
- 525 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
About this book
MPLS-enabled networks are enjoying tremendous growth, but practical information on managing MPLS-enabled networks has remained hard to find. Until now. MPLS Network Management: MIBs, Tools, and Techniques is the first and only book that will help you master MPLS management technologies and techniques, as they apply to classic MPLS networks, traffic-engineered networks, and VPNs. Written by the co-author of most current MPLS management standards, it provides detailed, authoritative coverage of official MIBs, examining key topics ranging from syntax to access levels to object interaction. It also offers extensive consideration of third-party management interfaces, including tools for metering traffic and predicting traffic growth and behavior. If you're a network operator, network device engineer, or MPLS application developer, you need this book to get all you can out of all of MPLS's many capabilities.* The only book devoted entirely to the tools and techniques for controlling, monitoring, debugging, and optimizing MPLS-enabled networks. * Authoritative information from the co-author of most IETF MIBs relating to MPLS and GMPLS, PWE3, and PPVPN. * Covers both standards-based and proprietary management technologies. * Includes interviews with seminal figures in the development of MPLS. * Via a companion web site, provides information on late-breaking developments in MPLS management and links to additional resources. * To be followed by a second volume presenting best-practice case studies dealing with how real companies approach the management of their MPLS networks.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1
Introduction
“It is a mistake to look too far ahead. Only one link in the chain of destiny can be handled at a time.”
–Winston Churchill
Introduction
In this chapter, we look at the origins of Multi-Protocol Label Switching (MPLS) and introduce some of its basic concepts, including the separation of the control and forwarding planes of MPLS, the Forward Equivalence Class, and the MPLS label. After this introduction, we then introduce and discuss some of the new applications of MPLS networks such as traffic engineering and virtual private networks.
After an introduction to MPLS, we explain the basic premise behind why MPLS-enabled networks need to be managed to provide scalable, usable, and most importantly profitable MPLS networks. Given this motivation, we introduce how MPLS networks can be managed effectively using both standards-based and nonstandard tools, many of which are described in this book. This discussion serves as an introduction to the remainder of the book.
It is not our goal for this discussion to be an in-depth introduction to MPLS. We assume you have a good level of understanding of MPLS already and that the introduction given in this chapter can be used as a refresher. Advanced readers may skim the beginning of the chapter, but we recommend at least glancing at the latter half of the chapter. If you are in need of a more in-depth introduction to MPLS and SNMP, consult the references given in the Further Reading section at the end of the chapter as well as those related to MPLS and SNMP in the Bibliography at the end of the book.
1.1 A Brief Introduction to MPLS
In the past, routing devices were designed with the control and forwarding components commingled, which led to many shortcomings including low performance and scalability issues. In particular, routing lookups, especially those involving so-called longest-prefix match lookups, were quite complex and expensive in nature—in fact, quite a deal more complex than any layer-2 switching or bridging operation. Further complicating this process was the fact that many routers were required to forward packets from many different routing protocols. By accepting packets from different protocols, the positions of fields in packet headers could potentially be different for nearly every packet received, potentially further degrading forwarding performance. In contrast, nonrouting devices such as layer-2 bridges and switches were able to forward traffic at relatively high speeds because they based their forwarding decisions not on variable-length packet headers and network addresses of varying lengths, but on a short, fixed-length field. For example, all ATM cells have a fixed length and well-defined format. Devices switching ATM cells only need to examine a short identifier and can immediately forward the cell based on this simple piece of information. There is no question as to the position of the forwarding information in a cell. However, layer-2 devices suffered from the lack of routing information, which ultimately limited their scope and effectiveness. Let us now examine the control and forwarding planes in more detail, and then investigate how they can form the basis of an efficient and scalable MPLS label switching router (LSR).
The control component of a router is responsible for the exchange of routing information between other network nodes. It is this information that is used to form the router’s routing database. This database paints a picture of the network from which a router can discern what it considers to be the most optimal path to any given destination in the network. Once stabilized, this database of best paths can be used to program the router’s forwarding table. In contrast, the forwarding function of a router focuses exclusively on the actual decision of moving packets between ports on a network node. Each packet contains a header with source, destination, and other information. When a node receives a packet on a port, it needs to decide which port (or ports) it needs to forward that packet to. The forwarding process is quite mechanical by nature. When a node receives a packet, the forwarding component in that node will first examine the destination address contained in the incoming packet as well as perhaps other fields in the header. This information is then compared with entries in its forwarding database. It is this simple process that allows the forwarding component to make quick and simple decisions as to where the packet needs to be forwarded.
In some devices, the forwarding component is tightly coupled with the routing component. This approach sometimes results in limited portability of that technology to other types of forwarding planes. It also sometimes results in difficulties in extending the protocol with additional functions. MPLS is built on both the premise of a clean separation of the control and forwarding functions to take advantage of their individual advantages, as well as using them together in concert to provide additional advantages not possible with other technologies. The control and routing functions of MPLS are based on the Internet Protocol suite of protocols, which includes IP, RSVP, BGP, OSPF, and so on. The basic device in an MPLS-enabled network is the LSR. This device implements both the MPLS control and forwarding planes. The control function of an MPLS label switching router is responsible for distributing routing information to other LSRs, as well as the information required to convert this information into forwarding tables that can then be used by the forwarding function. The MPLS forwarding function is based on the use of a short, fixed-length label. This concept comes from the use of the same concept in layer-2 technologies such as ATM and Frame Relay, which base forwarding actions on a short, fixed-length identifier.
