
eBook - ePub
Hiding Behind the Keyboard
Uncovering Covert Communication Methods with Forensic Analysis
This is a test
- 254 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Hiding Behind the Keyboard
Uncovering Covert Communication Methods with Forensic Analysis
Book details
Book preview
Table of contents
Citations
About This Book
Hiding Behind the Keyboard: Uncovering Covert Communication Methods with Forensic Analysis exposes the latest electronic covert communication techniques used by cybercriminals, along with the needed investigative methods for identifying them. The book shows how to use the Internet for legitimate covert communication, while giving investigators the information they need for detecting cybercriminals who attempt to hide their true identity. Intended for practitioners and investigators, the book offers concrete examples on how to communicate securely, serving as an ideal reference for those who truly need protection, as well as those who investigate cybercriminals.
- Covers high-level strategies, what they can achieve, and how to implement them
- Shows discovery and mitigation methods using examples, court cases, and more
- Explores how social media sites and gaming technologies can be used for illicit communications activities
- Explores the currently in-use technologies such as TAILS and TOR that help with keeping anonymous online
Frequently asked questions
At the moment all of our mobile-responsive ePub books are available to download via the app. Most of our PDFs are also available to download and we're working on making the final remaining ones downloadable now. Learn more here.
Both plans give you full access to the library and all of Perlego’s features. The only differences are the price and subscription period: With the annual plan you’ll save around 30% compared to 12 months on the monthly plan.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes, you can access Hiding Behind the Keyboard by Brett Shavers,John Bair in PDF and/or ePUB format, as well as other popular books in Computer Science & Cyber Security. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1
Laying the Foundation of Covert Communications
Abstract
Communication is a requirement for business operations, government functions, and human-to-human interaction to exist. Without communication, none of these will be possible. From simple conversations to the most advanced encrypted communications, information must transit from person to person. The vast majority of communications are legitimate for human relationships; however, some communications either facilitate criminal acts or are actually criminal in nature. The focus of uncovering covert and anonymous communications is to undermine the criminal elements of communications in order to prevent, detect, and reduce crime.
Keywords
Anonymous; Communication; Covert; Criminal activity; Encryption; Government; History of communications; Investigations; Methods; Personal communicationIntroduction
You have probably taken communication courses in either high school or college and been taught how to effectively communicate in business and personal relationships. These types of communication courses are valuable in many aspects, but do not relate to the investigative methods you will see in this book. I intend to give you sufficient and necessary principles, concepts, and practical methods to not only uncover covert communications but also determine the content of the conversations using both forensic analysis and interpretation of data.
You will notice that much of the information in this book details “how to communicate anonymously and covertly” alongside with “how to find anonymous and covert communications.” Unlike driving a car where you do not need to know engines or transmissions work, as an investigator, you do need to understand how these types of communications take place in order to understand the methods to uncover and analyze them. The technical explanations may be beyond the scope of a nonforensic investigator, but do not be discouraged as you read the descriptions and methods. Investigators need to know how certain methods are used in order to look for them during investigations.
Fair warning, there will be communications that you will not be able to find or decipher if found in the course of your examination. Even the communications you uncover and decipher may not be directly attributed to your targets technology and good old-fashioned spy tradecraft works well to hide communications from the sets of prying eyes. We are going after the covert communications that can be found with gumshoe detective work to be analyzed and deciphered with effective uses of both technology and brain power. We are also hoping to find communication mistakes made by your targets. Given a 100 communication efforts using a dozen different types of methods, there is a risk of failure by your targets in one or more of their communication deliveries. These mistakes are more than freebies for your investigation; their contents are potentially a goldmine of information. As will be shown, having found one key bit of evidence can unlock an entire chain of communications.
Discussing covert communications sometimes involves breaking codes. However, the focus of this book is not code breaking as much as it is to first find the communications and then break the anonymity by identifying your targets. Much of the code-breaking topics in this book will be for illustrative purposes and not for mastering the cracking of ciphers since that is a topic already covered in many published books.
