
eBook - ePub
Securing Intellectual Property
Protecting Trade Secrets and Other Information Assets
This is a test
- 288 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Securing Intellectual Property
Protecting Trade Secrets and Other Information Assets
Book details
Book preview
Table of contents
Citations
About This Book
Most employeers are astounded at how easily and quickly their proprietary information can get out of their control. In a large number of cases, theft of trade secrets often involves employees leaving a company to start their own business or work for a direct competitor.Nearly all books that address the topic of trade secrets have the "spy vs. spy" perspective. The author approaches the topic from a practical business perspective and not simply creating "paranoia" for paranoia's sake. The material for this book comes from the author's extensive work experience as a computer forensics consultant and manager on numerous theft of trade secrets cases.
- No-nonsense solutions to the most common intellectual property problems facing security managers, computer security professionals, corporate legal counsel, and human resource managers
- Sample agreements and forms that address specific business needs
- Coverage of threats ranging from physical security lapses to hackers to social engineering
Frequently asked questions
At the moment all of our mobile-responsive ePub books are available to download via the app. Most of our PDFs are also available to download and we're working on making the final remaining ones downloadable now. Learn more here.
Both plans give you full access to the library and all of Perlego’s features. The only differences are the price and subscription period: With the annual plan you’ll save around 30% compared to 12 months on the monthly plan.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 1000+ topics, we’ve got you covered! Learn more here.
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more here.
Yes, you can access Securing Intellectual Property by Information Information Security in PDF and/or ePUB format, as well as other popular books in Law & Intellectual Property Law. We have over one million books available in our catalogue for you to explore.
Information
Chapter 1. Elements of a Holistic Program
Introduction
In many environments, security as an element of business culture has been hit with the double-whammy—that is, it suffers from both an image problem and an identity crisis. Many people think of corporate security as the “guards, guns, and gates” guys and cyber security as those “snoops who read employees' e-mail.”
Security often is seen as a controlling or constricting force within an enterprise. It is frequently thought of as something that gets in the way of business. And lacking either a real mandate or a bold vision, many people within security slip into a reactive mode and resort to playing whack-a-mole, thus contributing to the bad image and deepening the identity crisis.
Security also is harried from a pack of false memes, which hound it, as well as some structural impairment, which hobbles it.
False Memes Lead People the Wrong Way
For example, a false meme tells you that teenage hackers with purple Mohawks and skateboards are responsible for most network break-ins; they don't really mean any real harm or do much damage. That might have been true fifteen years ago, but it hasn't been true for quite some time.
Another false meme assures you that 80 percent of all serious cyber-crime is perpetrated by insiders, for example, by dishonest or disgruntled employees. Again, looking in the rear-view mirror, at a great distance, that might have been true years ago, but it is a dangerous assumption in today's world. It is not that the insider threat has been diminished; it is that the threat from outside has increased dramatically. Furthermore, the lines between insider and outsider have been blurred both by technology and business practice.
A third false meme (there are several others) states that “most industrial espionage is done by the turning of insiders.” Like the notion about “insiders” being the cause of most problems, this meme about the turning of insiders is particularly dangerous because it is a half-truth. The turning of insiders was the principle method, and it still is a major factor, but the business environment has changed radically, and methods of collection, and those eager to collect, have changed along with it.
From the Industrial Age to the Information Age
Of course, just as the Agricultural Age did not drop away when we entered into the Industrial Age, the Industrial Age is still with us, but an added dimension, the Information Age, is laid over the top of the two earlier paradigms. We are up to our necks in what Toffler called the Third Wave, and it has brought with it tremendous opportunity and profound challenge.
Unfortunately, this Third Wave has yet to sweep away a lot of Second Wave thinking about the nature of security.
To understand what security should look and feel like in the twenty-first century, pull out a piece of black paper. First, draw a big circle on it, and write along the curve of the circle, “Global Economy.” Next, draw a second big circle of the same circumference on top of the first circle, and then write along side of the curve of this second, superimposed circle, “Cyberspace.”
Within these two dimensions, which share the same space, you cannot draw a perimeter for your enterprise. And certainly, if you cannot draw a perimeter, you cannot protect it. Of course, you could draw a smaller circle, or a square, within the shared circle of the global economy and cyberspace, and you could imagine that the lines of the smaller shape delineated your enterprise's perimeter, but you would be deluding yourself. The reality is that the smaller shape is permeated by both the global economy and cyberspace, both are inside of your enterprise, you cannot keep them outside, and they are integral to how we do business today.
