
- English
- ePUB (mobile friendly)
- Available on iOS & Android
About this book
Build a better defense against motivated, organized, professional attacks
Advanced Penetration Testing: Hacking the World's Most Secure Networks takes hacking far beyond Kali linux and Metasploit to provide a more complex attack simulation. Featuring techniques not taught in any certification prep or covered by common defensive scanners, this book integrates social engineering, programming, and vulnerability exploits into a multidisciplinary approach for targeting and compromising high security environments. From discovering and creating attack vectors, and moving unseen through a target enterprise, to establishing command and exfiltrating data—even from organizations without a direct Internet connection—this guide contains the crucial techniques that provide a more accurate picture of your system's defense. Custom coding examples use VBA, Windows Scripting Host, C, Java, JavaScript, Flash, and more, with coverage of standard library applications and the use of scanning tools to bypass common defensive measures.
Typical penetration testing consists of low-level hackers attacking a system with a list of known vulnerabilities, and defenders preventing those hacks using an equally well-known list of defensive scans. The professional hackers and nation states on the forefront of today's threats operate at a much more complex level—and this book shows you how to defend your high security network.
- Use targeted social engineering pretexts to create the initial compromise
- Leave a command and control structure in place for long-term access
- Escalate privilege and breach networks, operating systems, and trust structures
- Infiltrate further using harvested credentials while expanding control
Today's threats are organized, professionally-run, and very much for-profit. Financial institutions, health care organizations, law enforcement, government agencies, and other high-value targets need to harden their IT infrastructure and human capital against targeted advanced attacks from motivated professionals. Advanced Penetration Testing goes beyond Kali linux and Metasploit and to provide you advanced pen testing for high security networks.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Chapter 1
Medical Records (In)security
THE “KANE” INCIDENT
http://www.securityfocus.com/news/122 An Introduction to Simulating Advanced Persistent Threat
Background and Mission Briefing
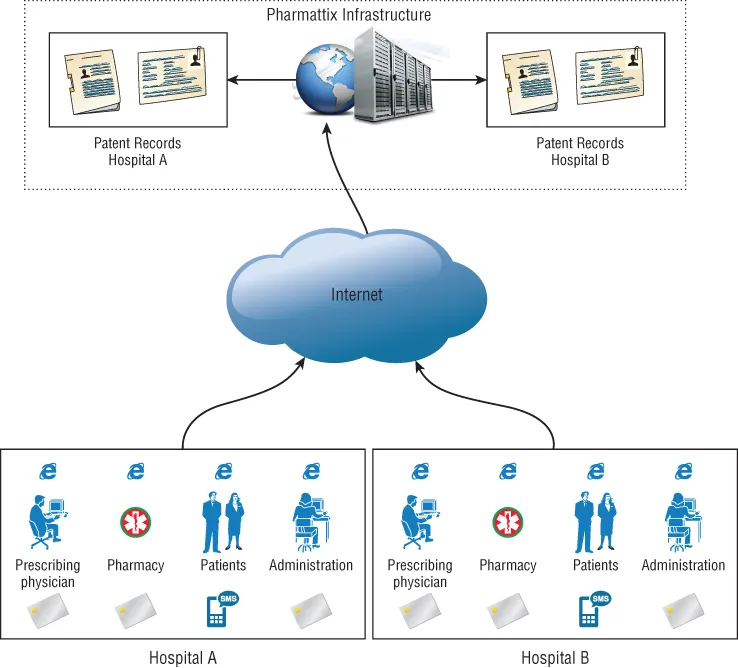
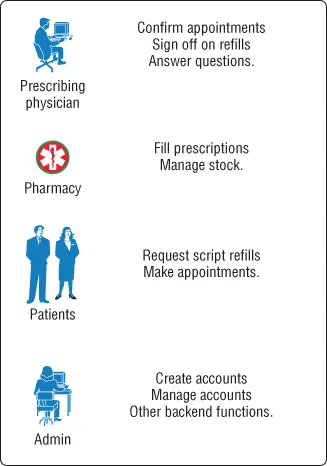
- The MD prescribing the medications
- The pharmacy dispensing the medications
- The patients themselves
- The administrative backend for any other miscellaneous tasks
PHARMATTIX MARKETING MATERIAL
- Own management environment • Individual pages as team route, appointments, etc. • Hours • NHG Patient Leaflets and letters • MS Office integration • Medical information • Passenger and vaccination information • Various forms (registration, repeat prescriptions, questions) • e-consultation • Online web calendar • A link to the website with your GP Information System (HIS) • Free helpdesk support
- E-Consultation and HIS integration: Want to communicate over a secure environment with your patients? Through an e-consultation you can. You can increase the accessibility of your practice without losing control. It is also possible to link your HIS to the practice site, allowing patients to make online appointments and request repeat medication. Without the intervention of the assistant!
WHEN BRUCE SCHNEIER TALKS, IT'S A GOOD IDEA TO LISTEN
Table of contents
- Cover
- Title Page
- Introduction
- Chapter 1: Medical Records (In)security
- Chapter 2: Stealing Research
- Chapter 3: Twenty-First Century Heist
- Chapter 4: Pharma Karma
- Chapter 5: Guns and Ammo
- Chapter 6: Criminal Intelligence
- Chapter 7: War Games
- Chapter 8: Hack Journalists
- Chapter 9: Northern Exposure
- End User License Agreement
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app