is involved, but there are many “guesstimates.” All show increasing use. At the same time, corporate use of information processing devices and digital storage is increasing rapidly.
Given the rapid expansion of both information processing systems and stored data on digital media, it is not difficult to see that Digital Forensics, with its ability to search through vast quantities of data in a thorough, efficient, and repeatable manner, in any language, is essential. This allows material to be recovered from digital media and presented as evidence that may not otherwise be recoverable and presentable in a court.
At this stage, the needs of the corporate world and that of law enforcement (LE) differ on a number of levels:
• LE works under more restrictive regulations that their counterparts in the corporate world.
• The burden of proof is typically more stringent in criminal cases than in civil cases.
• Each is governed by the “good practices” defined by their various governing bodies, and these often differ (e.g., LE relates to the criminal process in the jurisdiction and corporates are more focused on implementation of information security and security incident management).
Corporates are often loathe to involve LE in any incident for a variety of reasons, but legislation now exists in some jurisdictions to report any security incident that discloses personal information or that makes nominated individuals personally liable for breaches or other information security failures. In cases such as this, Digital Forensics may be called on not only to determine how the breach occurred but also to determine the effectiveness of the risk treatment (typically controls) in place to minimize the risk of unauthorized ac...
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- About the Authors
- Technical Editor Bio
- Acknowledgments
- Preface
- Chapter 1. Introduction
- Chapter 2. Forensic Laboratory Accommodation
- Chapter 3. Setting up the Forensic Laboratory
- Chapter 4. The Forensic Laboratory Integrated Management System
- Chapter 5. Risk Management
- Chapter 6. Quality in the Forensic Laboratory
- Chapter 7. IT Infrastructure
- Chapter 8. Incident Response
- Chapter 9. Case Processing
- Chapter 10. Case Management
- Chapter 11. Evidence Presentation
- Chapter 12. Secure Working Practices
- Chapter 13. Ensuring Continuity of Operations
- Chapter 14. Managing Business Relationships
- Chapter 15. Effective Records Management
- Chapter 16. Performance Assessment
- Chapter 17. Health and Safety Procedures
- Chapter 18. Human Resources
- Chapter 19. Accreditation and Certification for a Forensic Laboratory
- Chapter 20. Emerging Issues
- Appendix. Acronyms
- Bibliography
- Index
- Glossary