
Security, Privacy, and Digital Forensics in the Cloud
- English
- ePUB (mobile friendly)
- Available on iOS & Android
Security, Privacy, and Digital Forensics in the Cloud
About this book
In a unique and systematic way, this book discusses the security and privacy aspects of the cloud, and the relevant cloud forensics.
Cloud computing is an emerging yet revolutionary technology that has been changing the way people live and work. However, with the continuous growth of cloud computing and related services, security and privacy has become a critical issue. Written by some of the top experts in the field, this book specifically discusses security and privacy of the cloud, as well as the digital forensics of cloud data, applications, and services. The first half of the book enables readers to have a comprehensive understanding and background of cloud security, which will help them through the digital investigation guidance and recommendations found in the second half of the book.
Part One of Security, Privacy and Digital Forensics in the Cloud covers cloud infrastructure security; confidentiality of data; access control in cloud IaaS; cloud security and privacy management; hacking and countermeasures; risk management and disaster recovery; auditing and compliance; and security as a service (SaaS). Part Two addresses cloud forensics – model, challenges, and approaches; cyberterrorism in the cloud; digital forensic process and model in the cloud; data acquisition; digital evidence management, presentation, and court preparation; analysis of digital evidence; and forensics as a service (FaaS).
- Thoroughly covers both security and privacy of cloud and digital forensics
- Contributions by top researchers from the U.S., the European and other countries, and professionals active in the field of information and network security, digital and computer forensics, and cloud and big data
- Of interest to those focused upon security and implementation, and incident management
- Logical, well-structured, and organized to facilitate comprehension
Security, Privacy and Digital Forensics in the Cloud is an ideal book for advanced undergraduate and master's-level students in information systems, information technology, computer and network forensics, as well as computer science. It can also serve as a good reference book for security professionals, digital forensics practitioners and cloud service providers.
Tools to learn more effectively

