
- 496 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Network Analysis, Architecture, and Design
About this book
Traditionally, networking has had little or no basis in analysis or architectural development, with designers relying on technologies they are most familiar with or being influenced by vendors or consultants. However, the landscape of networking has changed so that network services have now become one of the most important factors to the success of many third generation networks. It has become an important feature of the designer's job to define the problems that exist in his network, choose and analyze several optimization parameters during the analysis process, and then prioritize and evaluate these parameters in the architecture and design of the system.
Network Analysis, Architecture, and Design, Third Edition, uses a systems methodology approach to teaching these concepts, which views the network (and the environment it impacts) as part of the larger system, looking at interactions and dependencies between the network and its users, applications, and devices. This approach matches the new business climate where customers drive the development of new services and the book discusses how networks can be architected and designed to provide many different types of services to customers. With a number of examples, analogies, instructor tips, and exercises, this book works through the processes of analysis, architecture, and design step by step, giving designers a solid resource for making good design decisions.
With examples, guidelines, and general principles McCabe illuminates how a network begins as a concept, is built with addressing protocol, routing, and management, and harmonizes with the interconnected technology around it. Other topics covered in the book are learning to recognize problems in initial design, analyzing optimization parameters, and then prioritizing these parameters and incorporating them into the architecture and design of the system. This is an essential book for any professional that will be designing or working with a network on a routine basis.
- Substantially updated design content includes ad hoc networks, GMPLS, IPv6, and mobile networking
- Written by an expert in the field that has designed several large-scale networks for government agencies, universities, and corporations
- Incorporates real-life ideas and experiences of many expert designers along with case studies and end-of-chapter exercises
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1
Introduction
I begin this book with a description of the analysis, architecture, and design processes. Many of the concepts and terms used throughout this book are introduced and defined in this chapter. Some of these concepts may be new to you, while others are presented in a different light. Glossaries of terms and acronyms are presented at the end of this book for easy reference.
1.1 Objectives
In this chapter I will introduce the fundamental concepts of this book: that the network is part of a system that provides services to its end users; that there are processes for developing an analysis, an architecture, and a design for a network; and that there are ways to characterize a network.
1.2 Preparation
In order to understand and apply the concepts in this chapter, you should be familiar with basic networking concepts. This includes the functions and features of the TCP/IP protocol suite, technologies such as the variants of Ethernet, synchronous optical network (SONET), and wave division multiplexing (WDM), and the basics of network routing, security, performance, and management.
1.3 Background
Network analysis, architecture, and design have traditionally been considered art, combining an individual’s particular rules on evaluating and choosing network technologies; knowledge about how technologies, services, and protocols can be meaningfully combined; experience in what works and what doesn’t; along with (often arbitrary) selections of network architectures. However, as with other types of art, success of a particular network design often depends primarily on who is doing the work, with results that are rarely reproducible. This may have been acceptable in the early days of networking, when networks were more of a hobby than a critical resource and did not directly support revenue generation. Today, however, networks are embedded within our work, home, and outside environments. They are considered “mission-critical”1 to corporate success and provide near real-time access to information throughout the world. As such, the design of a network must be logical, reproducible, and defensible. This premise is the foundation for this book.
Traditionally, network analysis, architecture, and design have been based on developing and applying a set of rules for the network. In developing a set of rules, an individual may draw from personal experience as well as from general rules such as the 80/20 rule (where 80% of a network’s traffic is local and 20% is remote) or the adage “bridge when you can, route when you must” (bridging being simpler, easier, and cheaper at the time). As we see later in this book, although both of these rules are ancient from the perspective of networking history, they still apply today, albeit in modified form. Such rules were useful when there weren’t many choices in network technologies and services, and when the differences between choices were clearly understood. But times have changed, and our notion of designing networks must adapt to the variety of options now available to us, the variety of services that networks can offer to end users, and the subtle nuances brought about by combining network technologies, techniques, and services.
Network analysis, architecture, and design have traditionally focused on capacity planning, which is over-engineering a network to provide an amount of capacity (also known as bandwidth) estimated to accommodate most short- and long-term traffic fluctuations over the life cycle of the design. The result is a bandwidth “buffer” that can handle these fluctuations. As network traffic grows over time, this bandwidth buffer is reduced, and users experience problems related to traffic congestion. This is an inefficient use of network resources, wasting money up front in resources that are not used while failing to provide the flexibility needed to adapt to users’ changing traffic requirements. Network bandwidth is only one component of network resources that we must consider. We also need to consider how delay through the network, as well as network reliability, maintainability, and availability (RMA), can be optimized. In today’s evolving networks, delay and reliability can be more important than capacity.
In this book we explore how the analysis, architecture, and design processes have changed and how they continue to change. We discuss how these processes work together in engineering a new or existing network. We approach networks from a different perspective—as a system providing services to its users—and we discuss how networks can be designed to provide many different types of services to users. In taking this approach we emphasize network analysis, which helps us understand what is required of a network in supporting its customers and their applications and devices. As we will see, these processes require an investment in time and effort, but the return on investment is significant. These are powerful tools that can help you build better networks, improving the ability of your organization to get its work done.
