
eBook - ePub
Continuous Auditing
Theory and Application
- 275 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
eBook - ePub
Continuous Auditing
Theory and Application
About this book
Continuous auditing is a novel emerging technology in academia and practice. The concept of continuous auditing was conceived over two decades ago in academia and we are now at a junction where the auditing profession recognizes the implement-ability and value of a continuous audit. The book's purpose is twofold. First, the book aims to provide academics and practitioners with a compilation of select continuous auditing design science research that can be used as a springboard to future research and development. Second, the book aims to provide readers with an understand of the underlying theoretical concepts of a continuous audit, ideas on how continuous audit can be applied in practice, and what has and has not worked in research.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Publisher
Emerald Publishing LimitedYear
2018Print ISBN
9781787548732, 9781787434141eBook ISBN
9781787434653Continuous Auditing—A New View1
1. INTRODUCTION—CONTINUOUS ASSURANCE THE THEORY3
This volume is intended as an update on the report Continuous Audit (also called Red Book) published by the CICA and AICPA in 1999. In that volume, some basic principles and a vision were presented that served as a basis for additional guidance work by the Institute of Internal Auditors (IIA) in 2005 and the Information Systems Audit and Control Association (ISACA) in 2010. Fifteen years after that 1999 report, this volume presents a much different state-of-the-art, and this essay proposes an expanded set of concepts largely adding to Vasarhelyi and Halper (1991) and joining it with an increasing set of experiences and literature from practice and academia. The evolution of IT, the emergence of big data, and the increasing use of analytics have rapidly changed the landscape and profile of continuous assurance and auditing.4 Many of the current audit standards were initially instituted by legislation based on the Securities Act of 1933 and the Securities Exchange Act of 1934 and progressively developed into the current, ever-evolving set of generally accepted auditing standards, or GAAS. This formalization of “generally accepted” has had an enormous effect on business practices and consequently large effects on the social ecosystem.
Within this context, in addition to the external verification of financial statements, many contexts in need of third-party verification have risen. Consequently, organizations developed internal audit departments, consulting firms introduced auditing services, and some of these needs are being satisfied on an ad hoc basis mainly by external audit firms. Vasarhelyi and Alles (2006), in a study for the AICPA’s Enhanced Business Reporting (EBR) project, characterized the umbrella of verification services as “assurance,” under which falls a set of services such as the “traditional (external) audit,” internal audit, and much of what we later in this paper call “audit-like services.” Several data analytic and monitoring functions of the expanded set of activities that we hereby call continuous assurance have dual or multiple functions serving assurance, management, and other parties. Guidance on materiality, independence, and required procedures will eventually be needed to adapt to the new tools as the environment evolves. This essay illustrates some of these needs.
Groomer and Murthy (1989) and Vasarhelyi and Halper (1991) have respectively argued for and demonstrated the desirability and possibility of “closer to the event” assurance processes. This approach, reflecting the evolution of technology to online, real-time systems, has had slow but progressive adoption both in practice (Vasarhelyi et al, 2012; ACL 2006; PWC 2006)5 and in professional guidance (CICA/AICPA, 1999; IIA, 2005; ISACA, 2010).
1.1. Continuous Process Auditing
Motivating the need for continuous assurance, Vasarhelyi and Halper (1991) state: “There are some key problems in auditing large database systems that traditional auditing (level 1) cannot solve. For example, given that traditional audits are performed only once a year, audit data may be gathered long after economic events are recorded.” To deal with these problems, the AICPA/CICA’s Red Book (1999) introduced the current definition of continuous auditing:
A continuous audit is a methodology that enables independent auditors to provide written assurance on a subject matter, for which an entity’s management is responsible, using a series of auditor’s reports issued virtually simultaneously with, or a short period of time after, the occurrence of events underlying the subject matter. (CICA/AICPA, 1999)
Research studies have provided a much broader perspective on how technology is changing auditing. Alles, Kogan, and Vasarhelyi (2002) questioned whether there was an economic demand for continuously provided assurance and suggested that the more likely outcome is audit on demand. Alles, Brennan, Kogan, and Vasarhelyi (2006) expanded the scope of the continuous audit by dividing it into continuous control monitoring (CCM) and continuous data assurance (CDA). It has also been shown that many internal audit procedures can be automated, thus saving costs, allowing for more frequent audits and freeing up the audit staff for tasks that require human judgment (Vasarhelyi, 1983, Vasarhelyi, 1985; Alles, Kogan, and Vasarhelyi, 2002).
