
- 222 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
SQL Server on Linux
About this book
Bring the performance and security of SQL Server to LinuxAbout This Book• Design and administer your SQL Server solution on the open source Linux platform• Install, configure, and fine-tune your database application for maximum performance• An easy-to-follow guide teaching you how to implement various SQL Server CTP 2.x offerings on Linux—from installation to administrationWho This Book Is ForThis book is for the Linux users who want to learn SQL Server on their favorite Linux distributions. It is not important if you are experienced database user or a beginner as we are starting from scratch. However, it is recommended that you have basic knowledge about relational models. More advanced readers can pick the chapters of their interest and study specific topics immediately. Users from Windows platform can also benefit from this book to expand their frontiers and become equally efficient on both platforms.What You Will Learn• Install and set up SQL Server CTP 2.x on Linux• Create and work with database objects using SQL Server on Linux• Configure and administer SQL Server on Linux-based systems• Create and restore database back-ups• Protect sensitive data using the built-in cryptographic features• Optimize query execution using indexes• Improve query execution time by more than 10x using in-memory OLTP• Track row-versioning using temporal tablesIn DetailMicrosoft's launch of SQL Server on Linux has made SQL Server a truly versatile platform across different operating systems and data-types, both on-premise and on-cloud.This book is your handy guide to setting up and implementing your SQL Server solution on the open source Linux platform. You will start by understanding how SQL Server can be installed on supported and unsupported Linux distributions. Then you will brush up your SQL Server skills by creating and querying database objects and implementing basic administration tasks to support business continuity, including security and performance optimization. This book will also take you beyond the basics and highlight some advanced topics such as in-memory OLTP and temporal tables.By the end of this book, you will be able to recognize and utilize the full potential of setting up an efficient SQL Server database solution in your Linux environment.Style and approachThis book follows a step-by-step approach to teach readers the concepts of SQL Server on Linux using the bash command line and SQL programming language trough examples which can easily be adapted and applied in your own solutions.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Implementing Data Protection
- Crash course in cryptography
- Transparent Data Encryption
- Backup encryption
- Symmetric encryption
- Row-level security
- Dynamic data masking
Crash course in cryptography
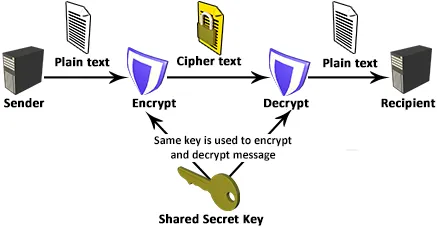
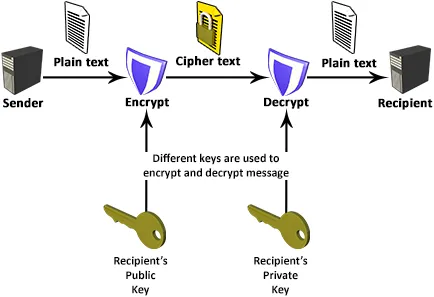
- Encryption: The process of creating an obfuscated message from plain text using a key
- Decryption: The process of returning plain text from an obfuscated message using a key
- Symmetric cryptography
- Asymmetric cryptography
Symmetric cryptography
Asymmetric cryptography
What is a key?
SQL Server cryptographic elements
Table of contents
- Title Page
- Copyright
- Credits
- About the Author
- About the Reviewer
- www.PacktPub.com
- Customer Feedback
- Preface
- Linux Distributions
- Installation and Configuration
- SQL Server Basics
- Database in the Sandbox
- Sample Databases
- A Crash Course in Querying
- Backup and Recovery Operations
- User Management
- Implementing Data Protection
- Indexing
- In-Memory OLTP
- Beyond SQL Server
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app