
Kali Linux 2018: Windows Penetration Testing
Conduct network testing, surveillance, and pen testing on MS Windows using Kali Linux 2018, 2nd Edition
- 404 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Kali Linux 2018: Windows Penetration Testing
Conduct network testing, surveillance, and pen testing on MS Windows using Kali Linux 2018, 2nd Edition
About This Book
Become the ethical hacker you need to be to protect your network
Key Features
- Set up, configure, and run a newly installed Kali-Linux 2018.x
- Footprint, monitor, and audit your network and investigate any ongoing infestations
- Customize Kali Linux with this professional guide so it becomes your pen testing toolkit
Book Description
Microsoft Windows is one of the two most common OSes, and managing its security has spawned the discipline of IT security. Kali Linux is the premier platform for testing and maintaining Windows security. Kali is built on the Debian distribution of Linux and shares the legendary stability of that OS. This lets you focus on using the network penetration, password cracking, and forensics tools, and not the OS.
This book has the most advanced tools and techniques to reproduce the methods used by sophisticated hackers to make you an expert in Kali Linux penetration testing. You will start by learning about the various desktop environments that now come with Kali. The book covers network sniffers and analysis tools to uncover the Windows protocols in use on the network. You will see several tools designed to improve your average in password acquisition, from hash cracking, online attacks, offline attacks, and rainbow tables to social engineering. It also demonstrates several use cases for Kali Linux tools like Social Engineering Toolkit, and Metasploit, to exploit Windows vulnerabilities.
Finally, you will learn how to gain full system-level access to your compromised system and then maintain that access. By the end of this book, you will be able to quickly pen test your system and network using easy-to-follow instructions and support images.
What you will learn
- Learn advanced set up techniques for Kali and the Linux operating system
- Understand footprinting and reconnaissance of networks
- Discover new advances and improvements to the Kali operating system
- Map and enumerate your Windows network
- Exploit several common Windows network vulnerabilities
- Attack and defeat password schemes on Windows
- Debug and reverse engineer Windows programs
- Recover lost files, investigate successful hacks, and discover hidden data
Who this book is for
If you are a working ethical hacker who is looking to expand the offensive skillset with a thorough understanding of Kali Linux, then this is the book for you. Prior knowledge about Linux operating systems, BASH terminal, and Windows command line would be highly beneficial.
Frequently asked questions
Information
Maintaining Access on Server or Desktop
- Maintaining access, or ET Phone Home
- Maintaining access with Ncat
- The Drop Box
- Cracking the Network Access Controller (NAC)
- Creating a spear-phishing attack with the Social Engineering Toolkit
- Using Backdoor Factory to evade antivirus
Maintaining access or ET Phone Home
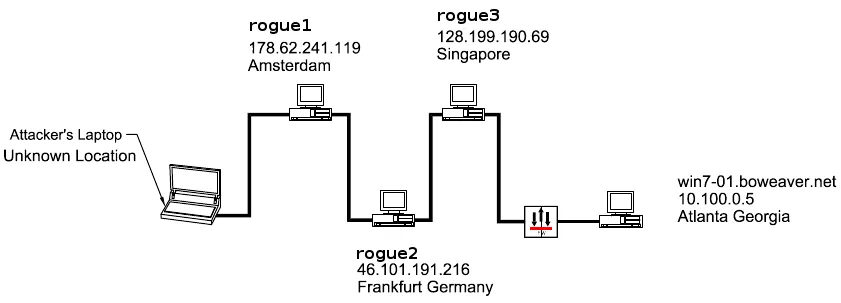
whois 178.62.241.119 inetnum: 178.62.128.0 - 178.62.255.255 netname: DIGITALOCEAN-AMS-5 descr: DigitalOcean Amsterdam country: NL admin-c: BU332-RIPE tech-c: BU332-RIPE status: ASSIGNED PA mnt-by: digitalocean mnt-lower: digitalocean mnt-routes: digitalocean created: 2014-05-01T16:43:59Z last-modified: 2014-05-01T16:43:59Z source: RIPE # Filtered
A good investigator, seeing this information, would just subpoena DigitalOcean to find out who was renting that IP when the victim phoned home, but it could just as likely be a machine belonging to a little old lady in Leningrad. The infrastructure of a botnet is developed from a group of compromised boxes. This chapter describes a small do-it-yourself botnet.
whois 46.101.191.216 inetnum: 46.101.128.0 - 46.101.255.255 netname: EU-DIGITALOCEAN-DE1 descr: Digital Ocean, Inc. country: DE org: ORG-DOI2-RIPE admin-c: BU332-RIPE...
Table of contents
- Title Page
- Copyright and Credits
- Packt Upsell
- Contributors
- Preface
- Choosing Your Distro
- Sharpening the Saw
- Information Gathering and Vulnerability Assessments
- Sniffing and Spoofing
- Password Attacks
- NetBIOS Name Service and LLMNR - Obsolete but Still Deadly
- Gaining Access
- Windows Privilege Escalation and Maintaining Access
- Maintaining Access on Server or Desktop
- Reverse Engineering and Stress Testing
- Other Books You May Enjoy