
Implementing DevSecOps with Docker and Kubernetes
An Experiential Guide to Operate in the DevOps Environment for Securing and Monitoring Container Applications (English Edition)
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Implementing DevSecOps with Docker and Kubernetes
An Experiential Guide to Operate in the DevOps Environment for Securing and Monitoring Container Applications (English Edition)
About This Book
Building and securely deploying container-based applications with Docker and Kubernetes using open source tools.
Key Features
? Real-world examples of vulnerability analysis in Docker containers.
? Includes recommended practices for Kubernetes and Docker with real execution of commands.
? Includes essential monitoring tools for Docker containers and Kubernetes configuration.
Description
This book discusses many strategies that can be used by developers to improve their DevSecOps and container security skills. It is intended for those who are active in software development. After reading this book, readers will discover how Docker and Kubernetes work from a security perspective.
The book begins with a discussion of the DevSecOps tools ecosystem, the primary container platforms and orchestration tools that you can use to manage the lifespan and security of your apps. Among other things, this book discusses best practices for constructing Docker images, discovering vulnerabilities, and better security. The book addresses how to examine container secrets and networking. Backed with examples, the book demonstrates how to manage and monitor container-based systems, including monitoring and administration in Docker.
In the final section, the book explains Kubernetes' architecture and the critical security threats inherent in its components. Towards the end, it demonstrates how to utilize Prometheus and Grafana to oversee observability and monitoring in Kubernetes management.
What you will learn
? Familiarize yourself with Docker as a platform for container deployment.
? Learn how Docker can control the security of images and containers.
? Discover how to safeguard and monitor your Docker environment for vulnerabilities.
? Explore the Kubernetes architecture and best practices for securing your Kubernetes environment.
? Learn and explore tools for monitoring and administering Docker containers.
? Learn and explore tools for observing and monitoring Kubernetes environments.
Who this book is for
This book is intended for DevOps teams, cloud engineers, and cloud developers who wish to obtain practical knowledge of DevSecOps, containerization, and orchestration systems like Docker and Kubernetes. Knowing the fundamentals of Docker and Kubernetes would be beneficial but not required.
Table of Contents
1. Getting Started with DevSecOps
2. Container Platforms
3. Managing Containers and Docker Images
4. Getting Started with Docker Security
5. Docker Host Security
6. Docker Images Security
7. Auditing and Analyzing Vulnerabilities in Docker Containers
8. Managing Docker Secrets and Networking
9. Docker Container Monitoring
10. Docker Container Administration
11. Kubernetes Architecture
12. Kubernetes Security
13. Auditing and Analyzing Vulnerabilities in Kubernetes
14. Observability and Monitoring in Kubernetes
Frequently asked questions
Information
CHAPTER 1
Getting Started with DevSecOps
Structure
- From DevOps to DevSecOps
- Getting started with DevSecOps
- DevSecOps methodologies
- Continuous integration and continuous delivery
- DevSecOps tools
Objectives
From DevOps to DevSecOps
- A developer writes the code using the development environment of their choice and uploads it to a centralized code repository like Git or Bitbucket.
- The Continuous Integration (CI) server downloads the source code from the central repository and packages the built artifacts and binaries. For example, Docker images are created and pushed to the Docker registry for containerized applications.
- These artifacts and binaries are downloaded from the repository to be deployed in different pre-production and production environments, where they are built using container technologies like Docker and Kubernetes.
- Containers are built from the Docker images. If the environment is not a containerized one (like VMs), sometimes the process is just copying the binaries to a drop location.
- Add automated security testing techniques, such as fuzz test and software penetration testing, to the software development lifecycle or system integration cycle
- Standardization of the integration cycle to reduce the introduction of errors
- Introduction of security issues and limitations to software and systems development teams at startup of the projects
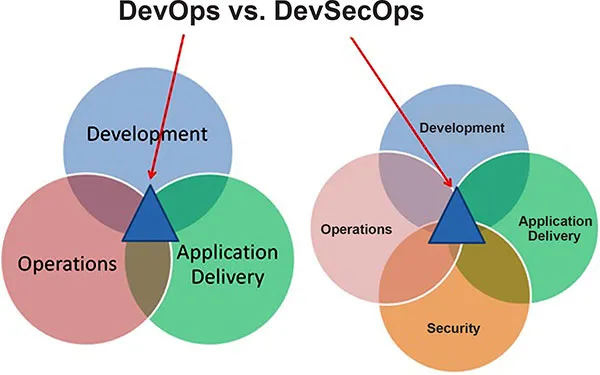
Getting started with DevSecOps
- Integrate security tools in the development integration process
- Prioritize security requirements as part of the product’s backlog
- Collaborate with the security and development teams on the threat model
- Review infrastructure-related security policies prior to deployment
Advantages of implementing DevSecOps
- Early identification of potential vulnerabilities in the code is encouraged.
- Greater speed and agility in applying security in all phases of development.
- Throughout the development process, tools and mechanisms are provided to quickly and efficiently respond to changes and new requirements.
- Better collaboration and communication between teams involved in development, as in DevOps.
DevSecOps lifecycle
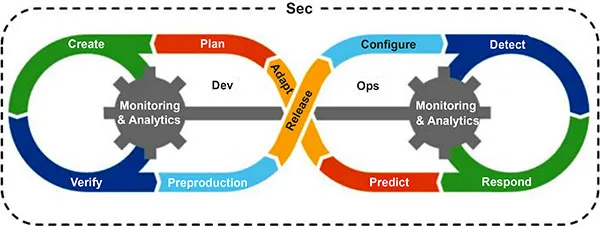
- More automation up front reduces the chances of mismanagement and lowers errors.
- According to Gartner, “DevSecOps can lead to security functions such as Identity and Access Management (IAM), firewall, and vulnerability scanning being programmatically enabled throughout the DevOps lifecycle, leaving security teams free to establish policies.”
- Security incidents are reduced and security is improved through shared responsibility between all teams.
- Vulnerability remediation costs are reduced.
ShiftLeft security
Table of contents
- Cover Page
- Title Page
- Copyright Page
- Dedication Page
- About the Author
- About the Reviewers
- Acknowledgements
- Preface
- Errata
- Table of Contents
- 1. Getting Started with DevSecOps
- 2. Container Platforms
- 3. Managing Containers and Docker Images
- 4. Getting Started with Docker Security
- 5. Docker Host Security
- 6. Docker Images Security
- 7. Auditing and Analyzing Vulnerabilities in Docker Containers
- 8. Managing Docker Secrets and Networking
- 9. Docker Container Monitoring
- 10. Docker Container Administration
- 11. Kubernetes Architecture
- 12. Kubernetes Security
- 13. Auditing and Analyzing Vulnerabilities in Kubernetes
- 14. Observability and Monitoring in Kubernetes
- Index