
Hands-On Penetration Testing with Kali NetHunter
Spy on and protect vulnerable ecosystems using the power of Kali Linux for pentesting on the go
- 302 pages
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Hands-On Penetration Testing with Kali NetHunter
Spy on and protect vulnerable ecosystems using the power of Kali Linux for pentesting on the go
About This Book
Convert Android to a powerful pentesting platform.
Key Features
- Get up and running with Kali Linux NetHunter
- Connect your Android device and gain full control over Windows, OSX, or Linux devices
- Crack Wi-Fi passwords and gain access to devices connected over the same network collecting intellectual data
Book Description
Kali NetHunter is a version of the popular and powerful Kali Linux pentesting platform, designed to be installed on mobile devices. Hands-On Penetration Testing with Kali NetHunter will teach you the components of NetHunter and how to install the software. You'll also learn about the different tools included and how to optimize and use a package, obtain desired results, perform tests, and make your environment more secure.
Starting with an introduction to Kali NetHunter, you will delve into different phases of the pentesting process. This book will show you how to build your penetration testing environment and set up your lab. You will gain insight into gathering intellectual data, exploiting vulnerable areas, and gaining control over target systems. As you progress through the book, you will explore the NetHunter tools available for exploiting wired and wireless devices. You will work through new ways to deploy existing tools designed to reduce the chances of detection. In the concluding chapters, you will discover tips and best practices for integrating security hardening into your Android ecosystem.
By the end of this book, you will have learned to successfully use a mobile penetration testing device based on Kali NetHunter and Android to accomplish the same tasks you would traditionally, but in a smaller and more mobile form factor.
What you will learn
- Choose and configure a hardware device to use Kali NetHunter
- Use various tools during pentests
- Understand NetHunter suite components
- Discover tips to effectively use a compact mobile platform
- Create your own Kali NetHunter-enabled device and configure it for optimal results
- Learn to scan and gather information from a target
- Explore hardware adapters for testing and auditing wireless networks and Bluetooth devices
Who this book is for
Hands-On Penetration Testing with Kali NetHunter is for pentesters, ethical hackers, and security professionals who want to learn to use Kali NetHunter for complete mobile penetration testing and are interested in venturing into the mobile domain. Some prior understanding of networking assessment and Kali Linux will be helpful.
Frequently asked questions
Information
Section 1: Exploring Kali NetHunter
- Chapter 1, Introducing Kali NetHunter
- Chapter 2, Understanding the Phases of the Pentesting Process
Introduction to Kali NetHunter
- Introducing Kali NetHunter
- The Android platform and Security model
- Installing Kali NetHunter
What is Kali NetHunter?
- Metasploit: A famous exploit development framework created by Rapid7 (www.rapid7.com).
- SAINT: A renowned vulnerability-assessment tool developed by SAINT Corporation (www.saintcorporation.com).
- Maltego: An information-gathering tool created by Paterva (www.paterva.com), which takes advantage of data-mining techniques using various resources on the internet.
Tools within Kali NetHunter
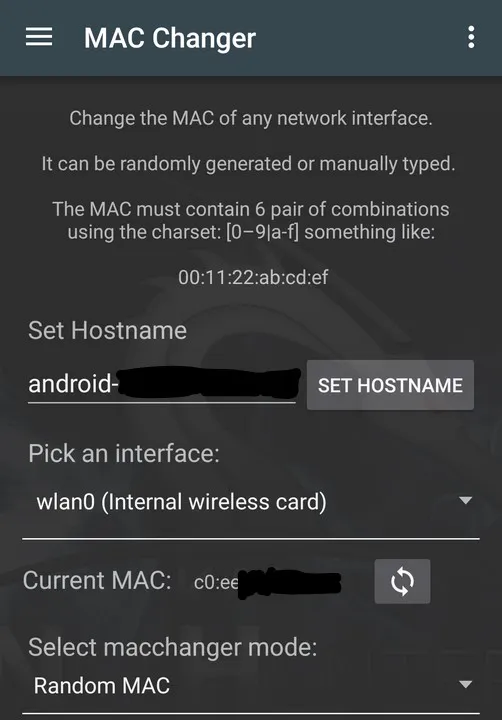
MAC Changer
The MITM framework
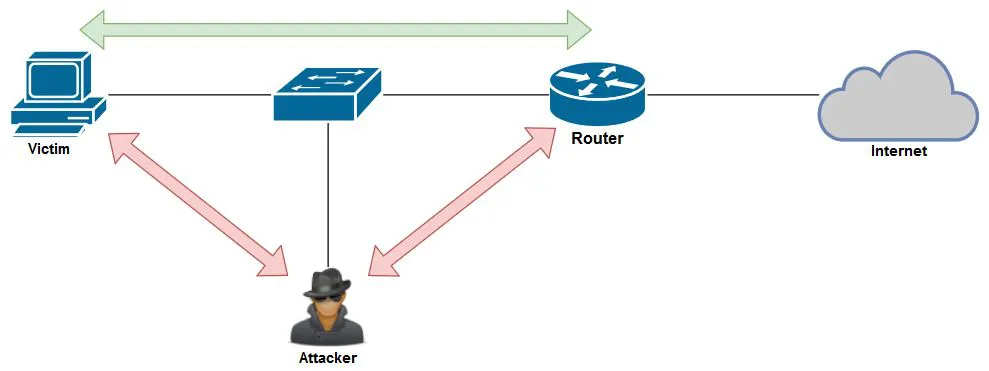
Table of contents
- Title Page
- Copyright and Credits
- About Packt
- Contributors
- Preface
- Section 1: Exploring Kali NetHunter
- Introduction to Kali NetHunter
- Understanding the Phases of the Pentesting Process
- Section 2: Common Pentesting Tasks and Tools
- Intelligence-Gathering Tools
- Scanning and Enumeration Tools
- Penetrating the Target
- Clearing Tracks and Removing Evidence from a Target
- Section 3: Advanced Pentesting Tasks and Tools
- Packet Sniffing and Traffic Analysis
- Targeting Wireless Devices and Networks
- Avoiding Detection
- Hardening Techniques and Countermeasures
- Building a Lab
- Selecting a Kali Device and Hardware
- Other Books You May Enjoy