This book begins by applying a systems methodology to networking. This methodology is relatively new, and you will learn a number of useful definitions in regard to network analysis, architecture, and design. The rest of this book is logically divided into three sections. The first section covers the analysis process: specifically, how to develop requirements, understand traffic flows, and conduct a risk analysis. The analysis process prepares you for dealing with network architecture, discussed in the second section. Here I describe how to make technology and topology choices for your network, how to understand the relationships among the various functions within your network, and how to use this information to develop an architecture. In the final section the network architecture is used as input for the design process, where location information, equipment, and vendor selections are used to detail the design. Information flows between analysis, architecture, and design processes are presented in Figure 1.1.
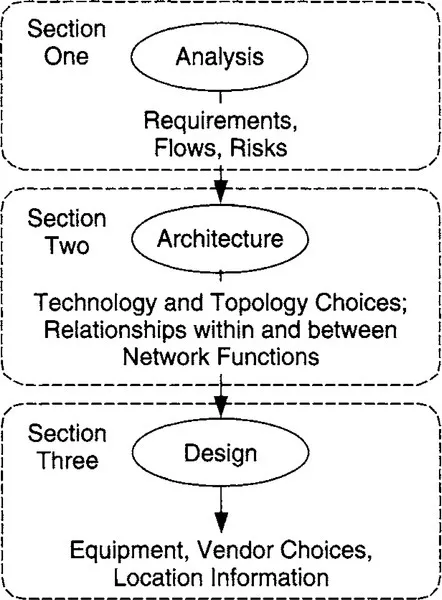
Figure 1.1 Information Flows Between Network Analysis, Architecture, and Design
Network analysis, architecture, and design will help you identify and apply network services and performance levels needed to satisfy your users. Through these processes you will be able to understand the problems you are trying to address with the new network; determine the service and performance objectives needed to tackle these problems; and architect and design the network to provide the desired services and performance levels.
1.4 Overview of Analysis, Architecture, and Design Processes
Network analysis, architecture, and design are processes used to produce designs that are logical, reproducible, and defensible. These processes are interconnected, in that the output of one process is used directly as input to the next, thus creating flows of information from analysis to architecture, and from architecture to design.
Network analysis entails learning what users, their applications, and devices need from the network (Figure 1.2). It is also about understanding network behavior under various situations. Network analysis also defines, determines, and describes relationships among users, applications, devices, and networks. In the process, network analysis provides the foundation for all the architecture and design decisions to follow. The purpose of network analysis is twofold: first, to listen to users and understand their needs; and second, to understand the system.
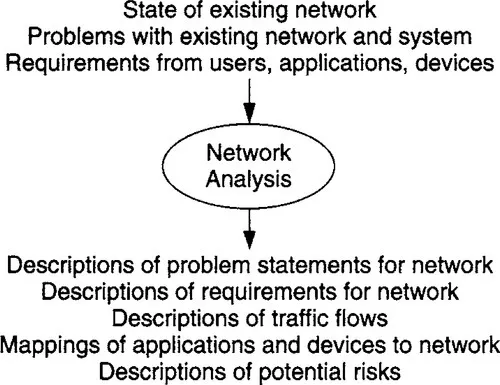
Figure 1.2 Inputs To and Outputs From the Network Analysis Process
In analyzing a network we examine the state of the existing network, including whatever problems it may be having. We develop sets of problem statements and objectives that describe what our target network will be addressing. And we develop requirements and traffic flows, as well as mappings of users, applications, and devices, in support of our problem statements and objectives. As such, network analysis helps us understand what problems we are trying to solve, and in the process we compile information that will be used in developing the architecture and design.
Network architecture uses the information from the analysis process to develop a conceptual, high-level, end-to-end structure for the network. In developing the network architecture we make technology and topology choices for the network. We also determine the relationships among the functions of the network (addressing/routing, network management, performance, and security), and how to optimize the architecture across these relationships. There usually is not a single “right” architecture or design for a network; instead there are several that will work, some better than others. The architecture and design processes focus on finding those best candidates for architecture and design (optimized across several parameters) for your conditions.
The network architecture process determines sets of technology and topology choices; the classes of equipment needed; and the relationships among ...
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright page
- Dedication
- Foreword
- Preface
- 1: Introduction
- 2: Requirements Analysis: Concepts
- 3: Requirements Analysis: Process
- 4: Flow Analysis
- 5: Network Architecture
- 6: Addressing and Routing Architecture
- 7: Network Management Architecture
- 8: Performance Architecture
- 9: Security and Privacy Architecture
- 10: Network Design
- Glossary of Terms
- Glossary of Acronyms
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Network Analysis, Architecture, and Design by James D. McCabe in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.