
- 560 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Google Hacking for Penetration Testers
About this book
This book helps people find sensitive information on the Web.Google is one of the 5 most popular sites on the internet with more than 380 million unique users per month (Nielsen/NetRatings 8/05). But, Google's search capabilities are so powerful, they sometimes discover content that no one ever intended to be publicly available on the Web including: social security numbers, credit card numbers, trade secrets, and federally classified documents. Google Hacking for Penetration Testers Volume 2 shows the art of manipulating Google used by security professionals and system administrators to find this sensitive information and "self-police their own organizations.Readers will learn how Google Maps and Google Earth provide pinpoint military accuracy, see how bad guys can manipulate Google to create super worms, and see how they can "mash up" Google with MySpace, LinkedIn, and more for passive reconaissance.• Learn Google Searching BasicsExplore Google's Web-based Interface, build Google queries, and work with Google URLs.• Use Advanced Operators to Perform Advanced QueriesCombine advanced operators and learn about colliding operators and bad search-fu.• Learn the Ways of the Google HackerSee how to use caches for anonymity and review directory listings and traversal techniques.• Review Document Grinding and Database DiggingSee the ways to use Google to locate documents and then search within the documents to locate information. • Understand Google's Part in an Information Collection FrameworkLearn the principles of automating searches and the applications of data mining.• Locate Exploits and Finding TargetsLocate exploit code and then vulnerable targets.• See Ten Simple Security SearchesLearn a few searches that give good results just about every time and are good for a security assessment.• Track Down Web ServersLocate and profile web servers, login portals, network hardware and utilities.• See How Bad Guys Troll for DataFind ways to search for usernames, passwords, credit card numbers, social security numbers, and other juicy information.• Hack Google ServicesLearn more about the AJAX Search API, Calendar, Blogger, Blog Search, and more.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
- Exploring Google’s Web-based Interface

- Building Google Queries

- Working With Google URLs




Introduction
Exploring Google’s Web-based Interface
Google’s Web Search Page
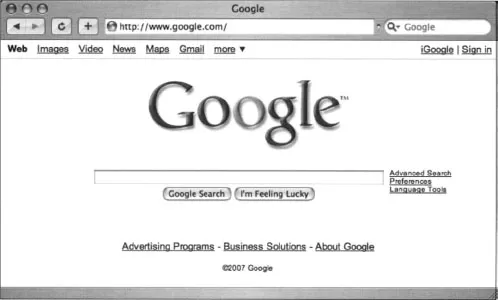
| Interface Section | Description |
|---|---|
| The Google toolbar | The browser I am using has a Google “toolbar” installed and presented next to the address bar. We will take a look at various Google toolbars in the next section. |
| Web, Images, Video, News, Maps, Gmail and more tabs | These tabs allow you to search Web pages, photographs, message group postings, Google maps, and Google Mail, respectively. If you are a first-time Google user, understand that these tabs are not always a replacement for the Submit Search button. These tabs simpl... |
Table of contents
- Cover
- Title Page
- Copyright
- Acknowledgments
- Lead Author
- Contributing Authors
- Table of Contents
- Chapter 1: Google Searching Basics
- Chapter 2: Advanced Operators
- Chapter 3: Google Hacking Basics
- Chapter 4: Document Grinding and Database Digging
- Chapter 5: Google's Part in an Information Collection Framework
- Chapter 6: Locating Exploits and Finding Targets
- Chapter 7: Ten Simple Security Searches That Work
- Chapter 8: Tracking Down Web Servers, Login Portals, and Network Hardware
- Chapter 9: Usernames, Passwords, and Secret Stuff, Oh My!
- Chapter 10: Hacking Google Services
- Chapter 11: Google Hacking Showcase
- Chapter 12: Protecting Yourself from Google Hackers
- Index
- Instructions for online access
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app