In the last decade of the 20th century, many large companies, prompted in part by the Y2K concern, replaced their legacy IT systems with new enterprise resource planning (ERP) systems. These ERP systems are controlled by extensive control settings while data is organized into relational databases that are composed of complex, multi-dimensional tables that are “related” to each other for the creation of reports by common fields. Users, for highly justifiable business reasons, are allowed to override control settings. Consequently, new assurance needs have emerged due to the ever increasing difficulty of direct observation of (1) control structures, (2) control compliance, and (3) data.
Control Structure
The ubiquitous usage of ERPs diminished concerns with the adequacy of control structures as the systems are typically based on best of class implementation and widely used even though each company will determine how the ERP control structure will be adopted for company-specific circumstances. Many questions remain, as the actual control structure does not only involve the ERP systems but also the entire manual and IT set of processes (that include many elements aside from the ERP systems) and their integration. Controls can be overridden or bypassed by the users, or may not exist at the upstream of the process, and transactions will be received as legitimate.
Control Compliance
Control compliance, on the other hand, became a much larger problem as established flexible and widely applicable control structures often entail a very large number of controls and for operational reasons these controls may have to be temporarily re-parameterized. For example, a particular checking account may be allowed to go over its credit limit for operational reasons. The need to monitor and assure control settings and the nature of overrides generated a new type of audit objective and process.
Data
Data is in general stored in ERPs, in files for legacy systems, or in more recent times in large repositories external to the organization that are called big data (Vasarhelyi, Kogan, and Tuttle; 2015). The access to these data for observation, monitoring, or mass retrieval requires the auditor’s knowledge and extensive use of software tools. This access is not only technically challenging but also organizationally difficult (Vasarhelyi, Romero, Kuenkaikaew, and Littley; 2012).
1.2. Conceptualizing Various Elements of CA
Table 1-1 illustrates the uses, purposes, and approach of the expanded model of continuous assurance differentiating between internal and external usage and further differentiating between diagnostic, predictive, and historic usage.
Table 1-1: Users, Purpose, and Approach of the Elements of Continuous Assurance.
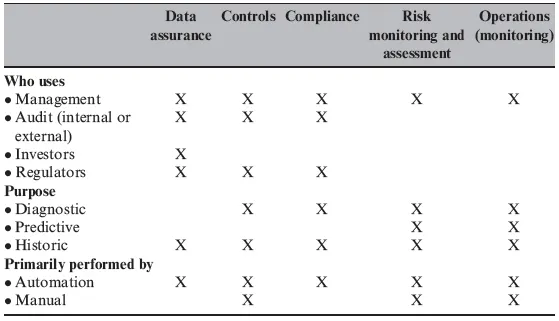
Each of these elements is discussed in the following sections.
Continuous assurance (CA) has the potential to benefit a wide variety of users. Management will be interested in all aspects, from data assurance to monitoring operations. Investors may primarily be interested in data assurance though, depending on the industry, compliance and risk monitoring may be equally as important.
CA is well suited for historic analyses, particularly given the speed with which CA provides information on attributes such as accuracy. Auditors that provide assurance on historic information will likely be primarily interested in the ability of CA to be used for such purpose. Access to sophisticated ERPs and complex data sets create an opportunity for CA to be used for diagnostic purposes. Where an error or anomaly has been identified, CA may perform a retrospective diagnostic of the situation—providing insight and analyses to management. Diagnostically, CA could also be tied to effectively assessing operational and structural strengths and weaknesses of an organization—enabling strategic decisions to be made in a timely manner and with sufficient context.
Automation is an essential element to CA, though manual involvement remains important particularly in situations where extensive judgment is required and where anomalies, exceptions, and outliers are identified.