1.1.1 Forward Equivalency Classes
The forwarding function of a router is responsible for forwarding traffic toward its ultimate destination. The information in the forwarding table is programmed based on information from the control plane. If a packet is not delivered via a local interface directly to the destination, the router must forward the packet toward the ultimate destination using a port that will steer that traffic on a path considered most optimal by the routing function. For this reason, a router must forward traffic toward its destination via a next-hop router. This next-hop router may be the next-hop along the most optimal path for more than one destination subnetwork, so many packets with different network layer headers may be forwarded to the same next-hop router via the same output port. The packets traversing that router can then be organized into sets based on equivalent next-hop network nodes. We call such a set a Forward Equivalency Class (FEC). Thus, any packet that is forwarded to a particular next-hop is considered part of the FEC, and can thus be forwarded to the same next-hop. One important feature of the FEC is the granularity of the classification of traffic it can encompass. Since the FEC is based on a routing next-hop, it can include different classifications of packets. For example, since the routing information for a particular next-hop classification can be based on a destination prefix, it might include every packet traveling toward that destination. In this way, the granularity of packets classified by that FEC is quite coarse. However, if the routing database has programmed some next-hops for some traffic based on an application layer, for example, the traffic granularity might be much finer.
1.1.2 The MPLS Shim Header
MPLS packets are encapsulated using an MPLS shim header. The header has this name because it defines an additional header that is placed—or shimmed—between existing layer-2 and layer-3 headers. Curiously, the verb comes from the noun, not the other way around. Therefore, the shim header is so called because it is a small object that is inserted—shimmed—in between the existing layer-2 and layer-3 headers. Figure 1.1 shows the MPLS shim header format. The shim header comprises a sequence of one or more label stack entries. The entries in the sequence can be viewed together as a conceptual stack. A label stack entry comprises several components: label, EXP bits, the bottom of the stack bit, and TTL. The first element is the MPLS label. The label is a fixed-length 20-bit quantity that represents the label used to switch a packet. This label has local significance on a given interface between two neighboring LSRs only. That is, a label taken out of the context of a specific interface between two LSRs may or may not be found to be useful, or may be assigned to a different segment of an LSP. The second portion of the header is 3 bits called the experimental (EXP) bits. These bits are reserved for experimental use, such as for the purposes of classifying LSPs using Differentiated Services code points. The next element of the shim header is a single bit used to indicate the “bottom of the stack.” This bit is set to 1 for the last entry in the label stack (i.e., for the bottom of the stack) and 0 for all other label stack entries. The fourth and final element in the stack is an 8-bit quantity called the time-to-live (TTL) field. The format of a label stack entry is detailed in Figure 1.2.
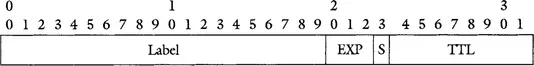
Figure 1.1 MPLS shim header format.

Figure 1.2 The MPLS label stack as it appears within the MPLS shim header.
The Label Stack
MPLS packets may contain more than one label. Depending on the application, it may be desirable to nest label switched paths (LSPs). For example, some TE and VPN operations find it useful to nest LSPs. When labels are nested, they are represented in the MPLS shim header as a stack structure, that is, a LIFO queue. The label stack is represented as a sequence of “label stack entries” in this stack. The topmost label appears closest to the layer-2 header, and the bottommost closest to the layer-3 header. Figure 1.2 demonstrates the label stack as a sequence of label stack entries. Each label stack entry is represented by 4 octets or 32 bits of data. Only the topmost label stack entry is used for any single lookup in the MPLS Label Forwarding Information Base (LFIB).
1.1.3 MPLS Label Switching
The MPLS forwarding plane is responsible for forwarding traffic based on an MPLS label. An MPLS label is a short, fixed-length 20-bit value (see Figure 1.1). The MPLS label has no structure. The MPLS label only has local significance between any two LSRs; therefore, the same label can be reused simultaneously within an MPLS-enabled network. In order for an MPLS LSR to be able to switch an MPLS packet, the label used in that packet’s header must represent an entry in the MPLS LFIB of that LSR. The LFIB is essentially the label-to-label switching database used to program the LSR’s forwarding plane. Once a packet is received, its label will be used by the forwarding plane to make a decision on where to forward the packet. At the edges of an MPLS-enabled network, label switching routers will map IP packets into FECs based on information provided by the MPLS control plane. Once classified into a FEC, the forwarding plane will be able to encapsulate any packet it receives that matches that FEC using the next-hop MPLS label assigned to that FEC.
Although...
Table of contents
- Cover image
- Title page
- Table of Contents
- The Morgan Kaufmann Series in Networking
- Copyright
- Dedication
- Foreword
- List of Tables
- Preface
- Chapter 1: Introduction
- Chapter 2: Management Interfaces
- Chapter 3: The MPLS Label Switching Router Management Information Base (MPLS-LSR MIB)
- Chapter 4: The MPLS Label Distribution Protocol MIB (MPLS–LDP MIB)
- Chapter 5: The MPLS Forward Equivalency Class to Next-Hop Label Forward Entry MIB (MPLS-FTN MIB)
- Chapter 6: The Interfaces MIB and MPLS
- Chapter 7: Offline Traffic Engineering
- Chapter 8: The MPLS Traffic Engineering MIB (MPLS-TE MIB)
- Chapter 9: NetFlow Accounting
- Chapter 10: Traffic Matrix Statistics
- Chapter 11: The MPLS Virtual Private Networking MIB (PPVPN-MPLS-VPN MIB)
- Chapter 12: Future Directions for MPLS Network Management
- Appendix A: IETF and Other Standards Bodies
- Appendix B: MPLS-TC MIB
- Glossary
- Bibliography
- Index
- About the Author
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access MPLS Network Management by Thomas D. Nadeau in PDF and/or ePUB format, as well as other popular books in Computer Science & Computer Networking. We have over one million books available in our catalogue for you to explore.