
- 280 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Netcat Power Tools
About this book
Originally released in 1996, Netcat is a netowrking program designed to read and write data across both Transmission Control Protocol TCP and User Datagram Protocol (UDP) connections using the TCP/Internet Protocol (IP) protocol suite. Netcat is often referred to as a "Swiss Army knife" utility, and for good reason. Just like the multi-function usefullness of the venerable Swiss Army pocket knife, Netcat's functionality is helpful as both a standalone program and a backe-end tool in a wide range of applications. Some of the many uses of Netcat include port scanning, transferring files, grabbing banners, port listening and redirection, and more nefariously, a backdoor. This is the only book dedicated to comprehensive coverage of the tool's many features, and by the end of this book, you'll discover how Netcat can be one of the most valuable tools in your arsenal.* Get Up and Running with Netcat Simple yet powerful...Don't let the trouble-free installation and the easy command line belie the fact that Netcat is indeed a potent and powerful program.* Go PenTesting with Netcat Master Netcat's port scanning and service identification capabilities as well as obtaining Web server application information. Test and verify outbound firewall rules and avoid detection by using antivirus software and the Window Firewall. Also, create a backdoor using Netcat.* Conduct Enumeration and Scanning with Netcat, Nmap, and More! Netcat's not the only game in town...Learn the process of network of enumeration and scanning, and see how Netcat along with other tools such as Nmap and Scanrand can be used to thoroughly identify all of the assets on your network.* Banner Grabbing with Netcat Banner grabbing is a simple yet highly effective method of gathering information about a remote target, and can be performed with relative ease with the Netcat utility.* Explore the Dark Side of Netcat See the various ways Netcat has been used to provide malicious, unauthorized access to their targets. By walking through these methods used to set up backdoor access and circumvent protection mechanisms through the use of Netcat, we can understand how malicious hackers obtain and maintain illegal access. Embrace the dark side of Netcat, so that you may do good deeds later.* Transfer Files Using Netcat The flexability and simple operation allows Netcat to fill a niche when it comes to moving a file or files in a quick and easy fashion. Encryption is provided via several different avenues including integrated support on some of the more modern Netcat variants, tunneling via third-party tools, or operating system integrated IPsec policies.* Troubleshoot Your Network with Netcat Examine remote systems using Netat's scanning ability. Test open ports to see if they really are active and see what protocls are on those ports. Communicate with different applications to determine what problems might exist, and gain insight into how to solve these problems.* Sniff Traffic within a System Use Netcat as a sniffer within a system to collect incoming and outgoing data. Set up Netcat to listen at ports higher than 1023 (the well-known ports), so you can use Netcat even as a normal user.
- Comprehensive introduction to the #4 most popular open source security toolavailable
- Tips and tricks on the legitimate uses of Netcat
- Detailed information on its nefarious purposes
- Demystifies security issues surrounding Netcat
- Case studies featuring dozens of ways to use Netcat in daily tasks
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1. Introduction to Netcat
- Solutions in this chapter:
- Introduction
- Installation
- Options
- Basic Operations
- Summary
- Solutions Fast Track
- Frequently Asked Questions
Introduction
Originally released in 1996, Netcat is a networking program designed to read and write data across both Transmission Control Protocol TCP and User Datagram Protocol (UDP) connections using the TCP/Internet Protocol (IP) protocol suite. Netcat is often referred to as a ”Swiss Army knife” utility, and for good reason. Just like the multi-function usefulness of the venerable Swiss Army pocket knife, Netcat's functionality is helpful as both a standalone program and a back-end tool in a wide range of applications. Some of the many uses of Netcat include port scanning, transferring files, grabbing banners, port listening and redirection, and more nefariously, a backdoor.
There is some debate on the origin of the name Netcat, but one of the more common (and believable) explanations is that Netcat is simply a network version of the vulnerable cat program. Just as cat reads and writes information to files, Netcat reads and writes information across network connections. Furthermore, Netcat is specifically designed to behave as cat does.
Originally coded for UNIX, and despite not originally being maintained on a regular basis, Netcat has been rewritten into a number of versions and implementations. It has been ported to a number of operating systems, but is most often seen on various Linux distributions as well as Microsoft Windows.
Note
For the sake of this chapter, we will work with Netcat in two different operating systems: Windows XP and UNIX/Linux. Windows is in a category by itself. The UNIX and Linux variants are essentially the same thing. Furthermore, the differences within the various Linux distributions are minimal. Also be aware that there are at least two slightly different implementations: the original UNIX release of Netcat as well as a more recent implementation called GNU Netcat.
In the 2006 survey of users of the nmap-hackers mailing list, Netcat was the 4th rated tool overall. In fact, in three consecutive surveys (2000, 2003, and 2006) Netcat was rated no. 2, no. 4, and no. 4 despite the considerable proliferation of more advanced and more powerful tools. In the day and age when users seek the latest and greatest of the edge tools, Netcat's long reign continues.