A Brief History of Covert Communication
History is interesting, but understandably for some, history is in the past and therefore, not particularly important. In the manner of how history applies to your reading of this book, I refer to a few historical events where intercepting and deciphering communications were instrumental in outcomes and relevant to the present.
At a minimum, by understanding covert and anonymous communications has been in existence for thousands of years and is still being used, makes a strong point to consider the importance of the history of covert communication. In order for any nation to have security from enemies, covert communication is used to exchange information for national security. A nation that has access to its enemy’s communications is at a tactical, strategic, and economical advantage.
During World War II, Germany employed the use of the “Enigma” enciphering machine, seen in Fig. 1.1. The Enigma “had the potential to create immense numbers of electrically generated alphabets” (Singh, 1999). Communications created with the Enigma were extremely secure, and the German war effort was substantially successful because of their security of communications. A nation at war that can safely and securely communicate is a nation with a distinct advantage. As Germany relied more upon the Enigma, the reliance became part of Germany’s downfall once the Enigma code was broken. Once the Enigma code was broken, the Enigma was used against Germany as the Allies would know their most secretive plans. (German encoding machine—Enigma. World War II. Skanderborg Bunker Museum, Denmark—2004.)
The Enigma story directly relates to covert communications today, whether it is nation states fighting each other or between drug dealers conspiring to commit crimes. Once the communication methods are intercepted and decoded, your targets are operating in the clear, yet at the same time, they are blissfully unaware that their secret plans are no longer secret. When your investigation reaches a point where communications are being intercepted, it takes a concerted effort not to disclose or cause any suspicion the communication method has been compromised.

Figure 1.1 Enigma machine used during World War II.
Such is the case for wiretaps. The amount of time, effort, and energy to gain legal authority for a wiretap typically is immense. In fact, in most cases, all other methods are typically exhausted leaving a wiretap as the only option in the investigation. Being legally approved to conduct a wiretap is only the beginning as the telephone numbers must be identified along with the targets. Again, this is a very difficult process, especially since cell phones are constantly being replaced with new phones and new features.
To enable gaining the most intelligence from a wiretap, investigations are generally prolonged without disclosing the existence of a wiretap. During this time, investigators act upon some of the information obtained in the wiretap without disclosing the fact there is a wiretap in hopes the criminal organization will continue to use the telephones to communicate (or e-mail, etc.). As with many wiretap investigations, as soon as the targets feel law enforcement is closing in, phones are discarded (“dumped”), just in case they are compromised, to be replaced by entirely different phones and phone numbers. It is a careful balance to act upon information gained from a compromised communication channel and tipping off the targets.
There are few greater threats today than the war against terrorism and uncovering covert communication that facilitates terrorist attacks is a priority in every country. A well-known covert communication method used by not only terrorists but also anyone wanting to avoid sending e-mails that may be discovered is that of using web-based e-mail draft folders. With this method, two or more persons have the login credentials to an e-mail account. To communicate, any person with the credentials simply creates an e-mail and rather than send it, stores it in a draft folder which physically resides on an e-mail server of the e-mail provider. The other users of the account can access the drafts, and the e-mail is never sent outside the service provider’s network.
As an analogy, this method is akin to having a safe-deposit box in a bank vault with more than one person having access to the box. Messages can be left in the box for another to read, yet the message never leaves the vault. E-mail drafts are an extremely simple, yet effective means of communication using a third-party service provider as long as the e-mail account is unknown to investigators.
An important point to make about this older method using a draft e-mail folder is that even as the disclosure of this technique is now common knowledge, it is still employed today. Even those who can be considered experts in covert communication use this method with the knowledge that the security is only in concealment of the e-mail account. A recent example of this draft e-mail method in 2012 was an extramarital affair discovered through a Federal Bureau of Investigation (FBI) investigation between the Central Intelligence Agency (CIA) Director General David Petraeus and author Paula Broadwell (Beary et al., 2013). The FBI, investigating a cybercrime allegation, discovered that Petraeus and Broadwell communicated secretly using a draft e-mail folder, which effectively ended their careers by uncovering their extramarital affair. By not sending e-mails to each other, the risk of discovery was very low.
