
Practical Linux Security Cookbook
Secure your Linux environment from modern-day attacks with practical recipes, 2nd Edition
- 482 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Practical Linux Security Cookbook
Secure your Linux environment from modern-day attacks with practical recipes, 2nd Edition
About this book
Enhance file system security and learn about network attack, security tools and different versions of Linux build.
Key Features
- Hands-on recipes to create and administer a secure Linux system
- Enhance file system security and local and remote user authentication
- Use various security tools and different versions of Linux for different tasks
Book Description
Over the last few years, system security has gained a lot of momentum and software professionals are focusing heavily on it. Linux is often treated as a highly secure operating system. However, the reality is that Linux has its share of security flaws, and these security flaws allow attackers to get into your system and modify or even destroy your important data. But there's no need to panic, since there are various mechanisms by which these flaws can be removed, and this book will help you learn about different types of Linux security to create a more secure Linux system.
With a step-by-step recipe approach, the book starts by introducing you to various threats to Linux systems. Then, this book will walk you through customizing the Linux kernel and securing local files. Next, you will move on to managing user authentication both locally and remotely and mitigating network attacks. Later, you will learn about application security and kernel vulnerabilities. You will also learn about patching Bash vulnerability, packet filtering, handling incidents, and monitoring system logs. Finally, you will learn about auditing using system services and performing vulnerability scanning on Linux.
By the end of this book, you will be able to secure your Linux systems and create a robust environment.
What you will learn
- Learn about vulnerabilities and exploits in relation to Linux systems
- Configure and build a secure kernel and test it
- Learn about file permissions and how to securely modify files
- Authenticate users remotely and securely copy files on remote systems
- Review different network security methods and tools
- Perform vulnerability scanning on Linux machines using tools
- Learn about malware scanning and read through logs
Who this book is for
This book is intended for all those Linux users who already have knowledge of Linux file systems and administration. You should be familiar with basic Linux commands. Understanding information security and its risks to a Linux system is also helpful in understanding the recipes more easily.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Security Tools
- Linux sXID
- Port Sentry
- Using Squid Proxy
- Open SSL Server
- Trip Wire
- Shorewall
- OSSEC
- Snort
- Rsync and Grsync—backup tool
Linux sXID
Getting ready
apt-get install sxid
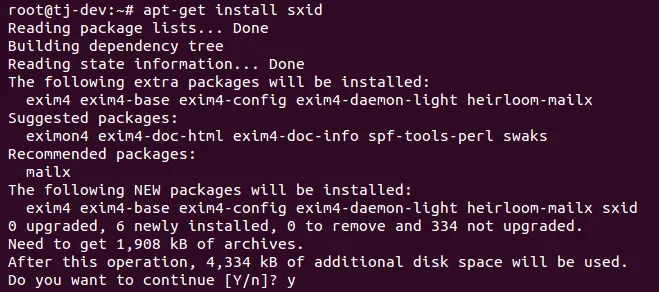
How to do it...
- Once the installation completes, we start editing the /etc/sxid.conf file to use the tool as we require. Open the file in the editor of your choice:
nano /etc/sxid.conf
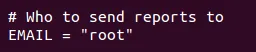
- In the configuration file, look for the following line:
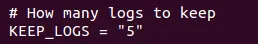
- Next, look for the line that reads KEEP_LOGS and change the value to a numerical value of your choice. This number defines how many log files to keep:
- If you wish to get the logs even when sXid finds no changes, then change the value for ALWAYS_NOTIFY to yes:

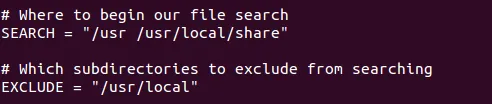
- We can define a list of directories, separated with spaces, for the SEARCH option, for sXID to use as a starting point for its search. However, if we wish to exclude any directory from the search, we can specify it under the EXCLUDE option:
- There are many more options in /etc/sxid.conf, which can be configured as per our requirements. Once we are done with editing the file, save and close the file.
- Now, if we want to run sxid manually for spot-checking, we use the following command:
sxid -c /etc/sxid.conf -k
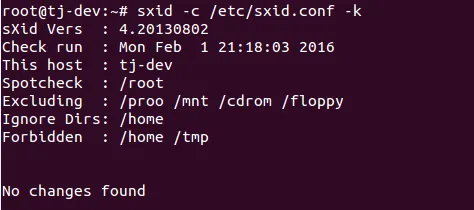
How it works...
Port Sentry
Getting ready
Table of contents
- Title Page
- Copyright and Credits
- Contributors
- Packt Upsell
- Preface
- Linux Security Problem
- Configuring a Secure and Optimized Kernel
- Local Filesystem Security
- Local Authentication in Linux
- Remote Authentication
- Network Security
- Security Tools
- Linux Security Distros
- Bash Vulnerability Patching
- Security Monitoring and Logging
- Understanding Linux Service Security
- Scanning and Auditing Linux
- Vulnerability Scanning and Intrusion Detection
- Other Books You May Enjoy
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app