
- 460 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Integer Algorithms In Cryptology And Information Assurance
About this book
Integer Algorithms in Cryptology and Information Assurance is a collection of the author's own innovative approaches in algorithms and protocols for secret and reliable communication. It concentrates on the “ what ” and “ how ” behind implementing the proposed cryptographic algorithms rather than on formal proofs of “why” these algorithms work.
The book consists of five parts (in 28 chapters) and describes the author's research results in:
-->
- Innovative methods in cryptography (secret communication between initiated parties);
- Cryptanalysis (how to break the encryption algorithms based on computational complexity of integer factorization and discrete logarithm problems);
- How to provide a reliable transmission of information via unreliable communication channels and;
- How to exploit a synergetic effect that stems from combining the cryptographic and information assurance protocols.
-->
This text contains innovative cryptographic algorithms; computationally efficient algorithms for information assurance; new methods to solve the classical problem of integer factorization, which plays a key role in cryptanalysis; and numerous illustrative examples and tables that facilitate the understanding of the proposed algorithms.
The fundamental ideas contained within are not based on temporary advances in technology, which might become obsolete in several years. The problems addressed in the book have their own intrinsic computational complexities, and the ideas and methods described in the book will remain important for years to come.
Contents:
- Introductory Notes on Security and Reliability
- Enhanced Algorithm for Modular Multiplicative Inverse
- Multiplication of Large-Integers Based on Homogeneous Polynomials
- Deterministic Algorithms for Primitive Roots and Cyclic Groups with Mutual Generators
- Primality Testing via Complex Integers and Pythagorean Triplets
- Algorithm Generating Random Permutation
- Extractability of Square Roots and Divisibility Tests
- Extraction of Roots of Higher Order in Modular Arithmetic
- Public-Key Cryptography Based on Square Roots and Complex Modulus
- Cubic Roots of Complex Integers and Encryption with Digital Isotopes
- Exponentiation-Free Accelerated Encryption/Decryption Protocol
- Cryptocol Based on Three-Dimensional Elliptic Surface
- Multi-Parametric Cryptography for Rapid Transmission of Information
- Scheme for Digital Signature that Always Works
- Hybrid Cryptographic Protocols Providing Digital Signature
- Control Protocols Providing Information Assurance
- Information Assurance Based on Cubic Roots of Integers
- Simultaneous Information Assurance and Encryption Based on Quintic Roots
- Modular Equations and Integer Factorization
- Counting Points on Hyper-Elliptic Curves and Integer Factorization
- Integer Factorization via Constrained Discrete Logarithm Problem
- Decomposability of Discrete Logarithm Problems
- Detecting Intervals and Order of Point on Elliptic Curve
- Generalization of Gauss Theorem and Computation of Complex Primes
- Space Complexity of Algorithm for Modular Multiplicative Inverse
- New Algorithm Can Be Computed
- Search for Period of Odd Function
- Optimized Search for Maximum of Function on Large Intervals
- Topological Design of Satellite Communication Networks
Readership: Integer Algorithms in Cryptology and Information Assurance would be a book of interest for researchers and developers working on telecommunication security and/or reliability, in industries such as business and banking, national security agencies, militaries, interplanetary space exploration, and telemedicine. Faculty members in Computer Science, Electrical Engineering, Information Technology, Bio-Engineering and Applied Mathematics Departments, who are planning to teach advanced courses in cryptography; graduate and PhD students; advanced undergraduate students of the same fields; and various national cryptographic societies would also find this book useful.
Key Features:
- Innovative cryptographic algorithms
- Computationally efficient algorithms for information assurance
- New methods to solve the classical problem of integer factorization, which plays a key role in cryptanalysis
- Numerous illustrative examples and tables that facilitate understanding of the proposed algorithms
- The style of the book, which concentrates on constructive description of wha t and how to implement the proposed cryptographic algorithms rather than on formal proofs of why these algorithms work
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Enhanced Algorithm for Modular Multiplicative Inverse
1. Introduction: Division of Two Integers

2. Basic Arrays and their Properties
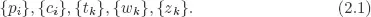
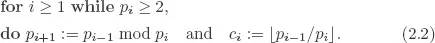
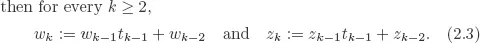
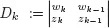

Table of contents
- Cover Page
- Title Page
- Copyright Page
- About the Author
- Dedication
- Preface
- Acknowledgments
- Contents
- 0. Introductory Notes on Security and Reliability
- 1. Enhanced Algorithm for Modular Multiplicative Inverse
- 2. Multiplication of Large-Integers Based on Homogeneous Polynomials
- 3. Deterministic Algorithms for Primitive Roots and Cyclic Groups with Mutual Generators
- 4. Primality Testing via Complex Integers and Pythagorean Triplets
- 5. Algorithm Generating Random Permutation
- 6. Extractability of Square Roots and Divisibility Tests
- 7. Extraction of Roots of Higher Order in Modular Arithmetic
- 8. Public-Key Cryptography Based on Square Roots and Complex Modulus
- 9. Cubic Roots of Complex Integers and Encryption with Digital Isotopes
- 10. Exponentiation-Free Accelerated Encryption/ Decryption Protocol
- 11. Cryptocol Based on Three-Dimensional Elliptic Surface
- 12. Multi-Parametric Cryptography for Rapid Transmission of Information
- 13. Scheme for Digital Signature that Always Works
- 14. Hybrid Cryptographic Protocols Providing Digital Signature
- 15. Control Protocols Providing Information Assurance
- 16. Information Assurance Based on Cubic Roots of Integers
- 17. Simultaneous Information Assurance and Encryption Based on Quintic Roots
- 18. Modular Equations and Integer Factorization
- 19. Counting Points on Hyper-Elliptic Curves and Integer Factorization
- 20. Integer Factorization via Constrained Discrete Logarithm Problem
- 21. Decomposability of Discrete Logarithm Problems
- 22. Detecting Intervals and Order of Point on Elliptic Curve
- 23. Generalization of Gauss Theorem and Computation of Complex Primes
- 24. Space Complexity of Algorithm for Modular Multiplicative Inverse
- 25. New Algorithm Can Be Computed
- 26. Search for Period of Odd Function
- 27. Optimized Search for Maximum of Function on Large Intervals
- 28. Topological Design of Satellite Communication Networks
- References
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app