Communicating through e-mail drafts, as seen in Fig. 1.2 is effective for covert communications until the account is discovered. Once discovered, potentially only a single e-mail may be left in the e-mail account since it most likely being used for a single draft e-mail communication. Potentially, once the message has been read by the intended party, the e-mail is deleted. In the case of this type of communication, the best method of investigation is monitoring the account draft folder in real time in order to capture the communications and not rely upon an empty folder as an indication of nonuse. Chapter “Anti-Forensics” details e-mail investigations as well as other means of online anonymous and covert communications.
The draft e-mail folder is easily defeated with search warrants, but only after the e-mail account has been identified. Throughout your investigations, you will find that nearly all communications between your targets involve an innocent third party, such as an e-mail provider or cell phone service provider. The reliance on third parties to communicate is a double-edged sword for your targets. For security, a third-party provider helps maintain anonymity if they do not require users to disclose personal information. Third-party providers also reduce research and development costs for communication methods since using commercially available tools are available worldwide and many times are free.
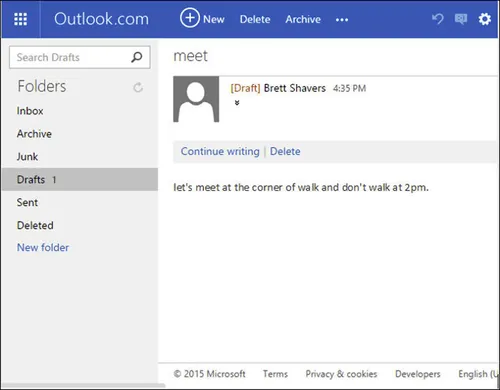
Figure 1.2 Draft e-mail stored but not sent.
Conversely, because of the reliance of third-party providers, your efforts as an investigator should also focus on obtaining assistance from these providers to identify your targets. Although some third-party providers may either refuse to cooperate with law enforcement or intentionally discard user information as part of their service, the vast majority of companies wish not to be part of the facilitation of crime or terrorist acts. Tips on gauging the cooperation of a third party before asking for their help is covered throughout this book as it is also not uncommon that a third party will warn a user of a pending civil or government investigation.
If a country can lose a war and a general lose a career by having their covert communications compromised, you can succeed in your investigations using the same methods that have been in use for thousands of years to uncover and break covert communications. The key is first finding the communications.
Covert Communication Overload
In its basic form, communication consists of a source sending information to a receiver. Investigators generally want to know the identities of the sender and receiver, the content of the message, the method of transmission, and the metadata associated with the message. Typically, all information is desired, and once investigators have the information, the targets are at a distinct disadvantage and the investigators can most likely, capture subsequent communications if the targets do not change their methods.
Fig. 1.3 is a visual that displays different physical methods that targets can use to convey information between each other. Technology allows for a wide range of transmission methods, such mobile devices, e-mail, telephones, and even fax machines. Even the regular mail system is a commonly used method of conveying clandestine of covert information.
Be prepared for discomfort and frustration in your quest to uncover covert clandestine and anonymous communications. Suspects under investigation are typically, if not always, using more than one type of method at the same time. Your targets are probably using smartphones to call and text each other, using computers to e-mail each other, and maybe even sending letters through the mail. To compound the multitude of tec...
Table of contents
- Cover image
- Title page
- Table of Contents
- Copyright
- Foreword
- Introduction
- About the Authors
- Acknowledgments
- Chapter 1. Laying the Foundation of Covert Communications
- Chapter 2. The Tor Browser
- Chapter 3. Triaging Mobile Evidence
- Chapter 4. Mobile Extraction Issues
- Chapter 5. Data Hiding
- Chapter 6. Cryptography and Encryption
- Chapter 7. Antiforensics
- Chapter 8. Electronic Intercepts
- Chapter 9. Digital Identity
- Chapter 10. Putting It All Together
- Chapter 11. Closing Thoughts
- Index