
Kali Linux Web Penetration Testing Cookbook
Identify, exploit, and prevent web application vulnerabilities with Kali Linux 2018.x, 2nd Edition
- 404 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Kali Linux Web Penetration Testing Cookbook
Identify, exploit, and prevent web application vulnerabilities with Kali Linux 2018.x, 2nd Edition
About this book
Discover the most common web vulnerabilities and prevent them from becoming a threat to your site's security
Key Features
- Familiarize yourself with the most common web vulnerabilities
- Conduct a preliminary assessment of attack surfaces and run exploits in your lab
- Explore new tools in the Kali Linux ecosystem for web penetration testing
Book Description
Web applications are a huge point of attack for malicious hackers and a critical area for security professionals and penetration testers to lock down and secure. Kali Linux is a Linux-based penetration testing platform that provides a broad array of testing tools, many of which can be used to execute web penetration testing.
Kali Linux Web Penetration Testing Cookbook gives you the skills you need to cover every stage of a penetration test – from gathering information about the system and application, to identifying vulnerabilities through manual testing. You will also cover the use of vulnerability scanners and look at basic and advanced exploitation techniques that may lead to a full system compromise. You will start by setting up a testing laboratory, exploring the latest features of tools included in Kali Linux and performing a wide range of tasks with OWASP ZAP, Burp Suite and other web proxies and security testing tools.
As you make your way through the book, you will learn how to use automated scanners to find security flaws in web applications and understand how to bypass basic security controls. In the concluding chapters, you will look at what you have learned in the context of the Open Web Application Security Project (OWASP) and the top 10 web application vulnerabilities you are most likely to encounter, equipping you with the ability to combat them effectively.
By the end of this book, you will have acquired the skills you need to identify, exploit, and prevent web application vulnerabilities.
What you will learn
- Set up a secure penetration testing laboratory
- Use proxies, crawlers, and spiders to investigate an entire website
- Identify cross-site scripting and client-side vulnerabilities
- Exploit vulnerabilities that allow the insertion of code into web applications
- Exploit vulnerabilities that require complex setups
- Improve testing efficiency using automated vulnerability scanners
- Learn how to circumvent security controls put in place to prevent attacks
Who this book is for
Kali Linux Web Penetration Testing Cookbook is for IT professionals, web developers, security enthusiasts, and security professionals who want an accessible reference on how to find, exploit, and prevent security vulnerabilities in web applications. The basics of operating a Linux environment and prior exposure to security technologies and tools are necessary.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Testing Authentication and Session Management
- Username enumeration
- Dictionary attack on login pages with Burp Suite
- Brute forcing basic authentication with Hydra
- Attacking Tomcat's passwords with Metasploit
- Manually identifying vulnerabilities in cookies
- Attacking a session fixation vulnerability
- Evaluating a session identifier's quality with Burp Sequencer
- Abusing insecure direct object references
- Performing a Cross-Site Request Forgery attack
Introduction
Username enumeration
Getting ready
How to do it...
- From Kali Linux, browse to WebGoat (http://192.168.56.11/WebGoat/attack), and, if a login dialog pops up, use webgoat as both the username and password.
- Once in WebGoat, go to Authentication Flaws | Forgot Password. If we submit any random username and that user does not exist in the database, we will receive a message saying that the username is not valid:
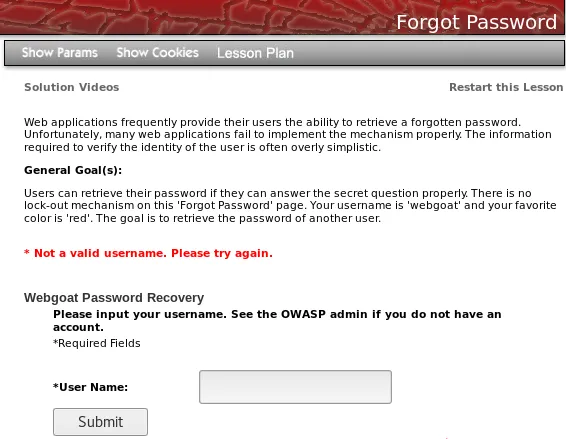
- We can then assume that the response will be different when a valid username is provided. To test this, send the request to Intruder. In Burp's history, it should be a POST request to http://192.168.56.11/WebGoat/attack?Screen=64&menu=500.
