
- 212 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
The Cybersecurity Self-Help Guide
About this book
Cybercrime is increasing at an exponential rate. Every day, new hacking techniques and tools are being developed by threat actors to bypass security systems and access private data. Most people do not know how to secure themselves, their devices, and their media shared online.
Especially now, cybercriminals appear to be ahead of cybersecurity experts across cyberspace. During the coronavirus pandemic, we witnessed the peak of cybercrime, which is likely to be sustained even after the pandemic.
This book is an up-to-date self-help guide for everyone who connects to the Internet and uses technology. It is designed to spread awareness about cybersecurity by explaining techniques and methods that should be implemented practically by readers.
Arun Soni is an international award-winning author who has written 159 books on information technology. He is also a Certified Ethical Hacker (CEH v8) from the EC-Council US. His achievements have been covered by major newspapers and portals, such as Business Standard, The Economic Times, Indian Express, The Tribune, Times of India, Yahoo News, and Rediff.com. He is the recipient of multiple international records for this incomparable feat. His vast international exposure in cybersecurity and writing make this book special. This book will be a tremendous help to everybody and will be considered a bible on cybersecurity.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
1 All About IP Addresses
Scenario
Objectives
- Concept of IP address and classification
- Step-by-step demonstration on how one can track an IP address
Introduction to IP Address
About the Network Interface Card
Understanding Public and Private IP Addresses
Public IP
- 49.36.224.184
- 2405:101:1246: ddb6:29b1:76cc:6089
Private IP
- 192.168.0.0 to 192.168.255.255 [65,536 IP addresses]
- 172.16.0.0 to 172.31.255.255 [1,048,576 IP addresses]
- 10.0.0.0 to 10.255.255.255 [16,777,216 IP addresses]
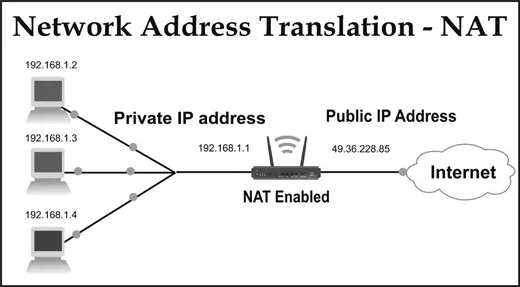
Network Address Translation
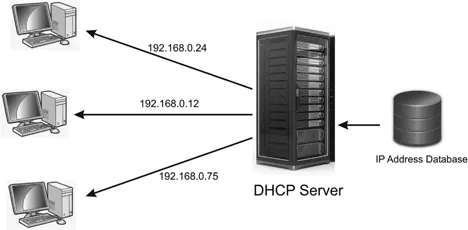
About Dynamic Host Configuration Protocol (DHCP)
Understanding IPv4 and IPv6 Addressing System
IPv4 Address
Table of contents
- Cover
- Half Title
- Title Page
- Copyright Page
- Contents
- Preface
- Introduction The World of Cybercrime
- Chapter 1 All About IP Addresses
- Chapter 2 Router Security
- Chapter 3 Applying 2-Factor Authentication (2-FA)
- Chapter 4 Has My Email Been Hacked?
- Chapter 5 Implementing Online Parental Control
- Chapter 6 The Golden Rule to Be on Social Media
- Chapter 7 Smartphone Security/Finding Your Lost Phone
- Chapter 8 All About Proxy and VPN
- Chapter 9 Collecting the Digital Evidence
- Chapter 10 Debit/Credit Card Security
- Chapter 11 Website Hacking and Security Implementation
- Chapter 12 Protection From Email Spoofing
- Chapter 13 Backup and Encryption
- Chapter 14 Must-Have Apps for Women and Elderly
- Chapter 15 Penetration Testing Using a Smartphone
- Chapter 16 P2P Money Transfer Apps and More
- Chapter 17 Final Thirty Tips for Online Safety
- Chapter 18 Reporting a Cybercrime
- Further Reading
- Index
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app