Continuous Data Audit CDA
Vasarhelyi and Halper called the process of monitoring and constantly assuring AT&T’s RCAM system continuous audit. The architecture of the system described in figure 1-1 shows data being (1) extracted from pre-existing reports, (2) sent to the business units through the remote job entry network, (3) transferred to an email system, and (4) extracted through individual text mining programs. This technique, analogous to what is called today “screen scrapping,” was chosen to avoid interference in the long and complex system process development protocol. All information was collected from existing reports and placed in a relational database. This database drove hypertext graphs that were given to auditors to interact with the system. The several layers of the RCAM system were represented as flowcharts respecting the internal auditors’ documentation practices and experience in data analysis. Many of the analytics impounded into the system were drawn from knowledge engineering (Halper, Snively, and Vasarhelyi, 1989) internal auditors and capturing the calculations they made with paper reports. The formalization of these processes allowed for their repetition at repeated frequency, and often reliance on these tests up to the moment that alerts were generated. Although internal auditors started relying on these exception reports, they also requested that the source reports be retained mainly for their traditional audit reports.
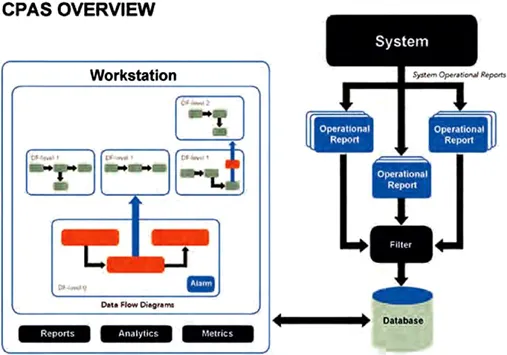
Figure 1-1: CPAS as Continuous Data Audit (from Vasarhelyi & Halper, 1991).
Although the idea of a continuous audit was conceptualized initially as a data monitoring and exception system (Vasarhel...
Table of contents
- Cover
- Title Page
- Introduction
- Continuous Auditing—A New View
- The Development and Intellectual Structure of Continuous Auditing Research1
- The Continuous Audit of Online Systems
- Continuous Auditing of Database Applications: An Embedded Audit Module Approach
- Continuous Online Auditing: A Program of Research
- Feasibility and Economics of Continuous Assurance
- Continuous Auditing: Building Automated Auditing Capability
- Principles of Analytic Monitoring for Continuous Assurance
- Continuous Monitoring of Business Process Controls: A Pilot Implementation of a Continuous Auditing System at Siemens
- Putting Continuous Auditing Theory into Practice: Lessons from Two Pilot Implementations
- Innovation and Practice of Continuous Auditing
- Evolution of Auditing: From the Traditional Approach to the Future Audit
- An Audit Ecosystem to Support Blockchain-based Accounting and Assurance
- New Perspective: Data Analytics as a Precursor to Audit Automation
- Conclusion
- Appendix: Continuous Auditing Research Directory: 1983–2011
- About the Editors
- Index
Frequently asked questions
Yes, you can cancel anytime from the Subscription tab in your account settings on the Perlego website. Your subscription will stay active until the end of your current billing period. Learn how to cancel your subscription
No, books cannot be downloaded as external files, such as PDFs, for use outside of Perlego. However, you can download books within the Perlego app for offline reading on mobile or tablet. Learn how to download books offline
Perlego offers two plans: Essential and Complete
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
We are an online textbook subscription service, where you can get access to an entire online library for less than the price of a single book per month. With over 1 million books across 990+ topics, we’ve got you covered! Learn about our mission
Look out for the read-aloud symbol on your next book to see if you can listen to it. The read-aloud tool reads text aloud for you, highlighting the text as it is being read. You can pause it, speed it up and slow it down. Learn more about Read Aloud
Yes! You can use the Perlego app on both iOS and Android devices to read anytime, anywhere — even offline. Perfect for commutes or when you’re on the go.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app
Yes, you can access Continuous Auditing by David Y. Chan, Victoria Chiu, Miklos A. Vasarhelyi, David Y. Chan,Victoria Chiu,Miklos A. Vasarhelyi in PDF and/or ePUB format, as well as other popular books in Business & Accounting. We have over one million books available in our catalogue for you to explore.