The goal of this chapter is to provide you with a basic understanding of Netcat. To that end, we'll start with installation and configuration (Windows and UNIX/Linux), and follow up with an explanation of the various options and an understanding of Netcat's basic operations. As we explore some of Netcat's operations, we'll introduce various chapters in the book that cover those operations in greater detail. To that end, consider this introductory chapter as the starting point for your journey.
Installation
Netcat being a rather simple and small program, it is no wonder that installation is straightforward, regardless of the operating system you choose. The Windows port of Netcat comes already compiled in binary form, so there is no true installation required. As previously noted, there are two common UNIX/Linux implementations: the original UNIX version as well as GNU Netcat. Virtually all flavors of UNIX/Linux will come with one of these implementations of Netcat already compiled; however, it is useful to know how to install it if necessary. Furthermore, depending upon your particular implementation, you may need to re-compile Netcat to obtain full functionality.
Windows Installation
Windows installation couldn't be any easier. Simply download the zip file from www.vulnwatch.org/netcat/nc111nt.zip. Unzip to the location of your choice, and you're finished (see Figure 1.1). There are a couple of important files to check out: hobbit.txt is the original documentation, readme.txt is an explanation of a security fix from version 1.10 to 1.11, and license.txt is the standard GNU general public license.
Note
Remember that Netcat is a command-line tool. Double-clicking on the nc.exe icon from Windows Explorer will simply run Netcat without any switches or arguments and will present you with a cmd line: prompt. You can run Netcat this way, but once the instance is complete the window will close immediately. This is not very helpful, especially if you want feedback. It is much easier to use from the command line directly. Start | Run | cmd.exe. nc –h will show you the help screen for further guidance.
Are You Owned?
My Anti-virus said Netcat was a Trojan!
Netcat's potent communications ability is not limited to network administrators. Penetration testers use Netcat for testing the security of target systems (for example, Netcat is included in the Metasploit Framework). Malicious users use Netcat (or one of the many variations of it) as a means of gaining remote access to a system. In this sense, it is understandable why many anti-virus programs have labeled Netcat as a “trojan” or a “hacktool.”Some anti-virus programs may try to prevent you from installing Netcat, or even try to prevent you from downloading Netcat or another application that includes Netcat. As with virtually any tool, there is no internal moral compass that limits its use for only legitimate purposes. Your decision in this case is simply to determine if Netcat was purposely downloaded and installed by you (and thus not a threat), or surreptitiously installed by a malicious user for nefarious purposes.You may consider configuring your anti-virus program to exclude a particular directory where you install Netcat when it scans or auto-protects your file system. Of course, you need to be aware of the dangers associated with this.
Figure 1.1. Netcat Installation Under Windows
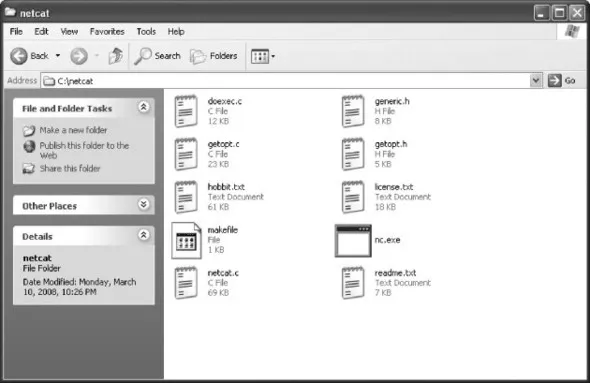
Linux Installation
Many mainstream Linux distributions come with Netcat already compiled and installed. Others have at least one or more versions of Netcat available as a pre-compiled package. To determine the version of Netcat, simply type nc –h or netcat –h. The original UNIX version will return a version line of [v1.10], while the GNU version will return GNU Netcat 0.7.1, a rewrite of the famous networking tool. Even if Netcat is already installed on your system, you may not want to skip this section. Many pre-installed, pre-compiled, or packaged versions of Netcat that come with a Linux distribution are not compiled with what is called the GAPING_SECURITY_HOLE option (this allows Netcat to execute programs with the –e option). These are typically “safe” compilations of the original Netcat source code. The GNU version of Netcat automatically compiles with the –e option enabled, so by installing this version no additional configuration is necessary. Despite this, all other functionality of...
Table of contents
- Copyright
- Brief Table of Contents
- Table of Contents
- List of Figures
- List of Tables
- Technical Editor
- Contributing Authors
- Chapter 1. Introduction to Netcat
- Chapter 2. Netcat Penetration Testing Features
- Chapter 3. Enumeration and Scanning with Netcat and Nmap
- Chapter 4. Banner Grabbing with Netcat
- Chapter 5. The Dark Side of Netcat
- Chapter 6. Transferring Files Using Netcat
- Chapter 7. Troubleshooting with Netcat
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Netcat Power Tools by Jan Kanclirz in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.