Saving Books

Keyword Search

Annotating Text

Listen to it instead
Information
Part I
Cloud Security and Privacy
1
Introduction to the Cloud and Fundamental Security and Privacy Issues of the Cloud
1.1 Introduction
1.2 Cloud Computing and Security Issues
- Cloud consumer – A person or organization that maintains a business relationship with and uses services offered by cloud providers.
- Cloud provider – A person, organization, or entity responsible for offering various services to cloud consumers.
- Cloud auditor – A party that can conduct independent assessments of cloud services, information system operations, performance, and security of cloud implementations.
- Cloud broker – An entity that manages the use, performance, and delivery of cloud services, and negotiates relationships between cloud providers and cloud consumers.
- Cloud carrier – The intermediary that provides connectivity and transport of cloud services from cloud providers to cloud consumers.
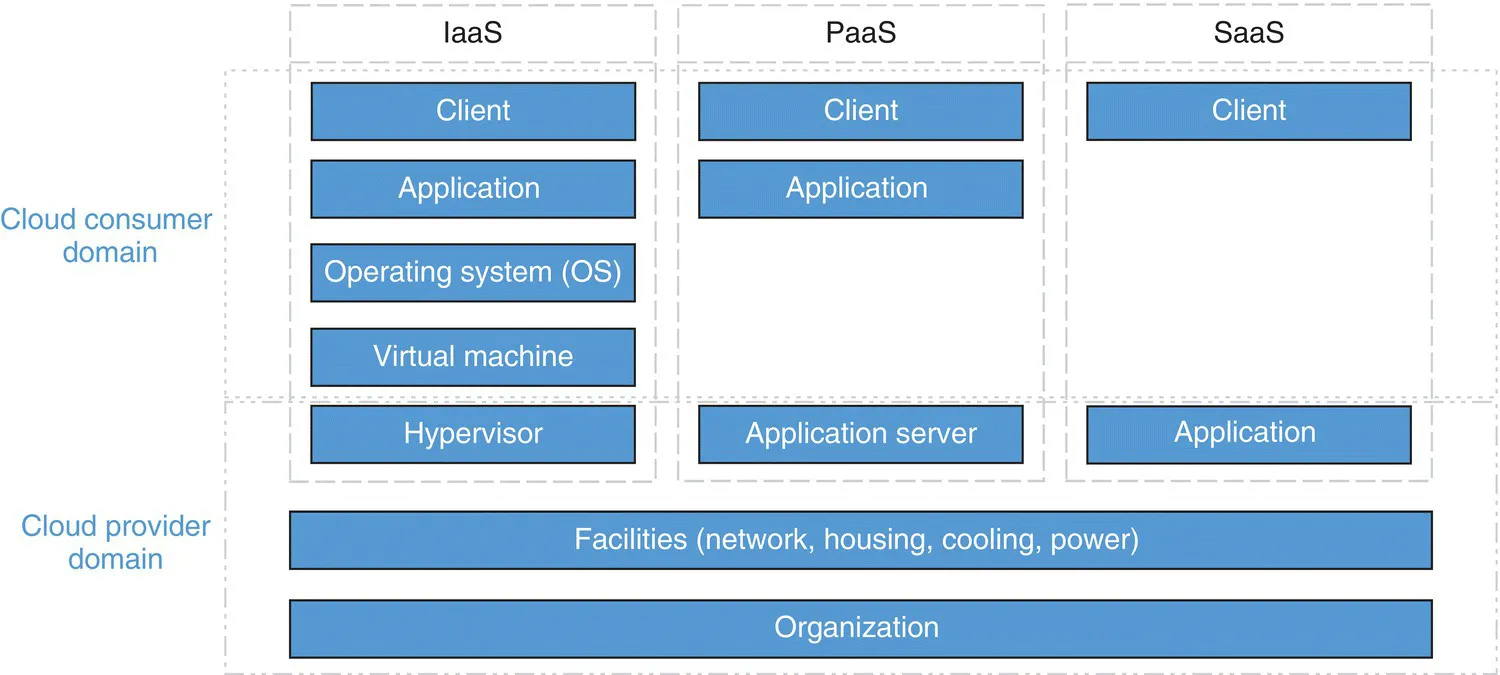
- Infrastructure‐as‐a‐Service – IaaS is the most basic cloud service model, where cloud providers offer servers, storage, and network, typically in the form of virtual appliances. Consumers can deploy and run any software such as operating systems and applications. IaaS providers are responsible for the underlying infrastructure including housing, running, and maintaining these resources, while consumers are responsible for maintaining the operating system and their applications. Amazon Elastic Compute Cloud (EC2, http://aws.amazon.com/ec2)), Eucalyptus (http://www8.hp.com/us/en/cloud/helion‐eucalyptus.html), and OpenNebula (http://opennebula.org) are some examples of IaaS providers.
- Platform‐as‐a‐Service – In PaaS, providers offer environments for developing, deploying, hosting, and testing software applications. Typically, it includes programming languages, databases, libraries, and other development tools. Consumers are not responsible for the underlying infrastructure, operating systems, or storage, but they are responsible for their deployed applications. Examples of PaaS providers include Microsoft Azure (https://azure.microsoft.com/en‐us), Force.com (http://www.force.com), and Google App Engine (https://cloud.google.com/appengine).
- Software‐as‐a‐Service – In SaaS, cloud providers offer applications on demand that are hosted on the Cloud and can be accessed through thin clients. Consumers do not manage or control the underlying infrastructure. Some SaaS applications allow limited user‐specific customization. Examples of SaaS providers include Salesforce.com's Customer Relationship Management (CRM, www.salesforce.com) and FreshBooks (www.freshbooks.com).
- Public cloud – A public cloud is deployed by an organization that offers various services to the general public over the Internet. The infrastructure is owned and managed by the service provider, and it is located in the provider's facilities. Cloud providers are responsible for the installation, management, provisioning, and maintenance of the cloud services. Users' data is stored and processed in the Cloud, which may raise security and privacy issues. It exists on the premises of the cloud provider.
- Private cloud – A private cloud is deployed for a single organization and is dedicated entirely to that organization's internal users. The private cloud resides in the organization's facilities; however, it can be hosted and managed by a third‐party provider. The private cloud can be owned, managed, and operated by the organization, a third party, or some combination of them, and it may exist on or off premises, so that data security and availability can be controlled by each of them.
- Community cloud – A community cloud is deployed for a specific community of consumers from organizations that share common computing concerns. It may be owned, managed, and operated by one or more of the organization's members, a third party, or so...
Table of contents
- Cover
- Table of Contents
- List of Contributors
- Part I: Cloud Security and Privacy
- Part II: Cloud Forensics
- Index
- End User License Agreement
Frequently asked questions
- Essential is ideal for learners and professionals who enjoy exploring a wide range of subjects. Access the Essential Library with 800,000+ trusted titles and best-sellers across business, personal growth, and the humanities. Includes unlimited reading time and Standard Read Aloud voice.
- Complete: Perfect for advanced learners and researchers needing full, unrestricted access. Unlock 1.4M+ books across hundreds of subjects, including academic and specialized titles. The Complete Plan also includes advanced features like Premium Read Aloud and Research Assistant.
Please note we cannot support devices running on iOS 13 and Android 7 or earlier. Learn more about using the app