This new world demands a new security paradigm. We think of it as a holistic vision of security.
We have described the bad image, the identity crisis, and the false memes, but what about the structural impairment? Just as intelligence suffers from stove-piping (i.e., unless intelligence can be cross-referenced and aggregated in many ways, and analyzed afresh from different angles, something very important will probably slip by), so does security; if personnel security, physical security, and information security are all stove-piped within an enterprise, each is less than it could be, and all could well be working at cross-purposes. Figure 1.1 shows how awareness and intelligence can help mitigate risk and threats within an organization.
Figure 1.1. Personnel, Physical, and Information Security Mitigate the Scope of Risks and Threats
In life, in nature, in business, and in security, everything is interconnected, one way or another, just as the size of the glacier pack impacts the flow of the river, which, in turn, impacts the irrigation and reservoirs upon which human habitation has come to rely. In security, all the various elements interconnect for good or bad. If your most sensitive information is stored on an insecure server, your investment in physical and personnel security will be wasted. Conversely, if inadequate attention is paid to your physical security, then all your diligence in implementing personnel and information security controls could be for naught. Figure 1.2 shows how integration of physical, personnel, and cyber security helps narrow the scope of risks and threats within an organization.
Figure 1.2. Integrating Physical, Personnel, and Cyber Security

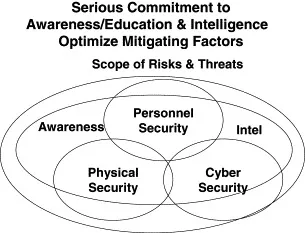
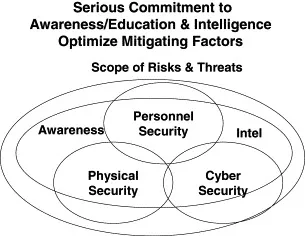
Each has to strengthen the other; each has to resonate with the whole (see Figure 1.3).
Figure 1.3. Serious Commitment to Awareness/Education and Intelligence Optimize Mitigating Factors
Here are some recommendations for a comprehensive program:
- Organization: Where security reports within an organization is perhaps the most vital issue of all. Consider appointing a Chief Security Officer (CSO), who reports to either the Chief Executive Office (CEO) or the Chief Financial Officer (CFO). This person should hold the reins of personnel security, physical security, and information security, and should not be a stranger to the boardroom.
- Awareness and Education: Educate your workforce on an ongoing basis about the threats of economic espionage, intellectual property theft, counterfeiting, and piracy. Help them understand your expectation that they will protect the enterprise's intellectual property, and by extension, their own livelihood. Provide general education for the entire workforce, and specialized education for executives, managers, technical personnel, among others.
- Personnel Security: Implement a “Personnel Security” program that includes both background investigations and termination procedures. You need policies that establish checks and balances, and you need to enforce them. Know the people you are going to hire. Don't lose touch with them while they work for you. Consciously manage the termination process if and when they leave the enterprise.
- Information Security: Recruit certified information security professionals (e.g., CISSP, CISM, etc.). Adopt best practices, and establish a baseline. Utilize appropriate information security technologies, such as fire...
Table of contents
- Brief Table of Contents
- Table of Contents
- Copyright
- Preface
- Chapter 1. Elements of a Holistic Program
- Chapter 2. Trade Secrets and Nondisclosure Agreements
- Chapter 3. Confidentiality, Rights Transfer, and Noncompetition Agreements for Employees
- Chapter 4. IT Services—Development, Outsourcing, and Consulting
- Chapter 5. How to Sell Your Intellectual Property Protection Program
- Chapter 6. Case Study
- Chapter 7. When Insiders and/or Competitors Target a Business's Intellectual Property
- Chapter 8. When Piracy, Counterfeiting, and Organized Crime Target a Business's Intellectual Property
- Chapter 9. Physical Security
- Chapter 10. Protecting Intellectual Property in a Crisis Situation
- Chapter 11. Top Ten Ways to Shut Down Hackers
- Appendix 1. Mutual Non-Disclosure Agreement
- Appendix 2. Evaluation Agreement (Pro-Recipient)
- Appendix 3. Employee Agreement
- Appendix 4. Software Development Agreement
- Appendix 5. Software Consulting Agreement (Favors Consultant)
- Appendix 6. Software Consulting Agreement (Favors Customer)
- Appendix 7. Web Site Development Agreement
- Appendix 8. Web Hosting Agreement
- Appendix 9. U.S. Department of Justice Checklist for Reporting a Theft of Trade Secrets Offense
- Index