- Once in Intruder, leave the username as the only insertion position:

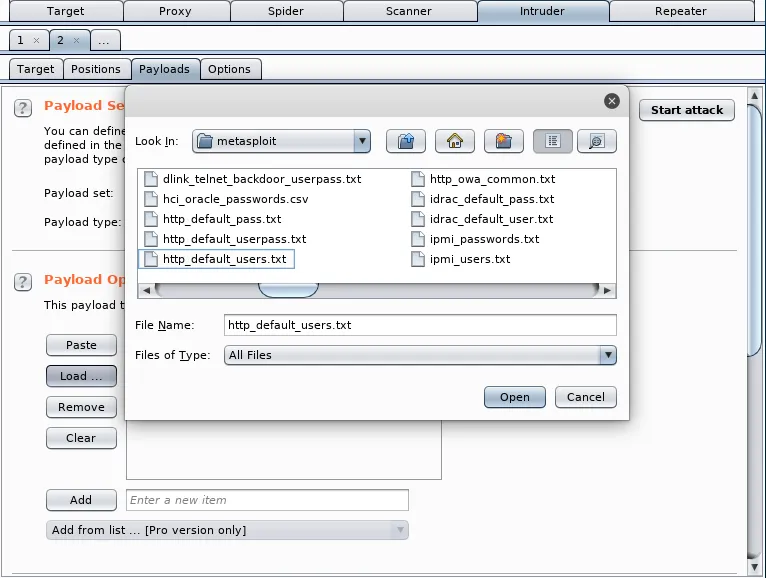
- Then, go to Payloads to set the list of users we will use in the attack. Leave the type as Simple List and click on the Load button to load the /usr/share/wordlists/metasploit/http_default_users.txt file:
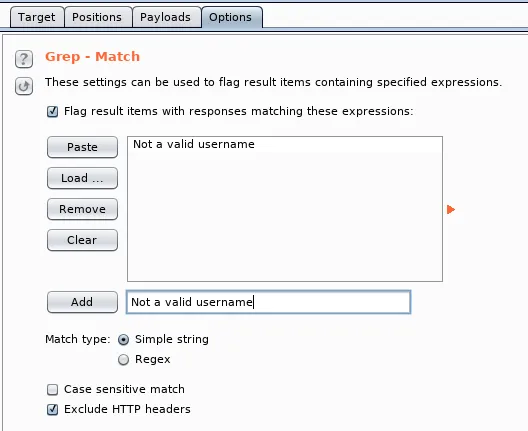
- Now that we know the message when a user doesn't exist, we can use Burp to tell us when that message appears in the results. Go to Options | Grep - Match and clear the list.
- Add a new string to match Not a valid username:
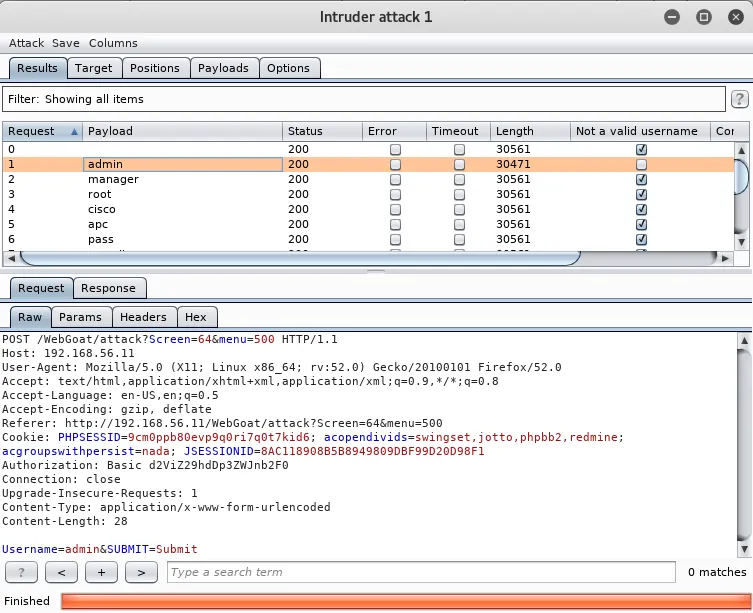
- Now, start the attack. Notice how there are some names, such as admin, in which the message of an invalid username is not marked by Burp Suite; those are the ones that are valid names within the application:
How it works...
Dictionary attack on login pages with Burp Suite
How to do it...
- First, we set up Burp Suite as a proxy to our browser.
- Browse to http://192.168.56.102/WackoPicko/admin/index.php?page=login.
- We will see a login form. Let's try test for both username and password.
- Now, go to Proxy's history and look for the POST request we just made with the login attempt and send it to Intruder.
- Click on Clear § to clear the pre-selected insertion positions.
- Now, we add insertion positions on the values of the two POST parameters (adminname and password) by highlighting the value of the parameter and clicking Add §:
- As we want our list of...
Table of contents
- Title Page
- Copyright and Credits
- Packt Upsell
- Contributors
- Preface
- Setting Up Kali Linux and the Testing Lab
- Reconnaissance
- Using Proxies, Crawlers, and Spiders
- Testing Authentication and Session Management
- Cross-Site Scripting and Client-Side Attacks
- Exploiting Injection Vulnerabilities
- Exploiting Platform Vulnerabilities
- Using Automated Scanners
- Bypassing Basic Security Controls
- Mitigation of OWASP Top 10 Vulnerabilities
- Other Books You May Enjoy
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app