The proliferation and influence of private security is often hailed as one of the most significant changes in international politics and it animates periodically debates ranging from the privatization of foreign policy to the ethics of contracting, from the cost effectiveness of companies to the tensions between private contractors and government military personnel, from democratic accountability to the relations between state and non-state actors.
This book addresses the question of how social norms produce or prevent state choices in contemporary private security governance structures. What drives change in regulation and what norms shape global initiatives and individual state choices? This is the central inquiry of the book. The politics of private security governance are not explained by conventional theories that claim that all global issues reflect underlying military and economic capabilities. Reflecting the realist tradition in international relations, analysts find it difficult to explain how regulation evolved in spite of conflicting national interests and cannot explain the involvement of states that had no strategic interest in cooperation (Avant 2016). Yet, constructivist approaches are challenged as well. Assuming the existence of private security norms is simplistic if these cannot be shown to be determinants of state behavior. There is a gap in our understanding of the relation between norms and their varying influence on state and interstate policymaking that this book aims at filling. From the start, which body of norms guides states in their relations to private security and what remains of the influence of the anti-mercenary norm, the most critical of all? Has the anti-mercenary norm been reformulated and limited? What shapes severe regulatory responses at the state level, including prohibition private security? These are the questions that the book aims at illuminating.
In the developing countries—where the state’s monopoly on violence is particularly lacking—and the urgency of modernization and subsistence is greatest, the questions are particularly relevant. In these contexts, the state’s monopoly of legitimate force is increasingly enmeshed in networks and relations that cannot always be contained within the boundaries of the national state (Abrahamsen and Williams 2010). Since Abrahamsen and Williams’ seminal contribution, other trends have characterized the developing world. I offer an original account both of the growth of Chinese private military and security contractors (PMSCs) in Africa1 and of Chinese participation to regulatory processes. How does Beijing promote or inhibit regulatory cooperation on matters of private security? The answer proposed in the book lies both in the history of the anti-mercenary norm and in distinct path of state formation of Chinese state (Chap. 10). The book explores Chinese participation to expert meetings and state conferences, and the policy choices made by a major player in the African continent.2
Finally, an intense evolution in Information and Communications Technology, including social media, has impacted international politics. The trend was acknowledged and identified earlier, as it initially revolved around CCTV and alarm systems with abstract systems and institutions reinforcing the expertise of private authority (Abrahamsen and Williams 2010, pp. 221–222). Since then, non-state actors with decentralized networks have challenged the boundaries of activism and rebellion against the state, with the phenomenon of radicalization gaining dramatic notoriety. Against these challenges, both PMSCs, and the private sector in general, are harnessed in support of a technologically complex and virtual conflict (Carmola 2010, pp. 167–170). What are then the normative basis to connect manned private security and technologically evolving private security? This book also aims at answering these evolving questions and uses the exploration of social norms and state choices, to help create bridges for international cooperation in the digital age.
1.1 The Complexity of Naming
1.1.1 Definitions
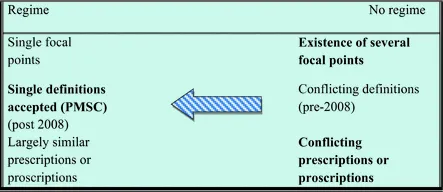
Having recognized the lack of a framework for PMSCs activities, states engaged in multiple initiatives that increasingly used the same definition: the
Montreux Document (hereinafter Montreux or the Document) and the International
Code of Conduct (hereinafter ICoC
or the Code), the UN
Draft
Convention, as well as national legislations governing PMSCs. First and foremost, agreement converged toward the use of a shared identifier—that is, PMSC. Moving from conflicting definitions to an agreed one is an important step of regime
construction, as indicated in Table
1.1. Thus, the first definition for this book is “PMSCs” or private military and security companies—private business entities that provide military and/or security services, irrespective of how they describe themselves. Military and security services include, in particular, “armed guarding and protection of persons and objects, such as convoys, buildings and other places; maintenance and operation of weapons systems; prisoner detention; and advice to or training of local forces and security personnel” (This is the definition in the Montreux Document, p. 9. Also cf. Chap.
2.) The primary business of PMSCs is not the production and procurement of hardware, typical of the defense industry, but the procurement and delivery of services
both in peace and in conflict zones.
Table 1.1Regime construction
The tractability of the issue-area has necessitated a disassociation from the categories of mercenarism and privateering , as the book is going to elucidate; and regulatory cooperation still consists in leading—or facilitating—the acceptance of the term PMSC, the invention of which I see as akin to a “permanent inherited patronym.”
In fact, an extraordinary variation in regulatory choices has characterized the last two decades. Some governments allowed PMSCs, others banned them altogether (cf. Chap. 6). In maritime security, several countries have changed policy recommendation almost overnight, from strongly advising against private security to recommending their use (cf. Chap. 7). In Spain , the government chose to authorize and subsidize the fishing industry’s use of PMSCs. The largest Iranian tanker operators, as well as Chinese shipping firms, now use PMSC services for their fleet. How can we then account for heterogeneity in state choices and what explain shift?
1.1.2 “Who Is It That Can Tell Me Who I Am?”
The analysis begins by identifying the actors and choosing the appropriate terms. De Nevers recalled an episode involving AFRICOM’s first commander. He stated in January 2010 that “AFRICOM does not use private military contractors.” Yet, De Nevers continues: “It is important to note, however, that many of the companies contracting with AFRICOM and AFRICAP fall within the broad rubric of PMSCs ” (De Nevers in Kinsey and Patterson 2012a, p. 71). This episode reflects the reticence in the use of the term private security and military company. It is indeed not a coincidence that all studies and accounts of PMSCs begin with the problem of simple definition, as Carmola writes, “that they are ambiguous or polymorphous entities—a mix of old and new, public and private; slippery, and hard to pin down analytically ” (Carmola 2010,...